For several years, supply chains have been growing more extensive. Across every industry, organizations rely on third parties to provide services, components, and/or support for their business operations. As the COVID-19 pandemic showed, if any part of your supply chain is disrupted, it can be impossible for you to meet business obligations.
The biggest risks surround the digital supply chain, which includes all your software providers, IT support, analytics platforms, and more. In today’s modern, interconnected world, third parties can be a back door for malicious actors. Your defenses might be impenetrable, but if a third, fourth, or fifth party has weak security, hackers could breach their services and then follow their connection with you to steal data, affect your business continuity, and more.
As supply chain attacks rise, supply chain security is becoming more important. This involves assessing, evaluating, and acting to mitigate physical and digital risks to your supply chain. In this article, we’ll explore different types of digital supply chain attacks, and explain how to prevent supply chain attacks by using the right technologies and techniques.
Understanding Supply Chain Attacks
A supply chain attack is when a malicious actor infiltrates one of your third parties’ services and uses that to enter your ecosystem. They could target a fourth, fifth, or Nth party, and then progress through the supply chain to breach numerous organizations.
A supply chain attack can impact hundreds of companies. All that matters is that they share a supply chain. The SolarWinds incident, for example, was one of the biggest recent supply chain attacks, affecting as many as 18,000 organizations. The MOVEit supply chain affected hundreds of users around the world, including, ironically, Norton anti-virus software.
The consequences can be astonishing. In 2017, the NotPetya attack on Ukrainian infrastructure resulted in global disruption. The shipping company Maersk suspended worldwide operations; pharma giant Merck couldn’t produce vaccines; a FedEx subsidiary was unable to process orders; and many more large companies were temporarily shut down. Supply chain attacks can even affect national economies — in July 2023, an attack on Japan’s Port of Nagoya disrupted 10% of Japan’s total trade.
Types of Digital Supply Chain Attacks

Supply chain attacks can come in many different forms and target different points along the supply chain. Cyber attacks are the most common type of attacks. They can include:
- Malware and ransomware attacks, using malicious software to penetrate third-party systems.
- Phishing attacks to trick employees into revealing sensitive information and/or access credentials.
- Distributed Denial of Service (DDoS) attacks flood a system with traffic, causing disruptions and downtime that can halt supply chain activities.
There are also many third-party risks. These can include:
- Supplier compromise, where attackers target suppliers that have weaker security measures and use them as entry points to the supply chain.
- Vendor fraud, where unscrupulous vendors provide counterfeit or substandard products, compromising quality and safety.
- Partner network breach, when gaps in your partner’s network expose shared data and systems.
Other types of digital supply chain attacks include:
- Software tampering, where attackers alter legitimate software to introduce vulnerabilities or backdoors that can be exploited later
- Firmware attacks which inject malicious code into hardware firmware to compromise devices at a fundamental level.
- Data manipulation and data tampering, when attackers alter or falsify data within the supply chain.
Key Elements in Preventing Supply Chain Attacks
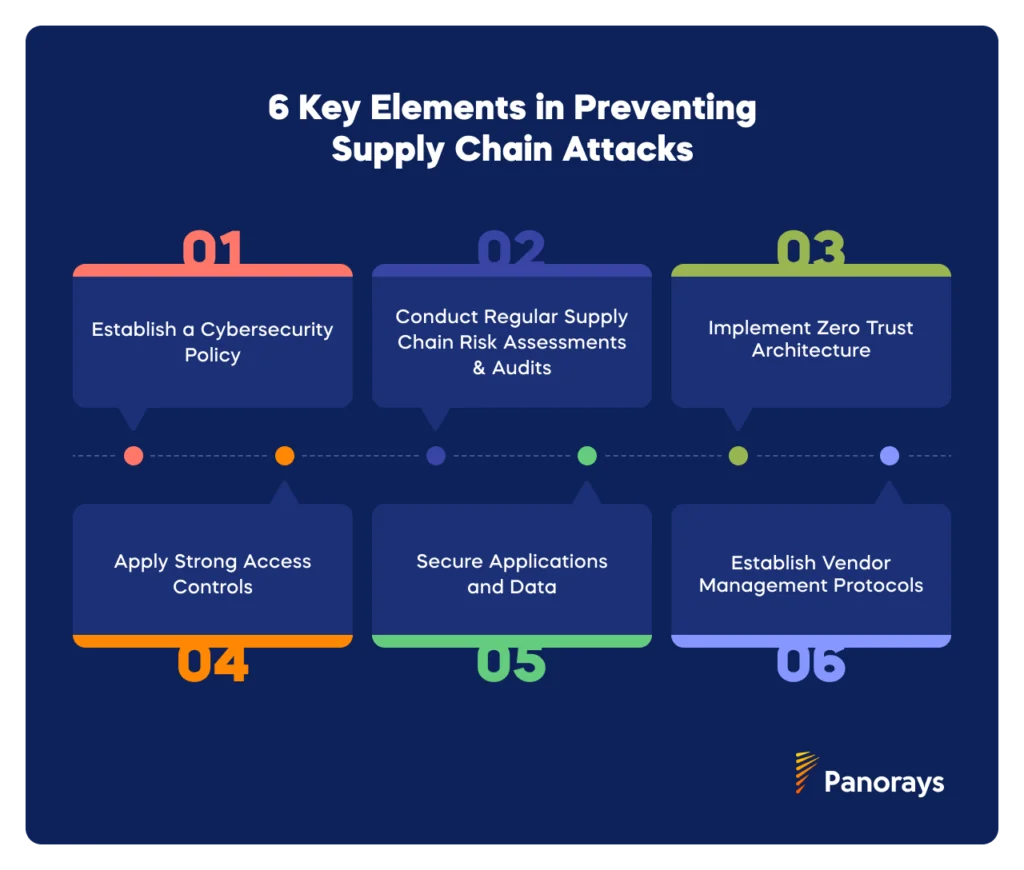
Given that supply chain attacks can cause so much damage, and most organizations have an enormous supply chain attack surface, working out how to prevent supply chain attacks is a priority for every enterprise. Thankfully, the right techniques, tactics, and technologies can go a long way towards strengthening your security posture and limiting your vulnerability.
These include key supply chain risk management practices such as robust vendor management, ongoing risk assessments, and audits, strict access controls, and a zero-trust infrastructure, together with visibility into your entire supply chain. A strong supply chain cybersecurity policy, secure coding practices, and regular application security assessments are also crucial for supply chain security that allows you to sleep at night.
Establish a Cybersecurity Policy for Your Supply Chain
Establishing a cybersecurity policy for your supply chain is the best way to ensure that your third parties follow standardized security protocols. Your policy should set clear guidelines and best practices for managing risks across your supply chain. You’ll also need clear communication channels and incident response plans, to deliver a coordinated response that minimizes the impact of any breach.
The first step is to assess your supply chain’s current vulnerabilities and risks, so you can formulate an effective way to address them. Include both defensive and offensive measures, as well as requirements for regular audits, compliance checks, and continuous monitoring. This ensures that all your third parties meet your security standards.
Defensive measures cover firm backup and recovery procedures, to preserve data integrity and availability in the event of an attack, along with security training and awareness programs that educate users throughout your supply chain on threats such as phishing or social engineering attacks.
Offensive supply chain security measures include frequent penetration testing and red team exercises. These identify potential weaknesses by simulating real-world attacks. You should also deploy honeytokens, which are decoys that alert security teams when they are accessed, so you can detect and respond to intrusions early.
Conduct Regular Supply Chain Risk Assessments and Audits
Regular assessments help you spot vulnerabilities in your supply chain so that you can take steps to address them. You also need to periodically audit security measures across your supply chain, to verify that your controls are effective and are implemented followed by all parties.
Look for issues like weak security policies, outdated software, or insufficient data protection measures. This helps you understand where the most significant risks lie, and prioritize areas that need immediate attention.
It’s important to frequently update your assessments to make sure that they are relevant to changing circumstances and keep pace with evolving threats. For example, if you enter into new partnerships, or upgrade your tech stack. Once you discover any weaknesses or gaps, it’s crucial to address them promptly, whether by enhancing security protocols, replacing vulnerable systems, or providing additional training.
Implement Zero Trust Architecture (ZTA) for Your Supply Chain
Zero trust architecture means adopting a principle of “never trust, always verify” towards every entity, both inside and outside your organization. In practical terms, this means that every user, device, and application that tries to access critical resources has to go through an authentication and authorization process, no matter what/who they are or how recently they last accessed that resource. This way, even if an attacker breaches your supply chain, they’re less likely to be able to move laterally and access your critical systems.
Implementing zero trust architecture requires you to first identify every vital asset, application, and data within your organization. You’ll need to understand where sensitive data is stored, who needs access to it, and how it’s used through your supply chain. Then you can enforce strict access controls, multi-factor authentication, and encryption, and monitor and validate every access request.
Implement Strong Access Controls Across Your Supply Chain
Strong access controls are fundamental to any supply chain security strategy so that only authorized personnel can access sensitive information and systems. It involves using Identity and Access Management (IAM) solutions that enforce robust authentication policies, such as multi-factor authentication (MFA), to verify user identity before granting access.
IAM solutions also help manage user roles and permissions, so that access rights are aligned with each individual’s role and responsibilities in the supply chain. Use them to apply rules like the principle of least privilege and role-based access controls (RBAC).
This way, each user is only given the level of access necessary to carry out their job, which helps restrict access to sensitive data, reduce your attack surface, and limit the potential damage from a compromised account. Just make sure that you regularly review and update your access controls, so that they reflect changes in user roles and operational needs.
Secure Applications and Data
Securing your applications and data is crucial to protect sensitive information, and prevent software from being exploited as a way into the supply chain. Applying encryption, both in transit and at rest, ensures that data can’t be read or used even if it’s intercepted or compromised, which significantly reduces the risk of data breaches.
Another important tactic is to bake in secure coding practices to application development. Shifting left on security helps prevent vulnerabilities that attackers could use. Best practices minimize risks like injection attacks, buffer overflows, and other common security flaws. You should also run regular application security assessments to identify and remediate any potential weaknesses, before they can be exploited in a supply chain attack.
Establish Vendor Management Protocols
You might have the strongest cybersecurity practices in the world, but that won’t help much if your third parties’ cybersecurity is weak. You need to ensure that every vendor meets your high security standards, by creating protocols for assessing and managing vendor security.
These should include sending security questionnaires, reviewing vendor security documentation and policies, and auditing their past incident response performance, to spot any gaps in their security posture that could pose a risk to your supply chain.
Your third-party contracts should include clauses that require specific security requirements, together with obligations for periodic reviews to verify compliance. Continuous monitoring and open communication helps you stay up to date with any changes in your security stance, and detect and respond to emerging risks before they snowball.
Supply Chain Attack Prevention
Supply chain attacks are a serious and increasing threat to your business continuity, revenue, and reputation, making it vital for every organization to invest time and energy into how to prevent supply chain attacks. This includes implementing technologies to help you establish firm access controls, secure coding practices, zero trust architecture, and a robust cybersecurity policy.
But ultimately, your supply chain security is only as strong as that of the weakest member of your supply chain. This means your strategy has to include third-party risk management practices, like ongoing vendor management and monitoring and regular risk assessments and audits.
Panorays can help you manage risk across your supply chain by delivering full visibility into third- and Nth-party risks, through tools like:
- Automated, customized security questionnaires
- External attack surface assessments
- Continuous monitoring and threat detection
- A dynamic Risk DNA score for each vendor to help you prioritize supply chain risks
Ready to secure your supply chain? Contact Panorays to learn more.
Supply Chain Attack Prevention FAQs
-
Tech tools deliver advanced capabilities for protecting your supply chain. For example, AI-powered threat intelligence can proactively identify and mitigate potential supply chain threats; automated systems can streamline risk assessments for third parties; continuous monitoring solutions can spot vulnerabilities in the supply chain before they are exploited by attackers; and third-party risk management platforms can ensure compliance with security protocols across the supply chain.
-
A supply chain attack is when malicious actors manage to breach any member of your supply chain, and then use that breach to gain unauthorized access to other organizations. It could target third, fourth, or Nth party vendors, suppliers, contractors, IT support providers, and more, to find vulnerabilities in their system.
-
/blog/how-to-prevent-supply-chain-attacks/Supply chain attacks can have severe and far-reaching impacts, including financial loss, disrupted business continuity, and damaged brand reputation. A supply chain attack could cause data theft and loss and compromise data integrity, with long lasting effects on business operations. At worst, supply chain attacks can destabilize national, regional, and even global economies.



