As organizations increasingly outsource critical services and embrace migration to the cloud, it’s becoming more crucial that they verify that their third party is using proper access controls – especially when they share sensitive data with that third party. Many organizations unknowingly grant their third parties privileged access, which could be why 70% report that a data breach originated from granting their third parties too much access. Instead of monitoring third-party security controls themselves, they rely on the terms of the contract or the reputation of the third party.
One method organizations should be using to internally assess their third party’s cybersecurity practices overall, including access controls, is with a third-party risk assessment.
Understanding Third-Party Risk Assessment
Third-party risk assessment means evaluating and categorizing all the risks that are associated with working with third parties. These could be suppliers, service providers, consultants, partners, or any other entity that’s connected with your organization.
For example, the marketing agency that’s helping improve your SEO ranking, the digital services provider that’s hosting your cloud storage, and the sustainability expert that helps prepare your ESG report are all third parties.
In today’s interconnected business world, most companies have a large network of third parties, creating a large potential source of third-party risks. You need to consider a whole range of risks, including financial risks, operational risks, cybersecurity risks, and reputational risks.
What Does a Third-Party Risk Assessment Include?
- A review of the nature of the relationship with the third party. This is the foundation of any effective third-party risk assessment. You need to know how critical their services are for your operational continuity; their level of access to your sensitive data; and whether there’s a concentration risk that makes them a linchpin for your supply chain. This equips you to prioritize risks and take decisions about mitigation actions.
- An evaluation of the third party’s compliance history. You’ll want to check their record for compliance with relevant regulations, including regional regulations such as CCPA and industrial regulations like HIPAA or SOX. This helps reveal how seriously they take their regulatory requirements, and gives you a way to assess whether you can trust them to comply with regulations that affect your organization.
- An assessment of the third party’s data security. Data breaches are among the most serious third-party risks that your company could face, so it’s crucial to carefully evaluate third-party data security. You want to verify their adherence to best practices like encryption and multi-factor authentication, and to review their access policies and credentials management, so you can gauge the risks of unauthorized access.
- An evaluation of the third party’s incident recovery processes. Security incidents are almost inevitable, no matter how strict your controls. What matters is how quickly the third party can resolve and recover from it. You want to see robust detection mechanisms and reporting protocols, alongside well thought-out incident recovery plans that are tested and updated on a regular basis.
- An evaluation of the third party’s geographical location. Geography can play a significant role in a third-party risk profile. Some regions are more likely to be affected by natural disasters like earthquakes or hurricanes that can interrupt operations, or face the threat of war or serious social unrest. It’s also important to consider if your third party operates in an autocratic state where authorities might demand access to business data.
- A review of the third party’s roles and responsibilities. You want to make sure that your third parties can meet their contractual obligations, regulatory requirements, and business expectations. Reviewing their roles and responsibilities helps you to identify potential gaps, risks, or conflicts in their duties that could impact security, compliance, or operational efficiency.
- An evaluation of the third party’s existing controls. It’s vital to gain a clear understanding of each third party’s current security, operational, and compliance controls. Weak controls translate into increased risks. Once you know how strong their controls are, you can require them to strengthen their controls, decide whether to change their access to your data or their role in your supply chain, or even choose to terminate the relationship.
Types of Third-Party Risks
Third-party risk assessments are an essential part of identifying and evaluating inherent risk. They enable you to properly identify and mitigate the many risks that could affect your company, helping minimize the number of cyberattacks and operational disruptions that could occur while building greater trust in your third parties.
Third-party risks include:
- Operational risks. Disruptions in your service due to data breaches, natural disasters, outages, supply chain disruptions, overreliance on one vendor, and systems failures can all lead to significant financial loss and harm to your reputation.
- Financial risks. Data breaches, DDoS and ransomware attacks and other security incidents can result in hefty penalties, as well as revenue lost due to subsequent operational disruption.
- Strategic risks. Mergers, suppliers that fall on hard times, over reliance on certain suppliers, and business goals that are misaligned can all create strategic risks for your organization.
- Compliance risks.Third parties must adhere to regulations such as DORA, NYDFS, and the NIS2 Directive, which deal specifically with outsourcing to third parties. Third parties must also adhere to regulations for their specific industry (e.g., EBA and PCI DSS), geographic location, and type of customer as well (e.g. GDPA, CCPA, EBA). Their lack of compliance can expose you to regulatory fines and penalties.
- Reputational risks. Cyberattacks, operational failures, company scandals, and issues with product quality from suppliers can impact your organization’s reputation.
- Cybersecurity risks. Ransomware, DDoS attacks, data breaches and other security incidents can impact your company’s reputation and operations, and cost your company in time, resources and regulatory fines.
Importance of Third-Party Risk Assessment
As third parties and internet infrastructure become increasingly interconnected, it is even more crucial for organizations to conduct frequent third-party risk assessments and have a recovery strategy and contingency plan in place.
The most recent example of this was the Crowdstrike attack that grounded flights, disrupted 911 centers, broadcasts and even the London Stock Exchange. The cause was a defective software update from Crowdstrike that impacted Microsoft Windows operating systems globally. Another example from the UK recently determined that a threat actor exposed the names of names, bank account details, and other information for current, former, and reserve members of the British Army, Naval Service, and Royal Air Force through a third-party contractor. Evidence showed that the payroll service was not doing enough to protect its data from malicious threat actors.
This was the second incident in a year that exposed sensitive information from the UK military.
Regulatory Compliance for Third-Party Risk Assessment
As organizations have increased their reliance on third parties, regulatory bodies have stepped up to include regulations that specifically deal with risks from third parties. These regulations include financial institutions, such as DORA and NFDFS, as well as the health industry, such as HIPAA and HITRUST. They even extend across geographic regions, such as the NIS2 Directive, a EU regulation that includes a broader scope of organizations and industries than DORA.
In addition, these regulatory bodies have also started to develop AI regulations. The AI Act bans the use of certain applications in the EU, such as facial recognition in general, and emotion recognition at work or at school. It also holds companies responsible for any damage incurred by the new technology. The Executive Order on AI aims to protect U.S. citizens against the risks of AI by requiring greater transparency on how the models work and establishing a new set of standards.
A 5-Step Guide to Completing a Third-Party Risk Assessment
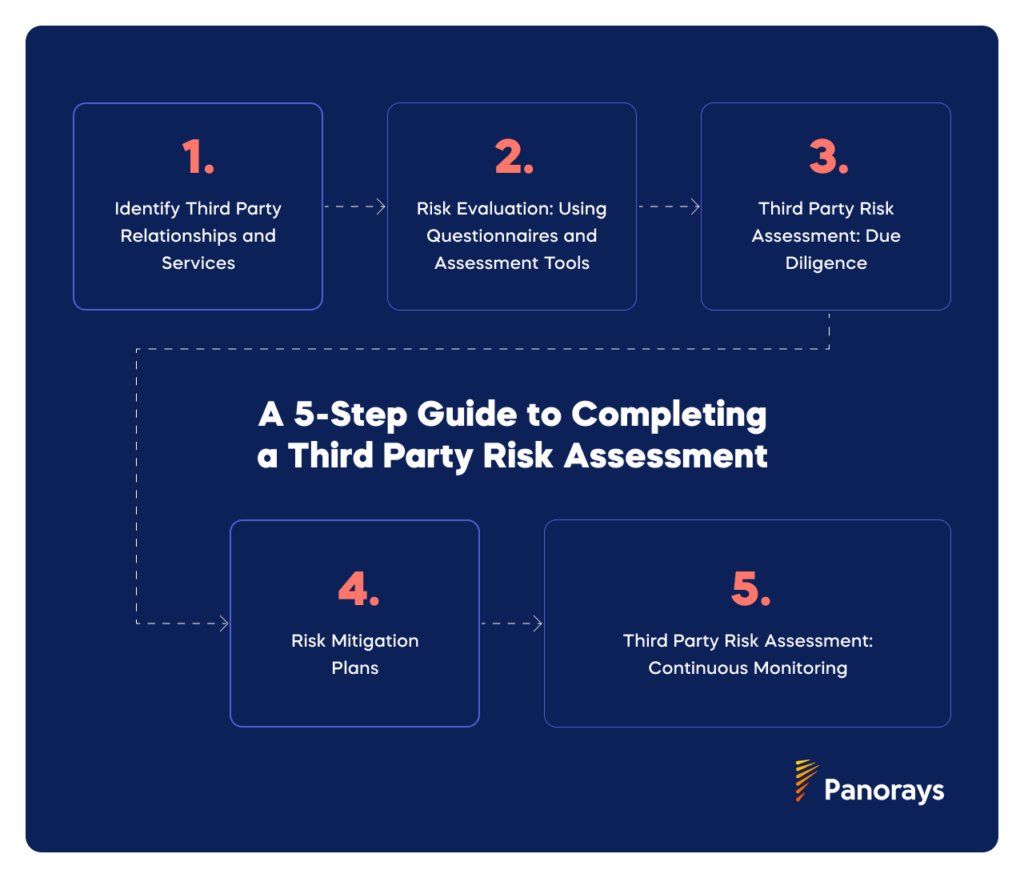
With the challenges of increased regulations, complexity of the supply chain, and lack of internal resources to verify access controls, third-party risk assessments must be a simple and standardized method for organizations to manage third-party risk.
Here are five steps for completing a third-party risk assessment that any organization can use and adapt as needed:
1) Identify Third-Party Relationships and Services
Due to the complexity and dynamic nature of today’s supply chain, nearly 48% of organizations don’t have a comprehensive inventory of third parties they use. This is likely one of the contributing factors for 98% of organizations reporting doing business with a party that has suffered a data breach.
2) Risk Evaluation: Using Questionnaires and Assessment Tools
Organizations have a number of tools in their arsenal to assess third-party risk, including cybersecurity questionnaires, vendor risk assessment questionnaires and risk scoring. These questionnaires should be customized according to the criticality of each business relationship to understand their approach to data protection, adherence to regulation, and how their internal policies align with their risk management approach. In addition, organizations should identify if the third party uses a specific risk management framework.
3) Third-Party Risk Assessment: Due Diligence
Due diligence should evaluate your third party’s approach to issues such as cybersecurity, operational controls, disaster recovery and adherence to relevant compliance and regulations. It may include reviewing compliance certificates, evaluating the vendor’s security controls, and audit reports along with other relevant documents. Proper due diligence helps you to proactively assess the risk posed to your organization, and either decide not to enter the business relationship or take steps to mitigate against the risk.
4) Risk Mitigation Plans
Risk mitigation involves evaluating the current security controls your vendor uses to identify and issues that might need to be addressed. These plans should be implemented according to the criticality of each vendor, with the most critical issues being addressed first. Mitigation strategies might include developing better security controls, adjusting the third party’s internal policies to align with your organization’s risk management, and including a penalty for non-compliance in third-party contracts.
5) Third-Party Risk Assessment: Continuous Monitoring
Due to the dynamic nature of the cybersecurity landscape, IT infrastructure and regulatory compliance, risks evolve continuously, and changes to your IT infrastructure are frequent. As a result, you’ll need to implement third-party risk assessments continuously to ensure they are up-to-date and effective at mitigating third-party risk. In addition, continuous monitoring helps to identify issues early and proactively work to mitigate them.
Best Practices for Third-Party Risk Assessments
Integrating third-party risk management into your organization’s overall risk strategy requires a structured approach. This includes:
- Developing a standardized risk assessment framework that ensures consistency
- Prioritizing high-risk entities for immediate attention and more resources
- Making risk assessments a mandatory part of your onboarding process
- Regularly updating risk assessments as circumstances change
Let’s take a closer look at what’s involved in each of these elements.
Develop a Risk Assessment Framework
A risk assessment framework refers to a structured approach to identifying, analyzing, and managing third-party risks. It’s a good way to standardize the criteria, methodologies, and tools that you use for risk assessments, to ensure consistency for every third party.
With a risk assessment framework, you’ll reduce the chances of missing important information or misassigning risk for a given third party, and systematically evaluate and mitigate potential threats.
Focus on High-Risk Vendors
Today, even small businesses have vast networks of third-party entities which keep changing. Assessing and monitoring risks for all these third parties requires a lot of resources, so it’s inevitable that you’ll take longer to get to some entities.
This makes it vital to prioritize resources for the most critical third parties, so that serious potential threats don’t go under the radar. Otherwise, your organization could experience significant damage while you’re busy investigating a less important source of risk.
Incorporate Risk Assessments Into Vendor Onboarding
You want to make sure that there’s no way that any third party could become part of your business ecosystem without a thorough risk assessment. That’s why it’s crucial to bake risk assessment into your vendor onboarding processes as a mandatory step for any new entities.
Make sure that new companies can’t gain access to your data or be included in your business supply chain before you’ve checked out their compliance, operational, financial, cybersecurity, and other risk profiles.
Regularly Update Assessments
Finally, remember that market conditions are always changing, your third-party relationships keep growing, and malicious actors don’t sit still. The threats that could affect your business are continuously evolving, so your risk assessments can’t stay static.
You need to regularly review and update the processes and considerations so that they are relevant to today’s regulatory environment, vendor operations, and emerging threats, otherwise you could be taken by surprise by unexpected risks.
Collaboration and Communication with Stakeholders
Third-party risk assessments demand collaboration with both internal and external stakeholders. Identifying internal stakeholders such as procurement, legal, compliance, HR, marketing and sales and communicating with them can help you align the security goals of the third-party risk assessment with overall business objectives. In addition, each group of stakeholders may have different priorities to address in the assessment.
Third-party vendors should also understand the goal of the assessment and any deadlines involved. Proper communication is crucial for improving the risk management process and establishing effective mitigation strategies.
Third-Party Risk Assessment Technology and Tools
Various solutions exist today for third-party risk assessments, including automation and AI. A lot of data from third parties can be collected and verified automatically through sources such as compliance reports, cybersecurity assessments, and financial reports. Risk scores can then be automatically assigned based on the data received.
In addition, artificial intelligence (AI) can help identify unusual behavior that points to new or evolving risk, and even predict future behavior based on past security incidents and current cybersecurity practices. With more advanced third-party cyber risk management solutions such as Panorays, it can also accelerate the process of completing and evaluating cybersecurity questionnaires, through AI-generated answers based on past similar questionnaires, and AI-powered validation of answers by cross-referencing them with vendor documents. It can also use AI to map the digital supply chain and identify the KEVs, CEVs and vulnerabilities relevant to each party so that organizations can prioritize and remediate against risk more efficiently.
Third-Party Risk Assessment is a Critical Part of TPRM
A third-party risk assessment is a vital component of any organization’s third-party risk management. By standardizing your assessment, collaborating with both external and internal stakeholders, and including the most recent TPRM tools and technology, you’ll be able to align goals between different parts of your organization while at the same time effectively minimizing risk and building supply chain resilience.
Want to learn more about how you can manage third-party risk across your extended attack surface? Get a demo of our third-party risk management platform today.
Third Party Risk Assessment FAQs
-
A third-party risk assessment is a tool that evaluates the risk a potential new third party brings to your organization. It also evaluates the risk of a current business relationship to continually monitor and update the various stakeholders if the risk has changed.
-
In larger organizations, a third-party risk assessment is developed by the TPRM team, but in coordination with other teams such as sales, the C-suite, HR and procurement. In small to medium companies, a third-party risk assessment is the role of IT, procurement or finance.
-
A third party risk is any vulnerability that a business relationship poses to your organization. These include risks related to compliance, reputation, cybersecurity, strategic, operational and financial.
-
A third-party risk assessment has five steps:
- Identifying the third-party relationships and services in your supply chain.
- Evaluating the risk they pose to your organization using tools such as risk scoring, cybersecurity and vendor risk questionnaires.
- Performing due diligence and assessing the risk posed to your organization and developing different risk mitigation plans in response.
- Identify issues early and proactively working to mitigate them
- Conducting continuous monitoring.
-
As third parties and internet infrastructure become increasingly interconnected, it is even more crucial for organizations to conduct frequent third-party risk assessments and have a recovery strategy and contingency plan in place.
The most recent example of this was the Crowdstrike attack that grounded flights, disrupted 911 centers, broadcasts and even the London Stock Exchange. The cause was a defective software update from Crowdstrike that impacted Microsoft Windows operating systems globally. Another example from the UK recently determined that a threat actor exposed the names of names, bank account details, and other information for current, former, and reserve members of the British Army, Naval Service, and Royal Air Force through a third-party contractor. Evidence showed that the payroll service was not doing enough to protect its data from malicious threat actors.
This was the second incident in a year that exposed sensitive information from the UK military.
-
As organizations have increased their reliance on third parties, regulatory bodies have stepped up to include regulations that specifically deal with risks from third parties. These regulations include financial institutions, such as DORA and NFDFS, as well as the health industry, such as HIPAA and HITRUST. They even extend across geographic regions, such as the NIS2 Directive, a EU regulation that includes a broader scope of organizations and industries than DORA.
In addition, these regulatory bodies have also started to develop AI regulations. The AI Act bans the use of certain applications in the EU, such as facial recognition in general, and emotion recognition at work or at school. It also holds companies responsible for any damage incurred by the new technology. The Executive Order on AI aims to protect U.S. citizens against the risks of AI by requiring greater transparency on how the models work and establishing a new set of standards.
-
Integrating third-party risk management into your organization’s overall risk strategy requires a structured approach. This includes:
Developing a standardized risk assessment framework that ensures consistency
Prioritizing high-risk entities for immediate attention and more resources
Making risk assessments a mandatory part of your onboarding process
Regularly updating risk assessments as circumstances change.



