Third-party security posture refers to the strength of your third-party cybersecurity and its ability to proactively defend against, mitigate against, and respond to attacks. Since many organizations today give their third parties access to their critical data, the security of these third parties and their ability to handle data securely can directly impact your organization, leading to data breaches, ransomware attacks, and other security incidents.
The Challenges of Building a Strong Third-Party Security Posture
The increase in the outsourcing of third parties for IT services (and their outsourcing to fourth and even fifth parties) has made it more difficult to gain visibility into the supply chain, making it challenging to detect and prioritize risk accordingly. The dynamic nature of IT technologies and cybersecurity risk has also demonstrated the critical importance of continuous monitoring to ensure a strong security posture for both you and your third parties over time. In addition, many organizations lack the resources needed to build a strong third-party security posture, such as TPRM technology and teams.
Why Your Third-Party Security Posture is Important

Having a strong third-party security posture in place delivers many benefits, including:
- Strengthen overall resilience. While a strong third-party security posture minimizes cyber risk in general, it also ensures that your business will be able to continue to offer services in the event of an attack.
- Build your reputation and trust with customers. By assessing whether your third parties meet compliance and have proper access controls in place, for example, you’ll reduce the risk of impact from attacks and build greater confidence in your brand.
- Greater ability to meet compliance. Many regulations and standards, such as DORA, NIST CSF, NYDFS, and the NIS2 Directive focus on risk as a result of the increased outsourcing of services to third-party vendors.
6 Steps to Assessing Your Third Party Security Posture
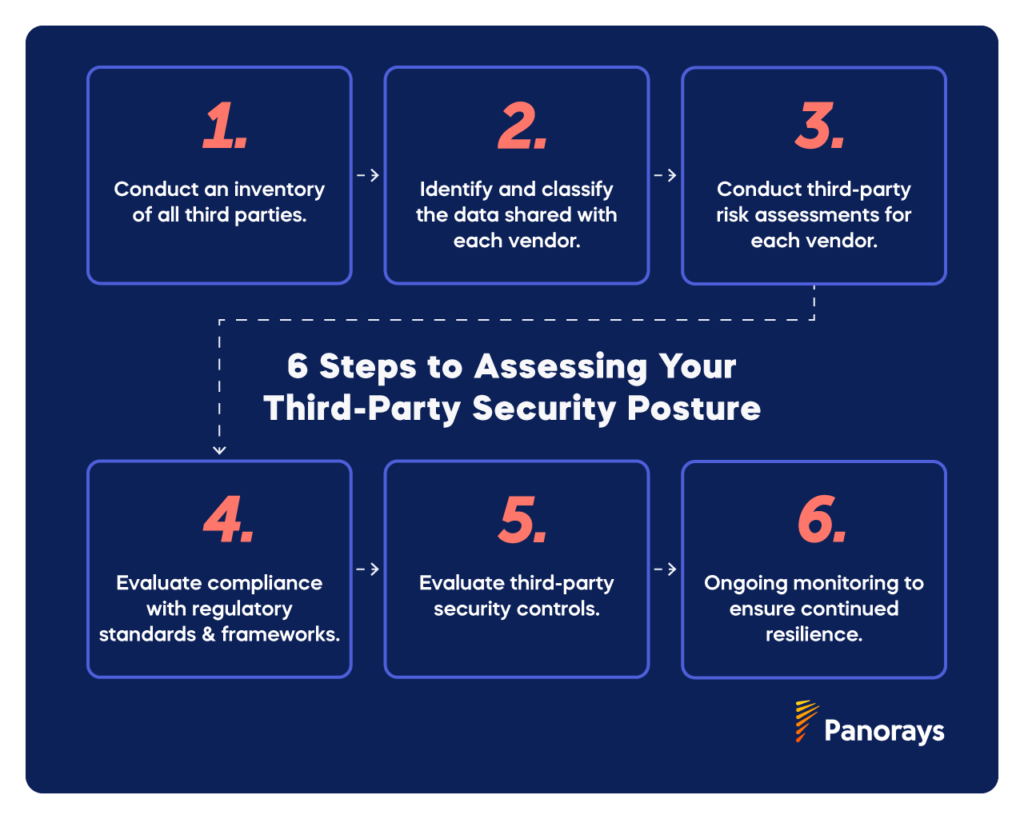
Many of the elements needed to assess your organization’s security posture are the same elements you need for your third-party security posture. However, third-party security posture assessment requires greater visibility into your supply chain and an evaluation of the different levels of potential risk to your organization by each of these third parties.
The steps for third-party assessment include:
1) Take inventory of all third parties.
The first step to assessing your third-party security posture is to understand which vendors are in your supply chain. Since many organizations find it challenging to identify their third parties at any given time, many turn to a third-party risk platform that automatically detects third parties and offers full supply chain visibility.
2) Identify and classify the data shared with each vendor.
Next, you’ll need to understand the different data shared with each vendor and its level of criticality, which will help you determine the level of security needed to protect it. Organizations typically implement security controls that are proportional to the level of criticality so that they can focus their resources on defending against the threats that pose the greatest risk.
3) Conduct third-party risk assessments for each vendor.
This should include a combination of security questionnaires, attack surface assessments, on-site audits, penetration testing, and the third party’s adherence to relevant industry regulations and standards.
4) Evaluate compliance with regulatory standards and frameworks.
Your organization may already do business with third parties that meet specific industry regulations such as GDPR, NYDFS, PCI DSS, HIPAA, and ISO 27001.
As the cybersecurity risk from third parties has increased, however, additional regulations and standards have been developed to address these risks, such as:
- DORA. Although the Digital Operational Resilience Act (DORA) was targeted towards financial institutions in the EU, it is unique in that it also requires compliance from third-party providers of EU financial service organizations (or those that have customers in the EU) and their subcontractors.
- NYDFS. The New York Department of Financial Services (NFDFS) focuses not only on protecting the personal data of New Yorkers, but also organizations that do business with them – as well as their third parties. The security guidelines for third parties include the implementation of multi-factor authentication (MFA), data encryption and the notification of any cyber incidents or data leaks.
- NIS2 Directive. This EU regulation includes a broader scope of organizations than DORA and also emphasizes the importance of proactive risk management such as third party and digital supply chain assessments. It requires organizations to report security incidents such as unauthorized access to services, data breaches and DDoS attacks.
5) Evaluate third-party security controls.
Determine the effectiveness of your third party’s security controls, including internal policies, procedures, and technical controls. It should also evaluate those necessary to comply with regulations and clearly specified in service level agreements (SLAs) and contracts. A proper vendor risk management program should regularly evaluate third-party security controls as well as its incident response preparedness and its contingency plan for continuing business operations in the event of an attack. During this step you may require additional controls to onboard or continue an existing relationship with a new vendor.
6) Ongoing monitoring to ensure continued resilience.
Since networks, systems, and the cybersecurity landscape are constantly evolving, you will need to continuously monitor your security posture to identify any cyber gaps. New attacks, network configurations, and software patches and updates are all examples of situations where new vulnerabilities necessitate changes to your third-party security management.
Why Employee Training and Awareness are Crucial Elements of Security Posture
Whether it’s a vulnerability due to a misconfiguration or a click on a malicious link, most cybersecurity threats are the result of human error. With continuous employee training on the latest social engineering techniques, such as whaling and spear phishing, they can be better equipped to recognize and respond to these threats. Some regulations, such as PCI DSS, HIPAA, and GDPR even require regular employee cybersecurity training to maintain the security standards needed to protect their sensitive data. Those who fail to provide these regular employee cybersecurity training and awareness may be fined.
Employee training and awareness is also an important part of effective incident response, as it includes preparation and an understanding of each employee’s role in the event of a security incident. Regular training also helps facilitate a culture of security-first awareness within your organization that can be influential in dealing with third parties.
The Challenges of Assessing Third-Party Security Posture
Although effective third-party risk management is essential to maintain a robust security posture, assessing your third-party risk presents several challenges. First, the increased reliance on and outsourcing of services to third parties has resulted in businesses switching vendors frequently, making it harder for them to identify vendors and their role in the supply chain at any given point in time. It also demands them to manage vendor risk at scale. Second, the dynamic nature of networks means that a simple upgrade or re-configuration introduces vulnerabilities in your third parties. Finally, although your business may be able to ask vendors questions related to their security policies, having the information in real-time requires continuous monitoring. Not all vendors have the technology and resources for this technology.
As a result of these challenges, many of the current tools companies use to strengthen their security posture against third-party risk today are ineffective.
These include:
- Vendor security questionnaires. Traditional vendor security questionnaires often include hundreds of questions that are not relevant to every third party. For example, software vendors should have different security questions than cloud-based providers. In addition, traditional questionnaires are sent and completed manually, which can be nearly impossible to scale, especially considering that the information received from third parties is only relevant for a certain period of time.
- Security rating services (SRS). Traditional SRSes may adequately assess your third-party attack surface but have no way to assure compliance with your internal security policies and practices. They are also often non-transparent, offering limited insight into the assets found and the security tests conducted. In addition, once an issue is found, they do not typically offer remediation plans.
The Main Components of a Strong Third-Party Security Posture
Since traditional tools are no longer adequate, organizations need tools that can address today’s challenges. Any organization that takes its third-party security posture seriously must use tools that provide:
- Context. A way to identify and measure the different third-party relationships and the level of risk they present. This depends on various factors, such as the type of data shared, who has access, how the data flows, which subcontractors it uses, etc.
- Visibility. Ideally, any security questionnaire that assesses the external security posture of an organization should also verify the organization’s internal security policies. For example, if a third party claims that it adheres to GDPR but a cyber posture assessment found that it does not encrypt its data, it may not actually meet GDPR compliance.
- Engagement. When security gaps arise, you’ll need a collaborative approach to remediate them with your third party. This should include visibility into how the cyber gaps were identified along with the specific steps required to remediate them.
The Challenges of Traditional Cyber Risk Ratings
While a cyber risk rating traditionally assesses your organization’s security posture, it does not include an assessment of its third parties and their individual business relationship with your organization. For example, a cloud service provider would pose a higher security risk to a healthcare organization, with access to highly sensitive personally identifiable information (PII), than a manufacturing company that only conducts business with other manufacturing companies.
In addition, cyber risk ratings typically rely on externally observable information, such as web configurations or known security incidents. This does not properly assess the third parties’ adherence to internal security requirements. Finally, these ratings do not usually take into account the dynamic cybersecurity landscape and nature of networks and systems that are only valid at a certain point in time.
The Need for an Accurate Cyber Risk Rating
Gaining a full picture of your third parties’ digital perimeter with an accurate cyber risk rating is crucial for organizations to align their third parties with their security controls and internal policies to properly mitigate cyber risk today.
| Layer Type | Network and IT | Application | Human |
| Categories | Asset reputation, DNS, cloud, mail server, TLS, web server | Application security, domain attacks, technologies, and exposed services | Responsiveness, employee attack surface, security team, and social posture |
In its mission to deliver the most accurate cyber risk rating on the market today, Panorays’ cyber risk ratings include hundreds of tests in categories of three different layers for each third party, including:
- Network and IT: Identify any flagged company assets, verify DNS configuration against best practices, conduct dedicated tests against cloud infrastructure providers, detect insecure server settings and vulnerabilities, testing TLS infrastructure for vulnerabilities, regulations, and best practices, and check web server security settings and mitigation controls.
- Application. Perform in-depth assessment of applications and services, test resilience against domain hijacking and typosquatting attacks, identify gaps in technology patching and known vulnerabilities (CVEs), and detect potentially dangerous exposed services.
- Human. Test your security team responsiveness over time, check the security awareness, breaches, and digital footprint of company employees, check for dedicated personnel responsible for security team management, and verify that the company’s social network footprints are official.
Performing External Attack Surface Assessments
To ensure its ability to run these tests, however, several elements address this in the Panorays platform, including:
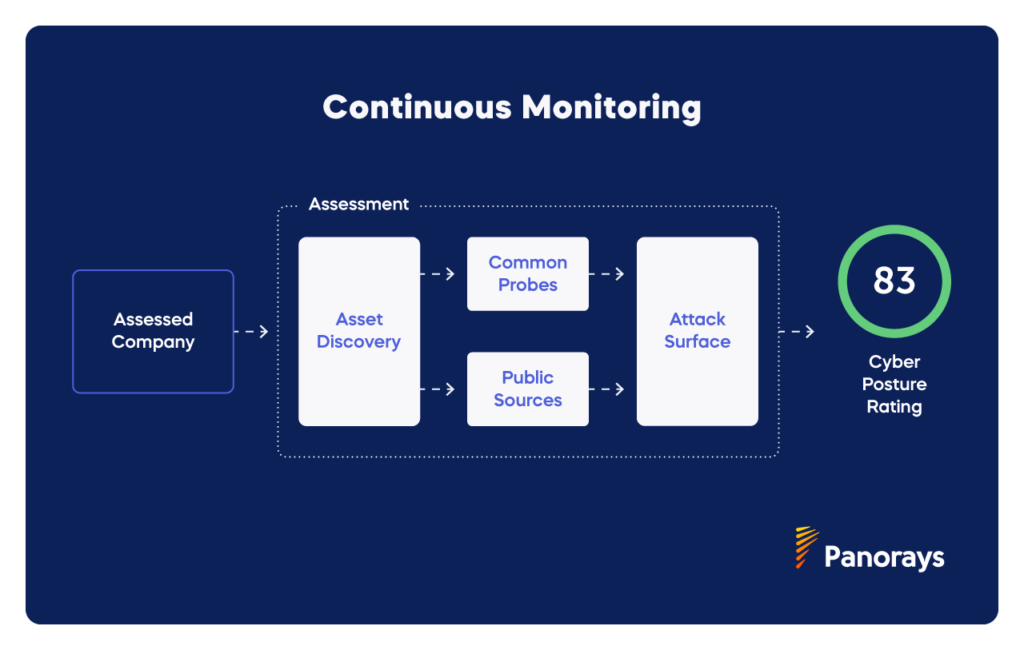
- Asset Discovery Mechanism. Every publicly accessible asset linked to the third party is identified automatically. Only one asset is necessary to get started – usually the primary domain of the company.
- Continuous Monitoring. Ongoing cyber risk ratings ensure greater accuracy, rather than relying on a one-time rating. This includes live alerts of any security incidents or data breaches that have recently affected your third parties.
- Non-Intrusive Assessment. All of the tests on the three layers are performed without engagement with the third party. However the platform allows third party collaboration or the dispute of findings. Assessment data is gathered from both public sources, such as reputation feeds, and common probes, such as sending an empty email to see whether a destination actually exists.
The Cyber Risk Rating Methodology
The Panorays Cyber Risk Rating is composed of the test entity. The results of each test generate both findings and a test rating. An aggregation of all of the test ratings is the Cyber Risk Rating.
| Property | Description |
| Test text | What is tested |
| Finding test | Cyber gap identified |
| Description test | Meaning of cyber gap and possible remediation |
| Severity | Info/Low/Medium/High/Critical |
| Weight | The extent the test affects the Cyber Rating |
| Assets | The assets tested |
Test Risk Rating Calculations
The internal rating score is from 0-100, where:
- 0: This score means that the test was performed and all assets failed.
- 1-99: Some assets passed the test while others failed.
- 100: The test was performed, all assets passed the test and there are no findings.
- N/A: The test could not be performed. For example, no SNMP server was detected so no SNMP test could be run.
In addition, there are several different rating calculations:
- Simple relativity. For example, if 2 out of 10 assets have a finding, the rating would be 80.
- Statistics. For example, if 1 out of 100 assets has a database, the rating would not be 99.
- Company and industry standards. For example, a company with only 20 employees does not have the same size security team as one of 20,000 employees.
Risk Rating Test Weights
Each test is weighed according to different parameters, including:
- Trusted companies. The tests are benchmarked against companies with solid cybersecurity programs, such as Microsoft, Google, Facebook, etc.
- Distribution. The statistical distribution is reviewed within specific industries to allow for a normal distribution for that industry. For example, tests that most companies pass or fail receive lower weight.
- Breached companies. Data is evaluated against companies that have suffered data breaches to understand which tests may have indicated the breach. Higher weight is given to these tests.
How Tests are Developed
Here’s an example of a test and its basic calculation
Panorays wanted to establish a benchmark for medium severity and weight of DNSSEC. After running tests on all companies in its database, it found:
- 97% of companies don’t have DNSSEC
- The average test rating is 1.7 points out of 100
- A trusted company dataset has an average of 1.6 points
As a result, the test found that DNSSEC is not widely adopted among companies and therefore the test was given less weight.
The Final Risk Rating
Final ratings are a reflection of an aggregation of the total tests for each category. resulting in scores for each layer:
Want to learn more about how Panorays can help you strengthen your third-party security posture? Get a demo today!
Security Posture FAQs
-
Security posture in cyber security refers to the ability of your organization to defend, mitigate, and respond to cybersecurity threats. It could include vulnerability management, penetration testing, attack surface management, vendor risk management, and employee security awareness and training. It typically does not include third-party risk management.
-
A security posture assessment is an evaluation of the organization’s ability to adhere to relevant regulations and standards, classify the level of risk faced, and effectiveness of its security controls.
-
You can improve your security posture by improving the security controls and ensuring that it has proper security programs in place that adhere to relevant regulations and standards. Ongoing monitoring is also key as it identifies any cybersecurity gaps that could occur due to changes in network, systems, or the general cybersecurity landscape.
-
The most accurate method for determining an organization’s security posture is with a cyber risk rating that includes both internal and external third-party security assessments. The cyber risk rating should be a reflection of the organization’s security posture at any point in time, rather than a static point.



