You don’t need to be based in Europe to keep an eye on DORA. If your company operates in one of the 22 industries defined in DORA’s Article 2, or provides critical services to those industries, compliance may be required—even if you’re headquartered outside of Europe. This is especially true for businesses with subsidiaries or operations within the EU, as DORA’s reach extends beyond borders.
There’s another reason to learn more about DORA–one that will increase your value as the security leader in your organization.
Quick Recap: What is DORA?
The Digital Operational Resilience Act (DORA) is a new regulation aimed at enhancing the cyber resilience of financial institutions within the European Union. Its primary goal is to ensure that organizations can withstand and recover from various cyber threats and operational disruptions.
In light of major supply chain attacks like the MOVEit breach, DORA mandates strict compliance not just for EU financial institutions, but also for their third-party providers and subcontractors. These rigorous standards aim to protect the entire digital supply chain and create a more secure, resilient financial ecosystem across Europe.
How European Financial Concerns Lead to DORA
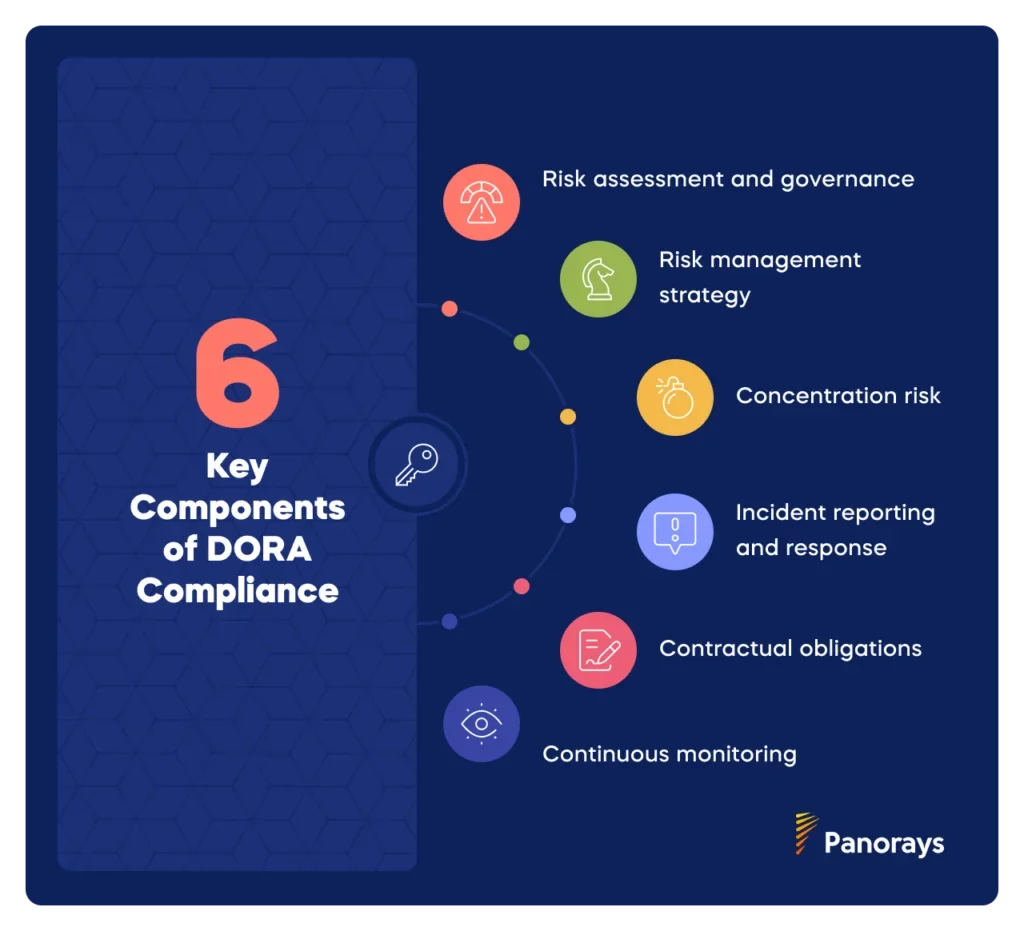
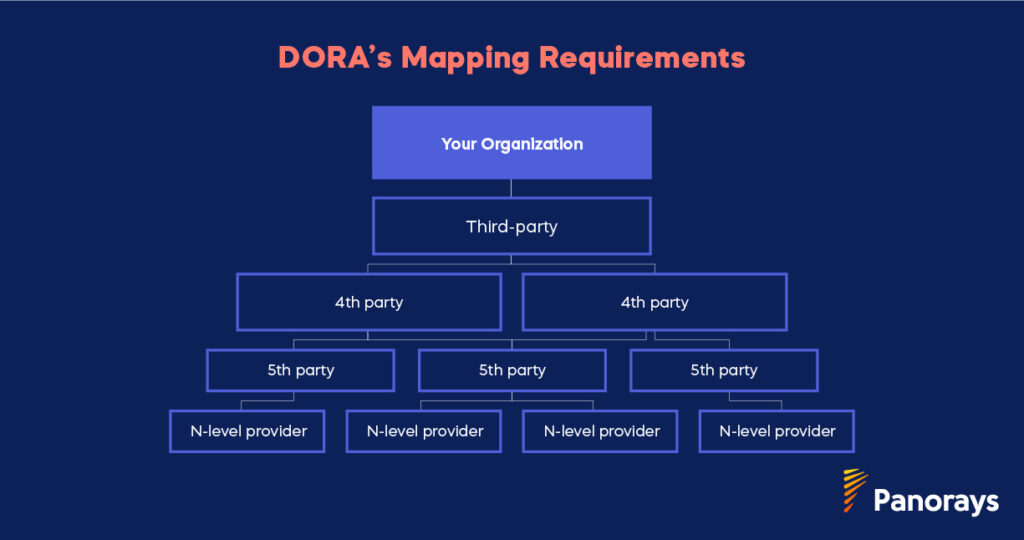
DORA encapsulates over a decade of banking’s technology security best practices and sets a new precedent in cybersecurity. DORA is more rigorous than prior regulations, with regulators placing a greater emphasis on its enforcement. DORA covers a wider scope and requires entities to map the “functions” of their business and the critical third-party suppliers (“ICT” in DORA-speak) that support each function—-as well as the digital supply chain that underlies each of their critical third-party suppliers.
DORA Requirements
- Mapping the important functions of your business (the CIFs)
- Mapping the suppliers who are critical to your CIFs
- Mapping out the subcontracting chain supporting the suppliers in #2 above.
For many CISOs, this means stepping into uncharted territory.
The bonus? It will give cyber practitioners a clear understanding of the risk vendors pose, including a combination of criticality and sensitivity of data to which vendors have access.
Yet, this task has CISOs across Europe understandably concerned, especially considering their detailed assessments will likely face intense regulatory scrutiny.
These concerns are reflected in a recent McKinsey & Company survey. Despite 94% of financial institutions working on DORA compliance, practitioners expressed worry about unclear definitions of critical functions and ICT providers. They also worry about limited time for compliance.
These concerns are reflected in a recent McKinsey & Company survey. Despite 94% of financial institutions working on DORA compliance, practitioners expressed worry about unclear definitions of critical functions and ICT providers. They also worry about limited time for compliance.
I’m also seeing these worries firsthand from cybersecurity leaders seeking guidance from Panorays.
Why DORA Compliance Matters Globally
As regulatory standards evolve, global organizations will need to implement similar practices to ensure comprehensive resilience. Here are two reasons why cybersecurity professionals in the US, as well as anywhere else in the world, should be looking closely at DORA.
1. Business Activity in Europe
If your business has operations or subsidiaries in Europe, or if you work in one of the 22 industries impacted by DORA, you’ll need to assess the risks across your digital supply chain. This involves mapping not only your vendors, but also their subcontractors, and every subsequent link in the chain.
2. Increase Your Professional Value
Using DORA as a framework to categorize and map your functions and vendors by criticality will give you deep insights into your business and its potential risks. With this wealth of information, you’ll be well-equipped to engage the C-suite and Board in meaningful discussions about risk, helping them focus their energy on the company’s strategic goals.
DORA’s Key Pillars and Their Impact on the US
DORA’s key pillars—risk management, incident reporting, and operational resilience testing—carry implications for US businesses with operations or ties to Europe. Let’s see how:
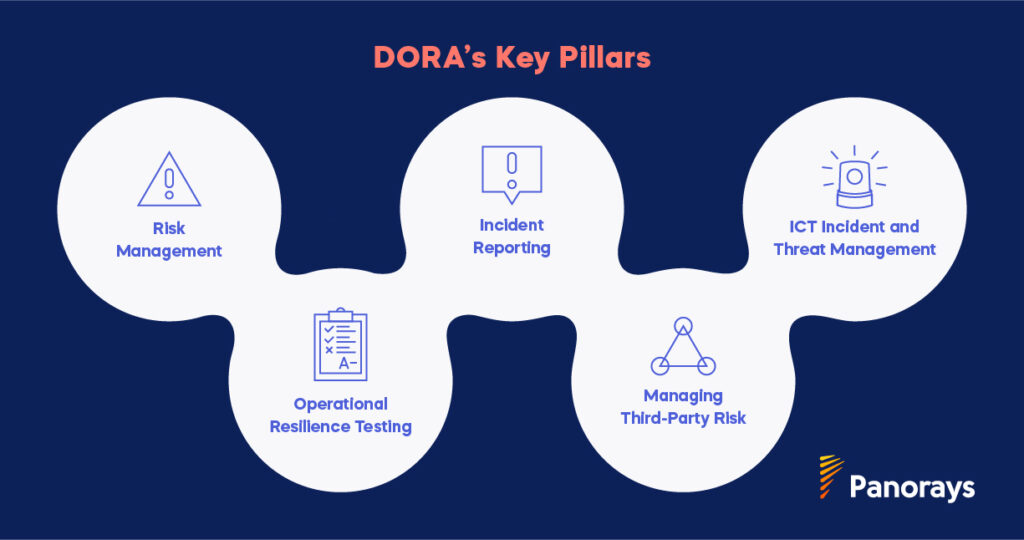
1. Risk Management
DORA’s structured risk management framework is designed to identify, assess, and mitigate risks across financial institutions and their supply chains. While US institutions follow various frameworks like NIST CSF, NIST SP800-53, or the FFIEC guidelines, DORA introduces more comprehensive requirements, particularly regarding the management of third- and fourth-party risks.
2. Incident Reporting
One of DORA’s strictest mandates is the requirement for prompt and detailed incident reporting.
Although the US has its own regulations, such as the CISA Cyber Incident Reporting mandate, DORA takes incident reporting to another level by enforcing stringent timelines and reporting protocols.
3. Operational Resilience Testing
DORA mandates regular operational resilience testing for financial institutions. This includes threat-led penetration testing and stress testing to identify weaknesses in ICT systems. These tests are essential for ensuring that systems can withstand real-world cyberattacks and operational disruptions.
For US businesses, especially those with cross-border financial operations, adopting these testing practices can significantly improve overall security posture. Sure, there are US frameworks that encourage resilience, but DORA’s prescriptive approach to testing might prompt US organizations to take a more rigorous and systematic approach to resilience— especially if they have European clients or partners.
4. Managing Third-Party Risk
DORA places a heavy emphasis on third-party risk management, requiring financial institutions to assess their critical third-party providers and even subcontractors. The process DORA demands can be broken down into five steps:
- Identification of critical or important functions (CIFs) and third-party providers
- Categorization of functions and vendors based on their criticality to the business
- Risk assessment of third-party providers and their subcontractors
- Ongoing monitoring of these providers to ensure compliance and resilience
- Contingency planning to prepare for any disruptions or failures in the supply chain.
This focus aligns closely with existing US frameworks such as TPRM and vendor risk management practices outlined by OCC and FFIEC. However, DORA goes further in requiring a more detailed understanding of 4th party risk—something that is not demanded by US regulations and, quite frankly, is new to most CISOs.
5. ICT Incident and Threat Management
DORA’s comprehensive approach to ICT incident and threat management requires financial institutions to have frameworks in place for detecting, managing, and reporting cyber threats with strict timelines.
For US businesses with European operations or partners, aligning with DORA’s strict incident reporting timelines can enhance their global threat management capabilities. Unlike US regulations like CISA that mandate reporting, DORA’s detailed framework offers a model to strengthen operational resilience and cross-border incident response.
Which Industries are Affected by DORA?
DORA’s regulations extend across a wide range of industries in the financial ecosystem and aim to bolster digital resilience at every level. Cybersecurity professionals in businesses directly or indirectly connected to these sectors need to understand their obligations under this sweeping legislation. Here are some of the industries affected by DORA:
- Alternative funds (AIFMs)
- Clearinghouses
- Credit organizations
- Crypto services
- Digital payment companies
- Insurance firms
- Investment enterprises
- Payment service providers
- Trading platforms
- UCITS management firms
- ICT third-party service providers
This last bullet is far-reaching and includes any organization providing a critical service to a company in one of the 22 industries, regardless of where you are headquartered or operate.
The inclusion of ICT third-party service providers highlights DORA’s expansive reach, emphasizing the importance of building resilience not just within financial institutions but across their entire digital ecosystem. This interconnected approach ensures that vulnerabilities in one area don’t compromise the stability of the broader financial landscape.
How US Financial Institutions Can Prepare for DORA-Like Regulations
First, determine if your organization falls within the scope or DORA compliance. If you have a subsidiary or business activities in Europe and you operate in one of the 22 industries affected by DORA, or if you provide a critical service to a company that falls under DORA’s scope, compliance is mandatory. To navigate these requirements effectively, I suggest hiring an advisory firm to conduct a gap assessment.
Then you’ll need to map out the organization’s critical functions and the suppliers to those critical functions. Although this can take significant time, the outcome will be worth it, both for your organization’s security and for your role as a valued partner. Your knowledgeable input will help to establish consensus among all stakeholders.
Any CISO who voluntarily conducts this mapping of critical functions and the critical suppliers to those functions will be able to analyze where they need to have backup plans for resilience and follow it up with a tabletop exercise.
Until you map things out, it will be hard to decipher what is critical. If you use DORA as a model, you’ll have a terrific framework to map your organization’s functions and suppliers to become more cyber-resilient. You’ll also enable the C-Suite to focus more clearly on the areas of the business that will give your organization competitive advantages.
Why wait for your country to implement stronger regulations to make your organization more cyber-resilient? Use DORA as a guide to get started to reap the long-term benefits.
Want to learn more about DORA? Here are some additional resources:



