External Attack Surface Management
External Attack Surface Monitoring At Our Core
Panorays’ industry-leading technology scans thousands of assets across your supply chain, with real-time, accurate, and reliable data, so you can confidently evaluate your third-party cyber risks. Our detailed Cyber Posture Assessments uncover vulnerabilities and identify potential security gaps with a complete breakdown of your security posture as well as that of your third parties.
External Attack Surface Insights
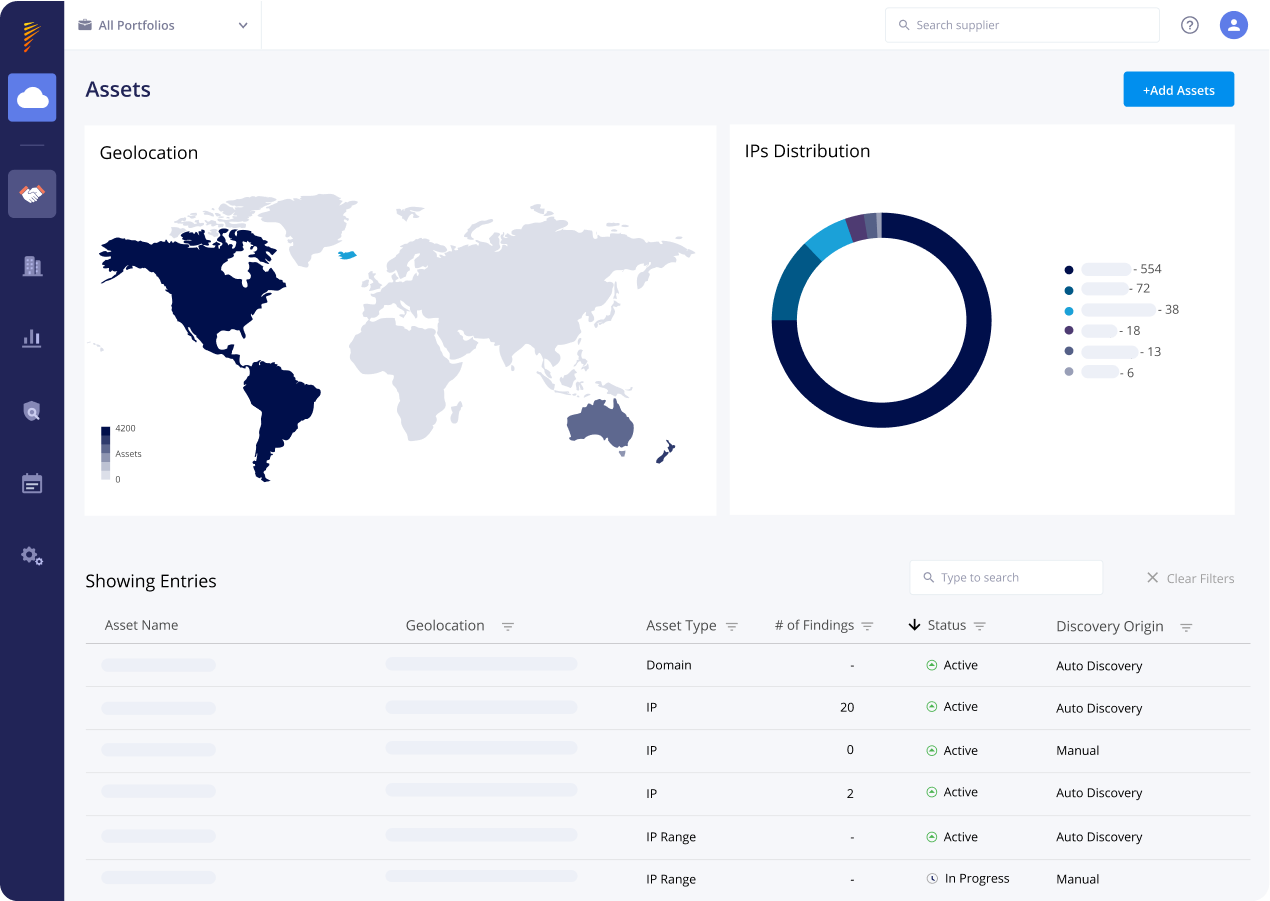
Our Attack Surface Management tools let you drill deep into your supply chain risks by, revealing Shadow IT and discovering 4th and 5th parties. You can easily assess the cyber posture of indirect parties and select critical vendors for continuous monitoring, so you can be the first to know of risks across your supply chain.
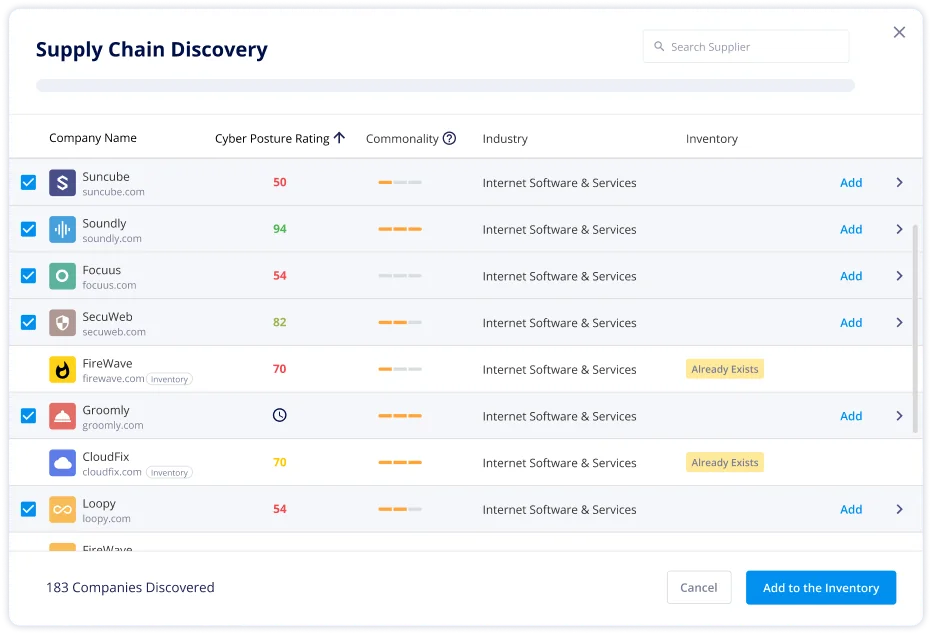
Real-Time Data on Evolving Risks
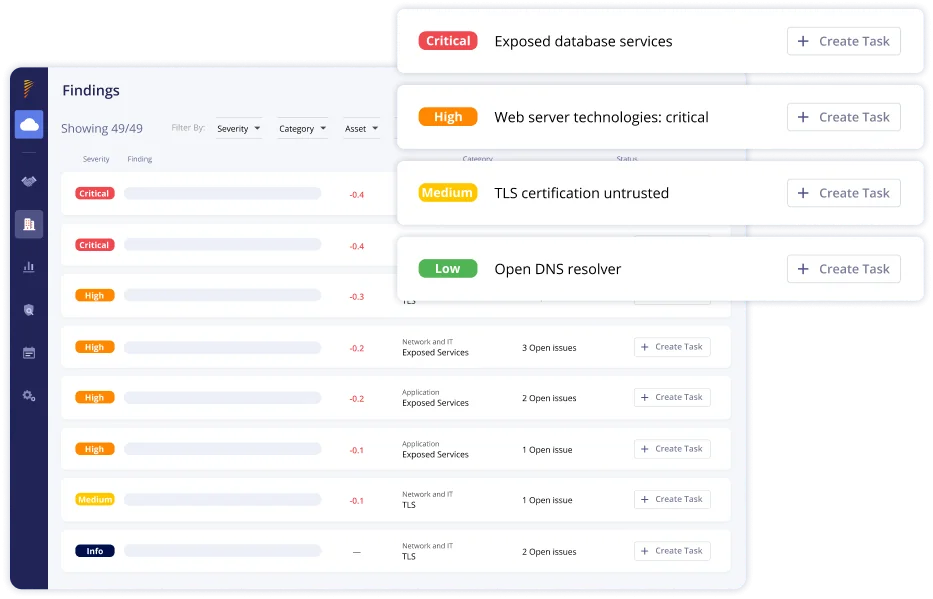
Panorays’ unique Risk Insights Portal gives you instant alerts on cybersecurity threats such as breaches, vulnerabilities, and zero-day attacks, with a detailed analysis of their impact on your direct and indirect suppliers. Panorays’ in-platform communication makes it easy to resolve vulnerabilities and remediate critical findings, all with a clear audit trail.
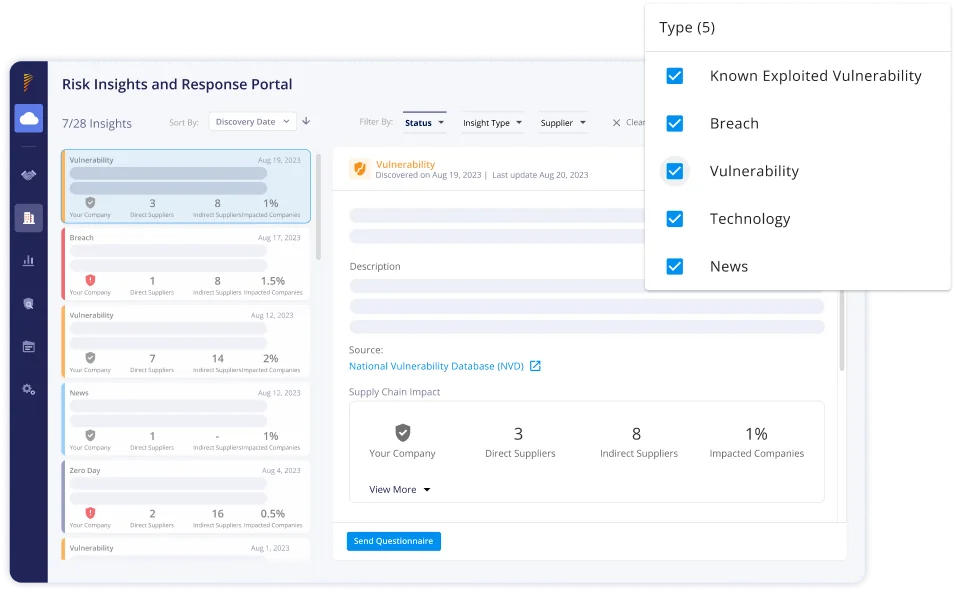
Manage Your External Attack
Surface And Reduce Cyber Risk
Secure Your Supply Chain
Know Who to Trust
Respond to Risks
Comprehensive Asset Management and Discovery
Panorays performs hundreds of tests across your attack surface, collecting information on exposed assets so you can understand potential risks across three layers.
Network & IT
Application
Human
Holistic Attack Surface Management
Cyber Risk Posture Ratings
Comprehensive Risk Analysis
Continuous Monitoring
Third and Fourth-Party Discovery
The Human Factor
Dark Web Insights
External Attack Surface Frequently Asked Questions
-
Attack surface monitoring lets you identify vulnerabilities and discover potential weaknesses in your digital assets. It also aids in cyber risk reduction and improved security posture, enabling proactive risk mitigation by addressing vulnerabilities before they are exploited.
-
External attack surface management involves monitoring and managing the digital assets and entry points that are accessible from outside an organization’s network. EASM focuses on protecting the organization from external threats and vulnerabilities.
-
Network attack surface: The external-facing network infrastructure and services.
Application attack surface: The software applications and web services are exposed to potential attacks.
Human attack surface: The vulnerabilities related to employees, their behaviors, and access privileges.
Supply chain attack surface: The risks associated with third-party vendors and partners. -
Identification: Identifying all assets, entry points, and potential vulnerabilities.
Assessment: Analyzing the identified elements for weaknesses and risks.
Mitigation: Implementing security measures to reduce the attack surface.
Monitoring: Continuously observing and updating the attack surface based on changes and emerging threats. -
To reduce your external attack surface, it is recommended to implement access controls and limit unnecessary access to resources, undergo patch management, network segmentation, and application security, along with training employees in security best practices.
-
Your attack surface can be measured by assessing the number of exposed assets and entry points.
As well, vulnerability assessments, attack surface mapping, and tracking changes in the attack surface over time can serve as tools to measure your attack surface.
Learn about other Panorays features
Hundreds of teams evaluate and manage their vendors’ security with Panorays