Panorays Third-Party Cybersecurity Questionnaires
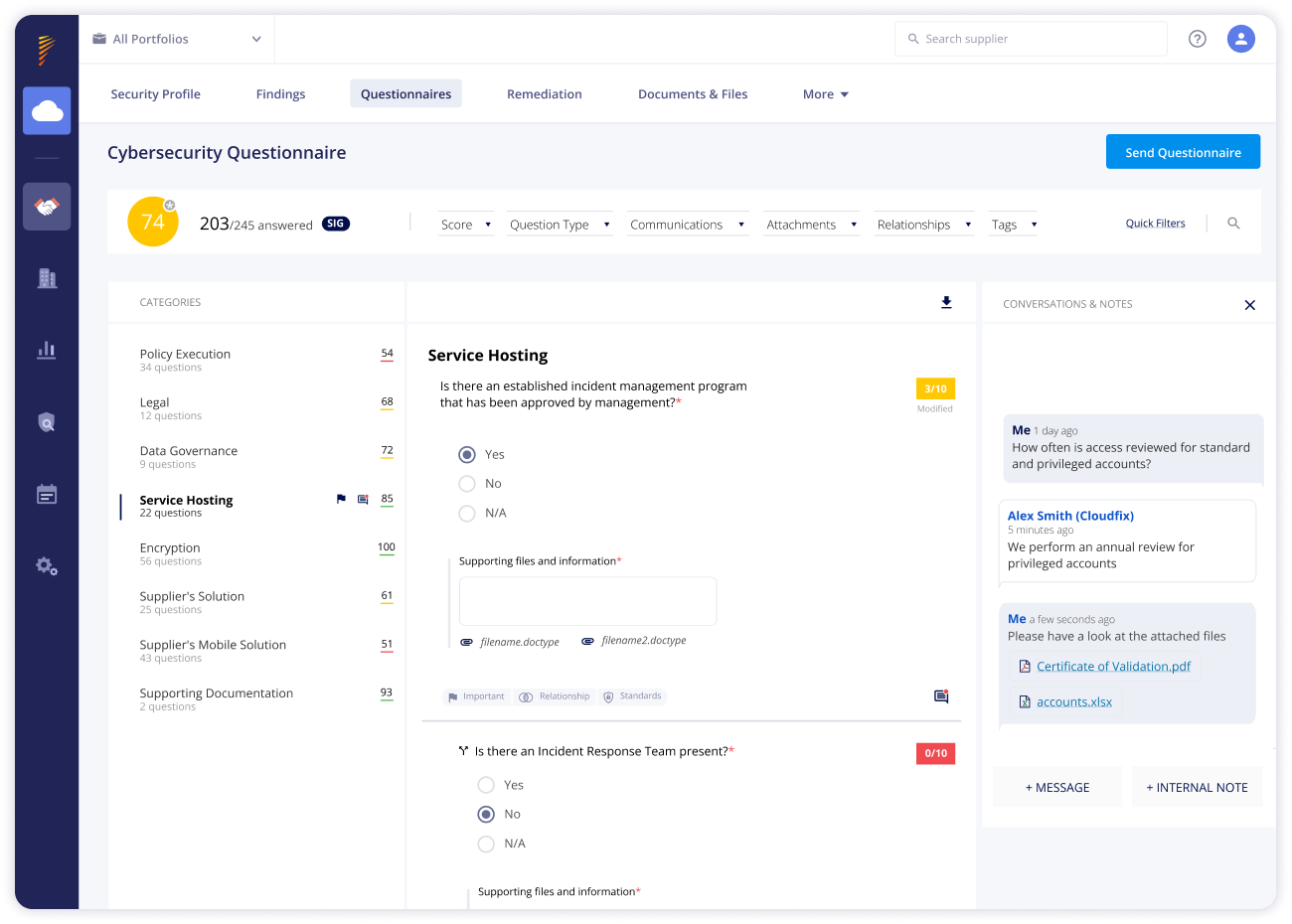
Customized Third-Party Cybersecurity Questionnaires
Simplify vendor assessments with Panorays’ customized questionnaires tailored to your specific vendor relationships and their business impact. With our auto-generated questionnaire templates, you can concentrate on the questions that really matter.
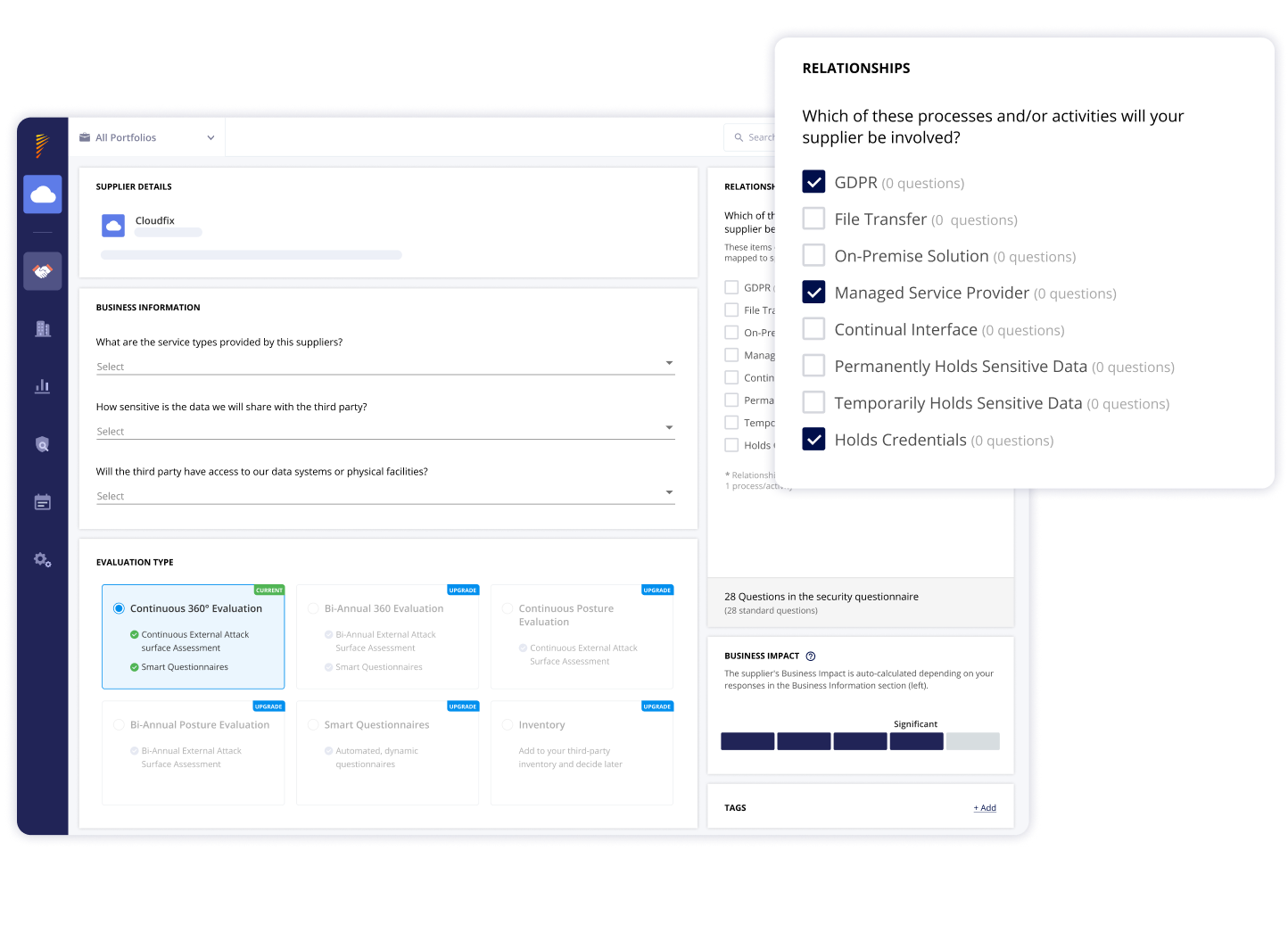
Validated Cybersecurity Questionnaire Responses
Panorays validates questionnaire responses by comparing them with vendors’ external documents and cyber posture assessments. Any gaps are then highlighted, making it simple to review and address them.
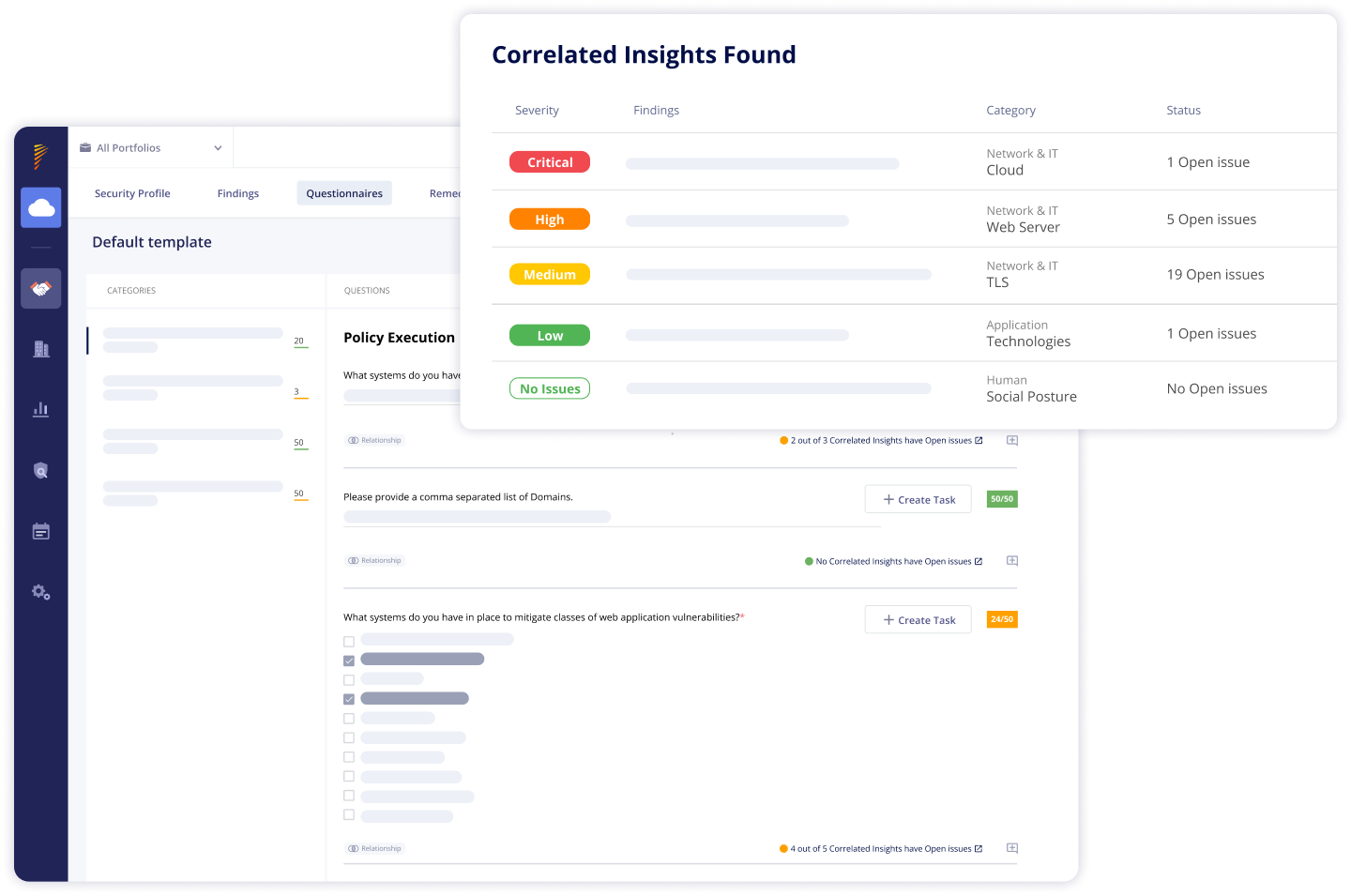
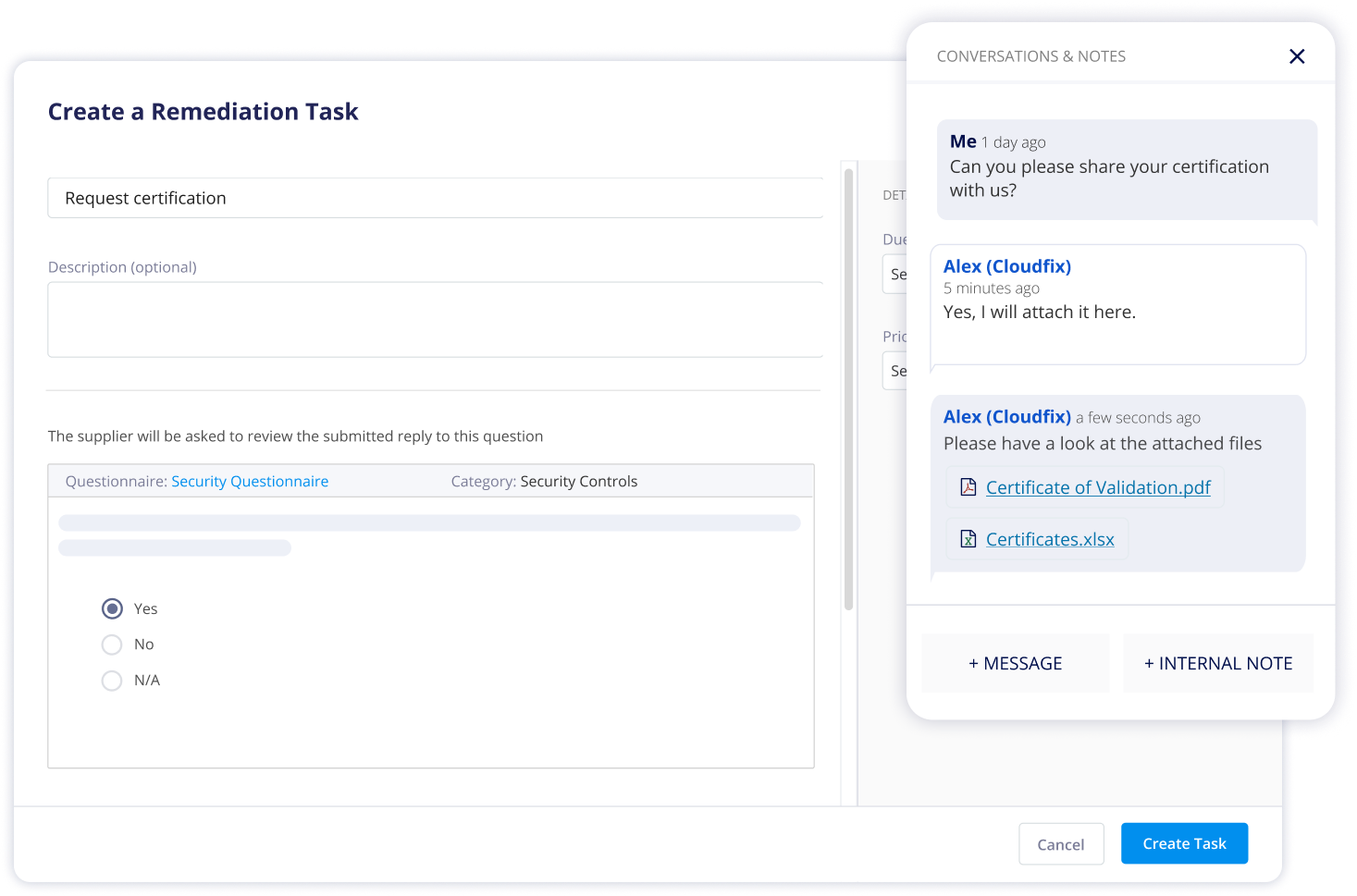
Effortless Third-Party Collaboration
Panorays streamlines collaboration with your third-parties by transforming questionnaire responses into automated tasks. You can effortlessly establish due dates, receive timely reminders, and engage in convenient in-app chats for effective communication with your external vendors.
Automate, Validate and Scale
Cybersecurity Questionnaires

Ensure Regulation Compliance

Efficiency at Scale

Collaboration Made Simple

Accelerated Responses
Four Steps to Seamlessly Manage Vendor Questionnaires
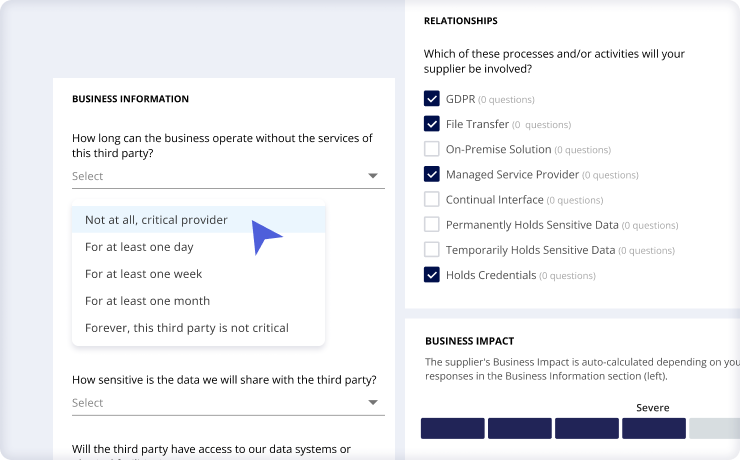
Step 1: Customize Questionnaires
Build questionnaires from industry standard templates, or create unique questions based on third-party criticality.
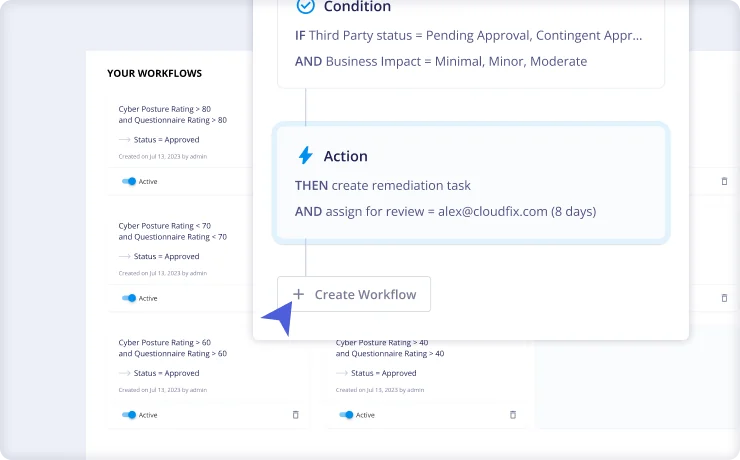
Step 2: Automate Questionnaire Workflows
Set up questionnaire workflows to automatically create remediation tasks, assign teammates, and approve or reject certain vendors based on their scores.
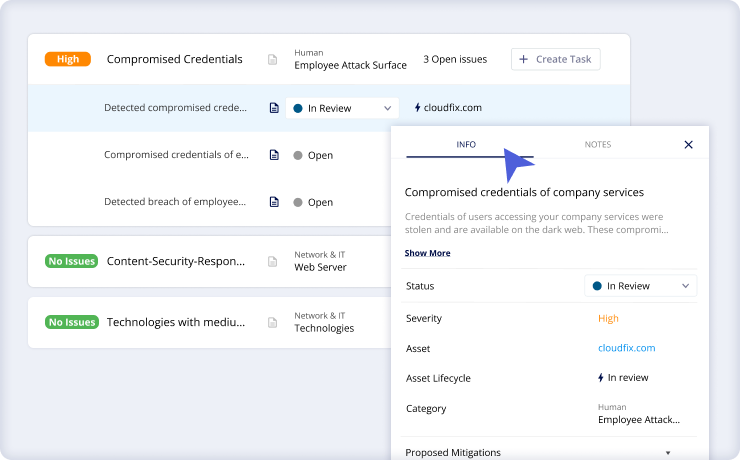
Step 3: Validate Vendor Responses
Cross-reference vendor responses with cyber posture data and vendor documentation to get a comprehensive view of third-party risks.
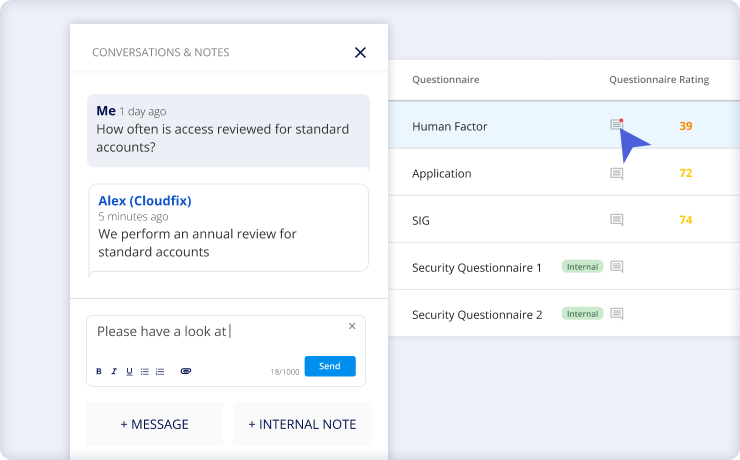
Step 4: Resolve Cybersecurity Gaps
Communicate with vendors to resolve any security gaps and keep track of all open tasks in an interactive management inventory.
-

Step 1: Customize Questionnaires
Build questionnaires from industry standard templates, or create unique questions based on third-party criticality.
-

Step 2: Automate Questionnaire Workflows
Set up questionnaire workflows to automatically create remediation tasks, assign teammates, and approve or reject certain vendors based on their scores.
-

Step 3: Validate Vendor Responses
Cross-reference vendor responses with cyber posture data and vendor documentation to get a comprehensive view of third-party risks.
-

Step 4: Resolve Cybersecurity Gaps
Communicate with vendors to resolve any security gaps and keep track of all open tasks in an interactive management inventory.
Key Vendor Questionnaire Features
Built-in SIG and CAIQ Questionnaires
Custom Questionnaire Templates
Customized Risk Assessments
Automatic Vendor Evaluations
Validated Responses
Easy-to-Manage Workflows
Cybersecurity Questionnaire Frequently Asked Questions
-
The vendor risk assessment security questionnaire is a set of inquiries used to evaluate the security practices and risks associated with a third-party vendor’s products or services.
-
A cybersecurity risk assessment typically includes an analysis of an organization’s assets, threats, vulnerabilities, likelihood of incidents, and potential impact to determine its overall security posture.
-
The purpose of a vendor security questionnaire is to assess and ensure that a vendor complies with cybersecurity and data protection standards, reducing potential security risks and ensuring compliance.
-
A comprehensive risk assessment should include an identification of assets, threat analysis, vulnerability assessment, risk calculation, and mitigation strategies to address potential security threats effectively.
Learn about other Panorays features
Hundreds of teams evaluate and manage their vendors’ security with Panorays