On Friday, July 19th, Windows workstations and servers worldwide started displaying the ‘Blue Screen of Death’ (BSOD error), causing them to shut down and disrupt services. The next day Microsoft attributed the outage to a CrowdStrike incident in which an update resulted in a massive IT outage that has impacted airports, businesses, transportation links, supermarkets, and broadcasters worldwide.
The outage, impacting Microsoft Windows operating systems, was caused by a defective software update from Crowdstrike, a global cybersecurity firm. This incident has led to over 5,000 flight cancellations worldwide and disabled an estimated 8.5 million computers globally. It is expected that resolving the software issues will take some time.
The Global Impact of the Crowdstrike Supply Chain Incident
While the CrowdStrike event is not a cybersecurity incident, the software serves as a piece of fundamental cybersecurity infrastructure for many large enterprises and is a part of critical infrastructure for companies around the world. Its malfunction has brought organizations to a complete halt, hindering them from operating and delivering their services and products, resulting in a global supply chain disruption. Additionally, the outage has left organizations vulnerable to cyber attacks.
Best Practices for Handling Supply Chain Incidents
As we learn more about the CrowdStrike incident, more insights will emerge. Meanwhile, here are some best practices to strengthen your supply chain against future disruptions:
- Identify Your Critical Suppliers: Pinpointing your third and fourth parties ensures you’re prepared to track the implications for operational and cyber risk across your supply chain in the event of an incident. By gaining visibility into indirect suppliers impacted by an outage or cyber attack, you’ll be able to understand the impact your direct suppliers are facing and request necessary details and mitigation steps to ensure your business continuity.
You will also need to assess whether your vendors are still operating with the proper security controls in place. For example, some businesses may choose to disable Crowdstrike instead of restoring their systems to an earlier version and try finding to a replacement, in the meantime, this leaves you and your vendors vulnerable and with a loss of critical security controls. - Develop a Response Strategy: Align with stakeholders both internally and externally to create a unified response plan. It is vital to have ready-to-go questionnaires for critical suppliers to ensure you collect information on how they were affected, which of their systems are compromised, are they still able to provide the services they perform for you, and how they plan to address these challenges in the short and long term.
- Plan for Remediation and Mitigation: Create a remediation and mitigation plan along with your suppliers to minimize disruption of your supply chain. Using the feedback from suppliers’ questionnaires, you will be able to understand any risks posed to your business and create a clear plan of action to mitigate outstanding issues.
Recognizing the risks associated with third and fourth parties is essential for organizations. New regulations are emerging globally, such as DORA, requiring businesses to identify, manage, and report on supply chain risks. The Crowdstike incident is just one example of why regulations like these came about.
How Security Teams are Managing Supply Chain Disruptions With Panorays
Panorays’ comprehensive platform provides deep visibility into even the most complex supply chains, effectively addressing security risks to the Nth party level. The platform categorizes and analyzes third, fourth, and fifth parties, identifying which ones are crucial for supporting your organization’s critical functions.
By doing so, Panorays ensures that supply chain risks are managed effectively, helping clients navigate and mitigate current challenges. Here are some specific ways Panorays can assist in supply chain incidents like Crowdstike:
- Nth Party Discovery: Currently, 18% of Panorays customers have classified CrowdStrike as a “critical infrastructure” third party, opting for continuous monitoring to ensure ongoing oversight and risk management. Panorays allows its users to easily filter through suppliers that rely on CrowdStrike and see how many of their direct and indirect suppliers could face potential operation disruptions.
- Prioritize Critical Vendors: With Panorays, security teams can tier their vendors based on business criticality and data sensitivity, selecting their most critical vendors for continuous monitoring. As operation and cyber risks arise, Panorays will notify teams of such changes and display the impact of an event across their supply chain.
Additionally, users can customize the risk scores of affected vendors, adjusting the scores of those impacted by CrowdStrike, or any other incident, to reflect a higher risk level until appropriate mitigation measures are in place. These additional risk factors can be customized according to the industry and the risk appetite of the user as a policy or per third-party case basis.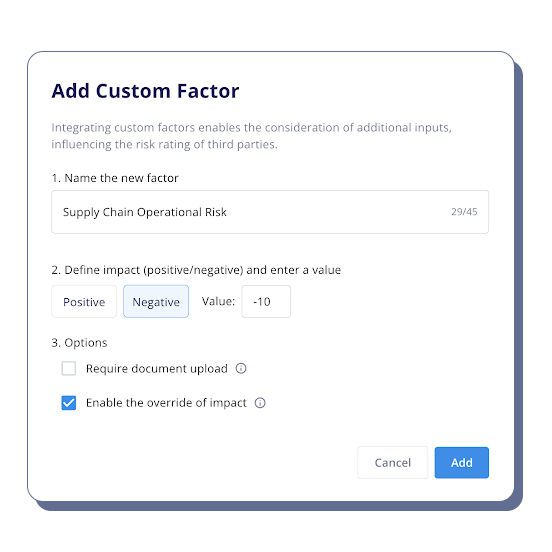
- Risk Portal Notifications: Customers who have designated CrowdStrike as a critical supplier received a notification through the Risk Insights Portal, detailing the scale and implications of the event, along with which suppliers were affected.
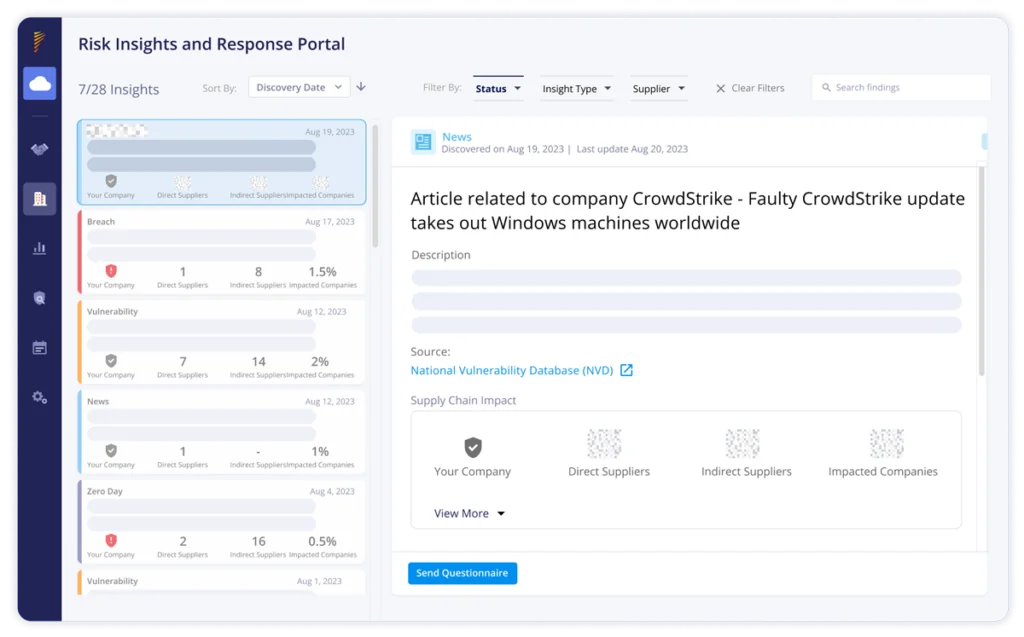
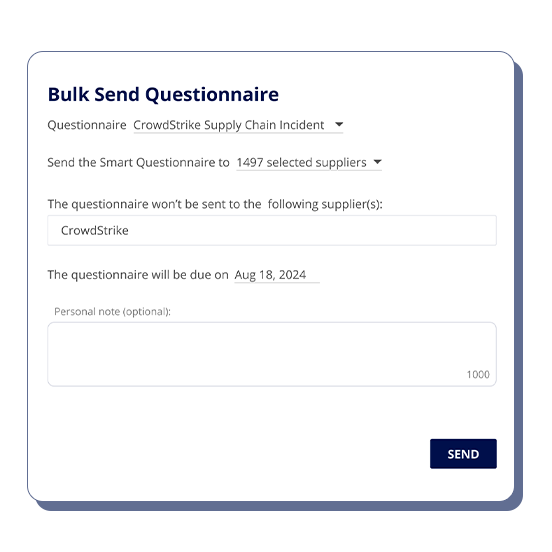
- Questionnaire Templates: Security teams can use in-app cybersecurity questionnaires to gather detailed information from their affected suppliers. These questionnaires help assess how the suppliers were impacted by an incident and outline their proposed mitigation steps. This process enables security teams to have a collaborative experience with the third party, understand the extent of the disruption, and ensure that appropriate measures are being taken to address and resolve the issue effectively.
Want to learn more about how Panorays can help you manage third-party risk? Get a demo today.
FAQs
-
CrowdStrike is a global cybersecurity company known for its advanced endpoint protection and threat intelligence solutions. The company is renowned for its threat intelligence capabilities and its ability to detect and respond to cyber threats quickly.
-
The CrowdStrike supply chain incident was caused by a defective software update from CrowdStrike itself. This problematic update affected Microsoft Windows operating systems and led to significant operational disruptions, including widespread computer malfunctions and numerous flight cancellations globally. The incident underscored the critical importance of thoroughly vetting and testing software updates, especially when they impact essential infrastructure.
-
The CrowdStrike incident primarily affected organizations and individuals relying on CrowdStrike’s software for endpoint protection and cybersecurity. Key impacts include businesses and enterprises, critical infrastructure, airlines and travel industries, and individual users. The widespread impact underscored the interconnectedness of modern IT systems and the far-reaching consequences of disruptions in critical software and services.



