See Panorays in Action
Speak to one of our experts and learn how Panorays lets you manage third-party cyber risks from one automated platform.
Get a customized one-on-one demo and learn how to:
- Evaluate third party risks with an integrated view of security questionnaires and external cyber assessments.
- Collaborate with third parties to quickly remediate security gaps.
- Monitor and respond to third-party risks with real-time alerts on changes to risk levels and emerging cyber threats.


01 Analysis
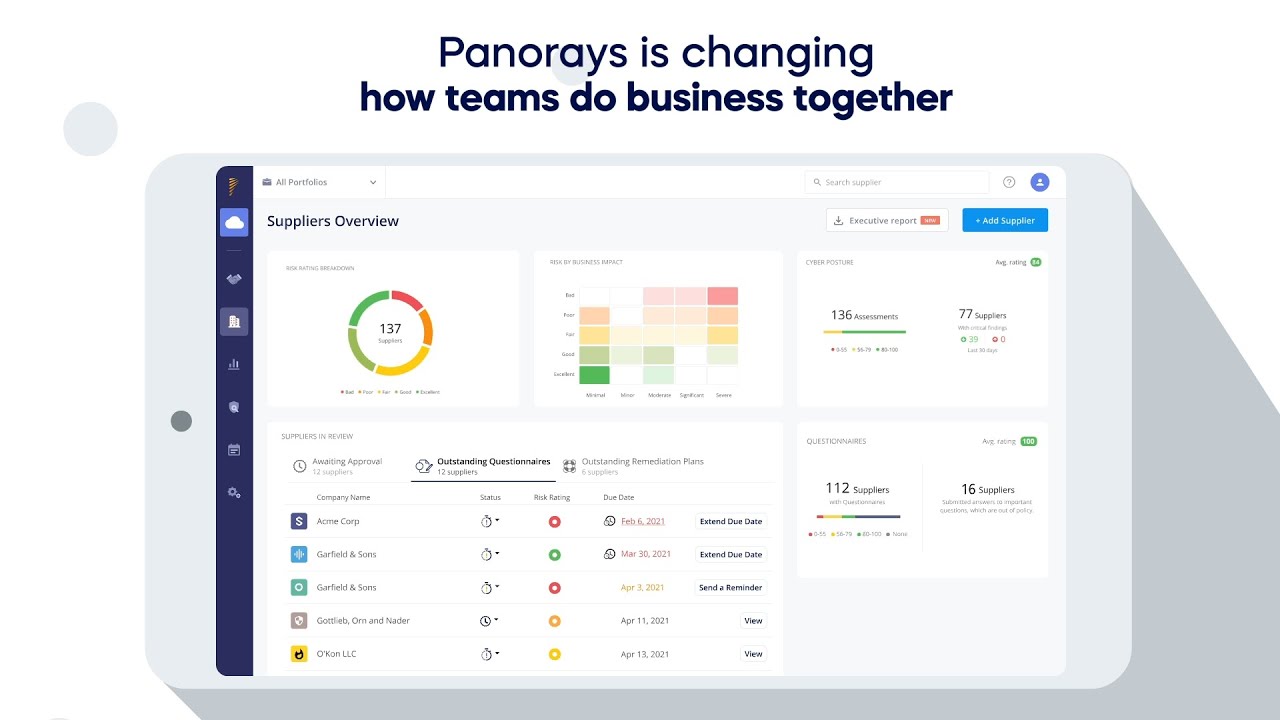
Engagement
Business engagement must be friction-free. The platform enables easy collaboration and rectification of issues. There is no need for out of platform discussion. No emails and no phone calls—just seamless engagement between the organization and third party.
Remediation
You and your suppliers can challenge or validate findings, receive instructions on how to mitigate cyber gaps and report progress.
Approval
Within seconds, you can see which suppliers do not adhere to your company’s security policies.
Monitoring
Your security evaluation is always current. Panorays continuously uncovers and evaluates the supplier, and you receive live alerts about any security changes or breaches to your third parties.