The role of the CISO has evolved beyond safeguarding assets and is now about driving business value. With this in mind, the savvy CISO and Security Manager can view the Digital Operational Resilience Act (DORA) as more than a regulatory requirement—he or she can see it as an opportunity.
While compliance may seem like a burden, DORA offers forward-thinking leaders the chance to seize strategic advantages. By embedding resilience into their operations, the CISO can aim higher than meeting regulatory demands; the CISO can aim to innovate, build trust, and differentiate their organizations in the market. Let’s dive into how DORA compliance can be a catalyst for achieving a competitive advantage.
What is DORA?
DORA, short for the Digital Operational Resilience Act, is an upcoming regulatory measure established by the European Union. It aims to strengthen the ICT (information and communication technology) risk management framework within the EU financial industry, responding to the ever-growing threat of cyber attacks on increasingly complex digital supply chains.

An essential part of DORA involves categorizing ICT systems and services based on the level of risk they pose. This allows organizations to monitor evolving risks for key technology supply chains more efficiently and enables threat prioritization according to their relevance to the business.
This approach enhances the monitoring of evolving risks to key technology supply chains by allowing businesses to prioritize threats based on their relevance.
DORA mandates that companies in the financial sector adhere to strict rules designed to bolster their capabilities in managing and mitigating ICT risks. This comprehensive framework is not just about compliance; it’s about embedding resilience into the very fabric of financial institutions.
What is DORA’s Goal?
The primary goal of DORA is to ensure that financial entities are well-prepared to handle ICT-related incidents. This means having robust processes in place for detection, protection, containment, and recovery, allowing institutions to swiftly address any disruptions to their operations. DORA is the first regulation aimed specifically at addressing the challenges of third-party cyber risk in digital supply chains.
How Will DORA Be Enforced?
DORA compliance will be enforced through a combination of on-site and off-site inspections. These inspections may involve requests for specific information, such as incident logs, details of implemented cybersecurity defenses, and comprehensive reports on ICT risk management practices.
What Are DORA’s Focus Areas?
DORA focuses on five main areas concerning financial services organizations:
- ICT Risk Management: Mapping ICT systems and identifying assets to conduct risk assessments on ICT systems.
- Incident Reporting: Requires mandatory rapid incident reporting to manage and mitigate disruptions and threats related to ICTs, security payments and operations.
- Digital Operational Resilience Testing: Demands regular testing of ICT systems and that they have recovery plans in place
- Third-Party Risk Management: Require the rigorous oversight of ICT third-party providers, including cloud services, to ensure that they do not become a source of vulnerability.
- Intelligence and Information Sharing: Although not unique to DORA, sharing information and intelligence is encouraged as it supports strengthening resilience and security along the entire supply chain.
What Are the Challenges of DORA Compliance?
Achieving DORA compliance is far from straightforward. The challenges are multifaceted and will require many institutions to navigate complex digital ecosystems, manage legacy systems, oversee third-party providers, and stay ahead of constantly evolving cyber threats. Additionally, DORA introduces the need to identify and manage not only third-party risks but also fourth, fifth, and nth-party risks as well as concentration risks in the supply chain, further complicating the compliance landscape.
The Complexity of Digital Ecosystems
Financial institutions operate within complex digital ecosystems with numerous technologies, platforms, and vendors. The more layers of technology and partnerships, the harder it is to maintain consistent ICT risk management.
Legacy Systems
Many financial institutions are burdened with legacy systems—outdated technologies patched over time—that often clash with modern resilience standards. Integrating these systems with newer technologies is challenging, resource-intensive, and costly, while their complexity can make it difficult to identify potential vulnerabilities, complicating compliance.
Third Parties and Beyond: Managing 4th and 5th Party Risks
DORA emphasizes the need for operational resilience of external partners, and financial institutions increasingly rely on third-party providers for essential digital services. This presents a unique challenge, as financial institutions often have limited control over the processes and risk management practices of their third-party providers.
The challenge doesn’t stop at third-party risks. DORA also necessitates the identification and management of fourth- and fifth-party risks posed by the subcontractors and partners of third-party providers. By assessing each third party’s inherent and material risks, organizations can prioritize the most critical vulnerabilities in their supply chain.
This requires an even deeper level of oversight and due diligence, as the resilience of your entire operation could hinge on the practices of a vendor several steps removed from your direct control.
Constantly Evolving Threats
The ongoing need to stay ahead of threats adds another layer of complexity to DORA compliance. Institutions must not only meet current standards but also anticipate and prepare for future challenges.
Navigating these challenges requires a proactive and well-resourced approach. Institutions that can successfully overcome these hurdles will not only achieve compliance with DORA but also position themselves as leaders in operational resilience, turning these regulatory challenges into competitive advantages.
Turning Challenges Into Opportunities
DORA compliance can seem daunting, but it offers a unique opportunity to strengthen your company’s operational resilience and gain a competitive edge.
By addressing the challenges head-on, companies based in Europe, as well as foreign institutions that conduct business in Europe can get ahead of the game and transform DORA’s requirements into strategic advantages.
Don’t believe us? Then believe Mark Neeb. He is the former President and CEO of The Affiliated Group, a debt collection agency based in the US.
In 2011, when the Consumer Financial Protection Bureau (CFPB) was established, Neeb was unhappy and frustrated about a new government agency imposing more regulations. But instead of resisting, he took an unexpected and bold approach.
At the next ACA convention, during a CFPB presentation with hundreds in the audience, Neeb did something no one anticipated—he raised his hand and volunteered his company for an audit by the CFPB. The room was stunned, and even the CFPB representatives were caught off guard.
This daring move put Neeb’s company in the spotlight as a model of compliance and integrity. By embracing the new regulations, Neeb turned a potential challenge into an opportunity, making the regulations work in his favor.
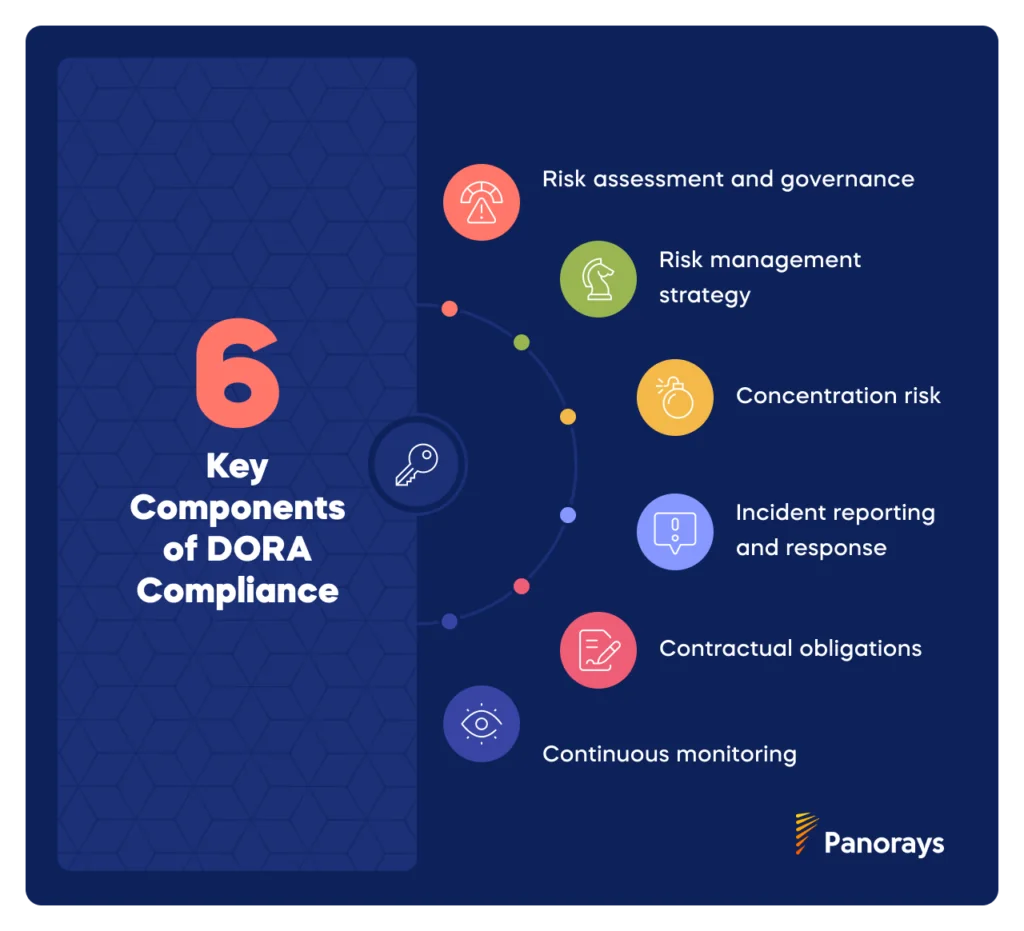
Below are some ways to turn DORA Compliance into a competitive advantage:
1. Leverage a Comprehensive ICT Risk Management Framework
Challenge: Ensuring resilience across complex digital ecosystems, especially with the inclusion of 4th and 5th-party risks, can be overwhelming.
Opportunity: Implementing a comprehensive ICT risk management framework that includes third-party oversight not only ensures compliance but also enhances your organization’s ability to respond to incidents swiftly. This holistic approach positions your institution as a trusted entity, capable of navigating the complexities of modern financial operations.
Benefit: A strong ICT risk management framework not only meets DORA’s requirements but also builds trust with clients and partners by demonstrating your commitment to safeguarding their data and transactions.
2. Modernize Legacy Systems
Challenge: Upgrading legacy systems to meet digital resilience standards is arduous, costly, and time-consuming. Plus, who wants to fix what’s not broken?
Opportunity: Use DORA compliance as a catalyst to modernize your IT infrastructure. This investment will pay off by reducing long-term operational risks and improving system efficiency. Modernized systems are easier to manage, integrate better with new technologies, and offer enhanced security features, making your institution more agile and resilient.
Benefit: Modernized systems increase operational efficiency, reduce vulnerabilities, and position your institution to adapt more quickly to future regulatory changes, as well as to adopt new and beneficial technologies.
3. Enhance Third-Party and Supply Chain Resilience
Challenge: Ensuring the operational resilience of third-party providers and managing the extended network of 4th and 5th parties can be difficult.
Opportunity: Strengthen your third-party risk management processes by establishing more rigorous oversight and due diligence practices. This could involve regular audits, continuous monitoring, and clear communication channels with all parties involved. By doing so, you can minimize risks throughout your supply chain and ensure that all partners adhere to the same high standards.
Benefit: Being DORA compliant and managing third-party risks can attract vendors who value cybersecurity and are committed to high standards. It also deters those unwilling to invest in risk management, ensuring that your partnerships are aligned with your organization’s priorities.
4. Stay Ahead of Evolving Cyber Threats
Challenge: Cyber threats are constantly evolving, requiring continuous monitoring and updating of security measures.
Opportunity: Use DORA’s emphasis on continuous monitoring and reporting as an opportunity to develop a proactive cybersecurity strategy. Implement advanced threat detection tools, conduct regular security assessments, and stay informed about emerging threats.
DORA’s insistence on clearly defining the criticality of ICT third parties and their respective digital supply chains will assist the financial entity to prioritize threats according to their impact on the business. This proactive stance will not only help you stay compliant but also ensure your institution is always a step ahead of potential risks.
Benefit: By staying ahead of cyber threats, your institution can prevent incidents before they occur, safeguarding your reputation and avoiding costly disruptions.
5. Be the First to Report Incidents
Challenge: The Fear of Reporting
Challenge: Fear of embarrassment or damage to the company’s reputation by voluntarily reporting a breach is a major hurdle.
Opportunity: Establishing yourself as a transparent organization can significantly strengthen trust among partners, vendors, and more important, regulatory or government agencies. This transparency not only aligns with DORA’s requirements but also fosters positive relationships with key stakeholders, enhancing your reputation as a leader in ethical practices and risk management.
Benefit: Being transparent builds stronger relationships with partners, vendors, and regulatory bodies and leads to increased confidence in your operations and a more favorable standing in regulatory reviews.
Practical Steps for Financial Institutions
For many organizations, one of the first steps towards DORA compliance in the third-party cyber risk arena will be documenting the digital supply chains that support their critical and important functions (known as “CIFA”).
DORA mandates that financial entities submit a report in a complex format known as the “Register of Information” which will include not just ICT third parties, but also connections to layers of subcontractors and concentration risk, where a single supplier or subcontractor is crucial to multiple aspects of the operation.
While challenging, doing the work of categorizing ICT third parties by criticality, “sensitiveness” of data (in the terminology of the regulation), and how replaceable a given supplier is a valuable exercise and will help prioritize threat management in the future.
Here are actionable measures that can help your institution achieve DORA Compliance:
1. Automation and Monitoring:
Automation makes complying with DORA much less burdensome.
By automating routine compliance tasks, financial institutions can make the job of achieving compliance significantly easier. Automation tools continuously monitor ICT systems and third-party relationships, helping to identify potential risks in real-time and reducing the chances of human error. Automation not only streamlines the compliance process but also improves the organization’s overall resilience and ensures that compliance is maintained consistently and efficiently.
2. Training and Awareness:
Compliance is not just about technology; it’s also about people. Comprehensive training programs are needed to educate employees at all levels about DORA requirements—and the importance of cybersecurity (but we’re preaching to the choir).
3. Leverage External Expertise:
DORA’s complex regulatory landscape can be especially challenging for smaller institutions. Cybersecurity consultants or specialized legal advisors can provide valuable insights and guidance. These experts can help your organization gain a competitive edge by staying ahead of compliance trends and avoiding costly mistakes.
Panorays as a Solution
Panorays offers a comprehensive platform that helps financial institutions manage their third-party risks in line with DORA requirements. With Panorays, organizations can automate their risk assessment processes, continuously monitor their third-party vendors and respective digital contracting chains, and ensure that all ICT services align with the latest regulatory standards. Panorays’ ability to export directly in the DORA Register of Information format speeds required reporting to the Supervisory Authorities. The platform’s robust features allow institutions to gain full visibility into their digital ecosystems, making it easier to identify and mitigate risks at every level.
By adopting Panorays, financial institutions can streamline their compliance efforts, enhance their operational resilience, and ultimately position themselves as trusted leaders in the financial sector.Read this guide on DORA compliance and third-party risk management or reach out to us to help you get started toward becoming DORA compliant.



