In late 2024, global grocery conglomerate Ahold Delhaize reported a breach that exposed the personal data of over 2.2 million individuals. The compromised information included names, dates of birth, social security numbers, and health and financial data, highly sensitive material with long-term implications for identity theft and fraud.
What’s most troubling is how the breach occurred: not through Ahold’s own systems, but via a third-party file transfer vendor. This wasn’t a direct hit; it was collateral damage. And that should alarm every security leader overseeing a digital supply chain.
As organizations expand their partner ecosystems and rely more heavily on interconnected vendors and platforms, the threat landscape has undergone a significant shift. Today, a breach anywhere in your extended ecosystem is a breach in your business. The Ahold Delhaize incident is only the latest in a string of high-profile attacks that originated not from the enterprise itself, but from the vendors it trusts.
Supply Chain Attacks Are Surging And Evolving
A recent Panorays survey of 200 CISOs reveals a striking disconnect in how organizations approach third-party cyber risk. While 73% of CISOs report an increase in third-party incidents, only 22% have full visibility into their supply chain. This gap highlights the rise in third-party breaches worldwide.
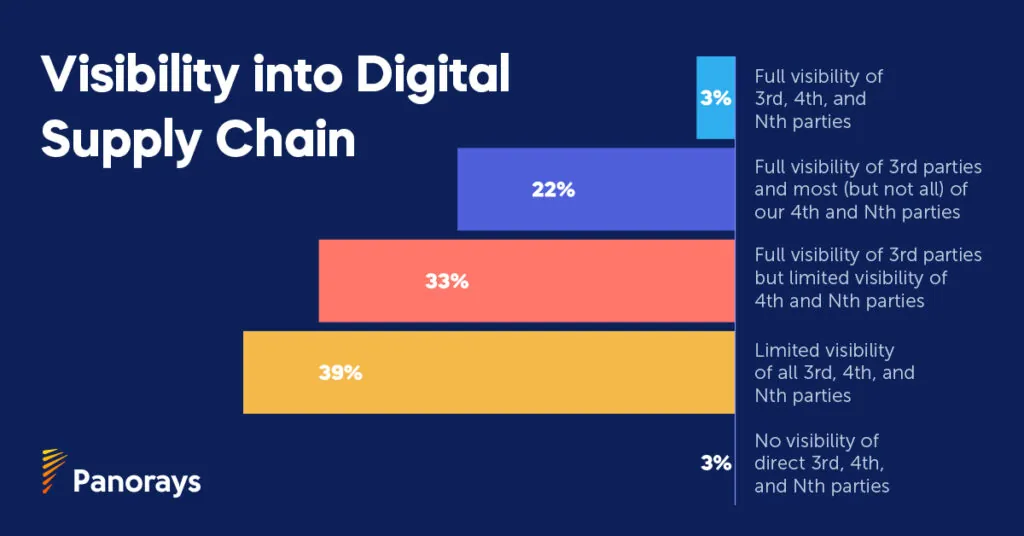
These findings echo broader industry concerns. In a Help Net Security article, experts warn that attackers are shifting upstream—targeting vendors’ development tools, integrations, and backend systems that often go unmonitored by risk teams.
A recent article from Help Net Security [June 30, 2025] explores this troubling trend. It reveals how attackers are increasingly targeting upstream systems like APIs, dev tools, and SaaS platforms, rather than high-visibility production environments. In many cases, attackers don’t even need to breach the primary target. They simply ride along quietly in the background, poisoning the software supply chain at development time or exploiting a vendor’s misconfigured platform.
This is exactly what happened in the Ahold Delhaize breach: attackers gained access through a trusted vendor’s infrastructure and exfiltrated highly sensitive data, all without initially tripping the alarm.
The Case for Evolving TPCRM
While some modern platforms are evolving to meet the demands of today’s cyber landscape, many traditional Third-Party Cyber Risk Management (TPCRM) methods are falling behind. Tools like questionnaires, annual audits, and static risk scores still dominate, but they often offer only point-in-time insights, heavily reliant on vendor self-reporting. These outdated practices leave dangerous visibility gaps.
The Ahold Delhaize breach reinforces why TPCRM must move beyond check-the-box compliance and toward a more resilience-driven, real-time, and risk-based approach. That means:
- Mapping third parties to business impact so you know which vendors matter most
- Gaining visibility into vendor infrastructure and tools, including development-time environments
- Continuously monitoring third-party risk posture for signs of drift or compromise
- Integrating security with procurement and legal to align contracts with real-time cyber expectations
What CISOs Should Do Now
In light of this and other recent supply chain breaches, CISOs and risk leaders should reevaluate how they assess, monitor, and engage with third-party vendors. It’s not enough to know who your vendors are; you must understand how they operate and what tools they depend on. If your current TPCRM program can’t provide that level of insight, it’s time to modernize.
The future of third-party cyber risk management is dynamic, contextual, and automated. Platforms like Panorays are built to support that future, helping organizations assess risk at scale, uncover hidden exposures, and respond quickly when something goes wrong.
Because in today’s interconnected world, your vendors’ weaknesses can become your headline risk.



