The Digital Operational Resilience Act (DORA) is reshaping cybersecurity standards for financial institutions across Europe and beyond. True to its name, DORA is focused on enhancing digital resilience, emphasizing the importance of protecting critical functions from both current and emerging cyber threats.
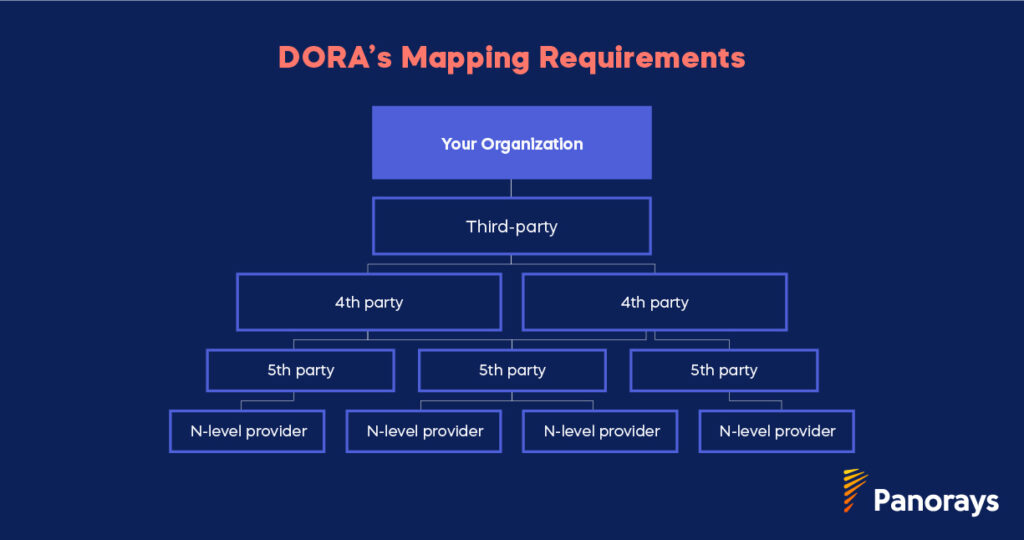
One of its key directives states: “The financial entity must fully monitor the ICT subcontracting chain and document it.” – JC 2023 67, November 2023.
With recent updates to DORA introducing additional requirements, this blog explores these changes and offers guidance on how to effectively address DORA’s demands for third-party cyber risk management.
Key Updates in DORA
DORA’s scope impacts over 22,000 financial entities and ICT service providers across the EU. The regulation applies to banks, insurers, investment firms, and intermediaries. It also applies to their critical ICT service providers, including cloud providers, SaaS vendors, and penetration testing companies.
New Requirements:
The most significant update concerns the Register of Information. A joint report from the European Supervisory Authorities (EBA, EIOPA, and ESMA) revealed that during a dry run, only 6% of submissions using Excel spreadsheets were accepted. As a result, they advise organizations to avoid spreadsheets and use a dedicated platform instead.
Other updates:
- Reporting Deadline: The first Register of Information report is due by April 30, 2025. However, some national regulators require submission as early as March 31.
Without a platform like Panorays, meeting DORA’s reporting requirements will be a challenge. In the following sections, we’ll explain why.
Implications of DORA for Third-Party Risk Management
DORA’s new requirements significantly raise the bar for managing third-party risks in financial ecosystems. These updates emphasize proactive risk assessment, accountability, and robust incident response to ensure digital resilience across the supply chain.
Proactive Risk Assessment
Organizations must conduct thorough due diligence when selecting third-party providers, assess their resilience, and continuously monitor their performance. Regular risk assessments are now essential to identify potential threats enabled by third parties across the supply chain.
Increased Third-Party Accountability
Under DORA, financial entities are fully accountable for risks posed by their ICT providers and their respective subcontracting chains. Regulators will closely examine how these risks are mitigated, making comprehensive third-party risk management a top priority.
Enhanced Incident Response
Financial services providers need clear, DORA-compliant incident response and recovery plans that define procedures, assign roles, ensure effective vendor communication during crises, and are thoroughly tested for real-world effectiveness.
Who Must Comply with DORA?
While DORA primarily targets European financial institutions, its impact extends globally. Businesses worldwide, especially those providing critical services to the EU’s financial sector, may need to comply with its regulations regardless of their headquarters.
Financial Entities
DORA applies to a wide range of financial institutions, including banks, insurance and reinsurance companies, payments and e-money providers, brokers, pension funds, capital market entities, and more.
ICT Third-Party Service Providers
Organizations providing critical services to financial entities, such as cloud providers, software vendors, fraud management tools, collaborative platforms, CRM solutions, and other ICT services, are also within DORA’s scope.
Global Reach of DORA
Even if your business is headquartered outside Europe, compliance may be required if you operate in one of the 22 industries outlined in DORA’s Article 2 or provide critical services to these industries. Businesses with subsidiaries or operations in the EU must take note—DORA’s regulations extend beyond borders.
Which Industries Are Impacted by DORA?
DORA’s regulations aim to enhance digital resilience across the financial ecosystem. Industries affected include:
- Alternative funds (AIFMs)
- Clearinghouses
- Credit organizations
- Crypto services
- Digital payment companies
- Insurance firms
- Investment enterprises
- Payment service providers
- Trading platforms
- UCITS management firms
- ICT third-party service providers
- This includes cloud providers like Amazon Web Service, Microsoft Azure, and Salesforce Cloud as well as software vendors, fraud management providers, collaborative tools, CRM solutions, etc.
This broad scope means that any organization providing essential services to these industries may need to comply, regardless of location.
What Are The 5 Pillars of DORA?
Financial institutions must align with DORA’s five pillars to ensure operational resilience and regulatory compliance. These core requirements address risk management, incident reporting, and operational resilience testing to safeguard critical functions. The five pillars are:
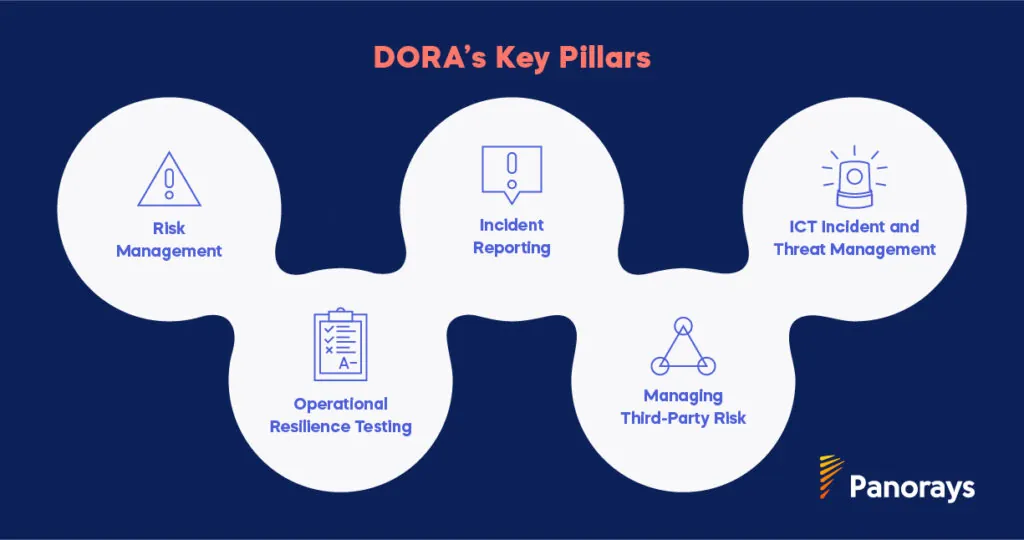
1. Risk Management
DORA’s structured risk management framework is designed to identify, assess, and mitigate risks across financial institutions and their supply chains. While US institutions follow various frameworks like NIST CSF, NIST SP800-53, or the FFIEC guidelines, DORA introduces more comprehensive requirements, particularly regarding the management of third- and fourth-party risks.
2. Incident Reporting
One of DORA’s most rigorous mandates is the requirement for swift and comprehensive incident reporting. It raises the bar by imposing strict timelines and detailed reporting protocols.
3. Operational Resilience Testing
DORA mandates regular operational resilience testing for financial institutions. This includes threat-led penetration testing and stress testing to identify weaknesses in ICT systems. These tests are essential for ensuring that systems can withstand real-world cyberattacks and operational disruptions.
4. Managing Third-Party Risk
DORA places a heavy emphasis on third-party risk management, requiring financial institutions to assess their critical third-party providers and even subcontractors. The process DORA demands can be broken down into five steps:
- Identification of critical or important functions (CIFs) and third-party providers
- Categorization of functions and vendors based on their criticality to the business
- Risk assessment of third-party providers and their subcontractors
- Ongoing monitoring of these providers to ensure compliance and resilience
- Contingency planning to prepare for any disruptions or failures in the supply chain.
5. ICT Incident and Threat Management
DORA’s comprehensive approach to ICT incident and threat management requires financial institutions to have frameworks in place for detecting, managing, and reporting cyber threats with strict timelines.
Can I Use an Excel Sheet for Register of Information Reporting?
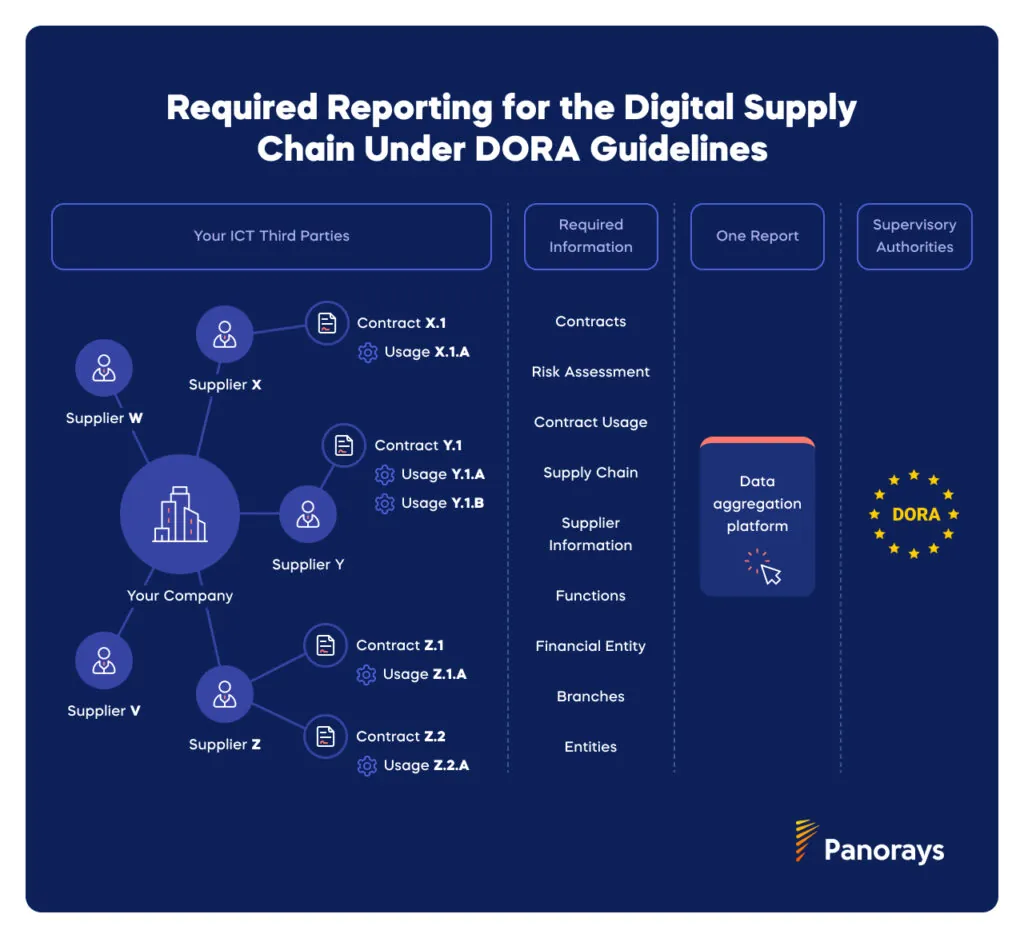
It’s best to avoid using Excel sheets for information reporting, as spreadsheets demand extensive manual effort and increase the risk of errors. The European Supervisory Authorities (EBA, EIOPA, and ESMA) released a joint report that stated in a dry run, that only 6% of submissions that used Excel sheets were accepted.
Another downside of spreadsheets is their lack of scalability.
While a multi-tabbed Excel sheet for DORA compliance can help collect, validate, and aggregate data, regulators recommend using a dedicated tool for this process. We advise choosing a platform that efficiently monitors, documents, and aggregates ICT supplier data. It should also provide automated questionnaire validation and streamlined supplier discovery to enhance compliance and efficiency.
What is DORA’s Register of Information Reporting Deadline?
The European Supervisory Authorities (EBA, EIOPA, and ESMA) have set April 30, 2025, as the deadline for financial entities to submit detailed registers of information about their contractual arrangements with ICT service providers. However, regulators in Ireland have set the deadline as March 31.
How Panorays Can Help You Achieve DORA Compliance
Panorays’ integrated solution simplifies DORA compliance by embedding it into the existing TPCRM process. It enables customers to assess ICT third-party compliance with DORA requirements and monitor their entire contracting chain for cyber and IT risks. This integration ensures full compliance without the need to manage it as a separate, standalone task.
Book a demo to see it in action. You can also learn how DORA compliance can give your organization a competitive edge.



