Do you remember when the only tools you needed to manage third-party risks were pen and paper? Compared to today, managing your supply chain was almost as easy as child’s play. Today, managing third-party cyber risk is far more complex due to the rapid expansion of cloud infrastructure, SaaS platforms, and deeply interconnected digital supply chains. Panorays’ CISO survey points out that in the past two years, 98% of organizations have had at least one third-party vendor experience a cyberattack. This is far beyond pen-and-paper security!
What is Third-Party Cyber Risk?
Third party cyber risk refers to the cybersecurity threats and vulnerabilities introduced by external vendors, suppliers, service providers, and partners that have access to an organization’s systems, data, or networks. These risks can stem from weak security controls, insecure software, misconfigurations, or breaches within a vendor’s environment and can quickly propagate across interconnected supply chains.
As organizations adopt cloud infrastructure, SaaS platforms, and API-driven integrations, third party cyber risk has become one of the leading causes of data breaches, ransomware incidents, and regulatory exposure.
In a relatively short time span, the business world changed significantly with the transition to cloud infrastructure and SaaS solutions. This shift has made maintaining control and visibility over data security increasingly complex. Moving from on-prem databases to the cloud has introduced fourth, fifth, and even nth parties into the supply chain, further complicating the landscape. Over time, more robust frameworks for managing risks were needed, and it started with GRC.
The shift to cloud infrastructure has increased the complexity of managing third-party cyber risks.
Governance, Risk, and Compliance (GRC) and Early Third Party Cyber Risk Controls Enters the Stage
When GRC emerged in the mid-2000s, it marked a significant shift from basic tools like pen and paper and Excel sheets. Initially, GRC platforms were born from the need to manage general risks associated with third parties. (Do you recall the damage caused by the 2002 port strike on the U.S. West Coast? Importers and their customers faced significant delays followed by financial losses.)
As the risk landscape evolved, GRC platforms began covering wider risks:
- Legal Risks: Helping organizations manage compliance and reduce legal liabilities.
- Financial Risks: Ensuring accurate financial reporting and managing financial risks, especially in response to regulations like SOX in 2002.
- Insurance Risks: Assisting in identifying and mitigating risks that impact insurance policies and claims.
- Operational Risks: Covering a wide array of risks related to the daily operations of a business, including supply chain and human resources.
- Strategic Risks: Aiding organizations in planning for long-term risks that could impact business strategy and growth.
GRC helps businesses identify potential risks, implement controls to mitigate those risks and ensure adherence to relevant laws and regulations.
Over time, businesses grew increasingly reliant on third-party vendors, suppliers, and partners, and the importance of managing third-party risks became evident.
This led to creating specific practices and tools within the GRC framework to address these unique risks. For example, Third-Party Risk Management (TPRM) which focuses on identifying, assessing, and mitigating risks associated with third-party relationships.
Today’s Challenges with GRC
Where GRC platforms fall short is protecting organizations from escalating supply chain cyber risks that go hand-in-hand with today’s increasing complexity and interconnectedness of modern business ecosystems.
For instance, in 2023, cyber-attacks across the U.S. supply chain impacted 2,769 entities. Considering that each entity has access to data from other multiple entities, the risk for any company connected to the supply chain is significant.
The need for real-time data sharing among partners for just-in-time inventory and other logistics has made supply chains more interconnected and vulnerable. Additionally, the globalization and remote collaboration add complexity to maintaining security across different countries with varying regulations and standards.
Security professionals today need comprehensive third-party cyber risk management that goes beyond compliance and offers critical visibility, detection, and alerts about threats across supply chains.
Welcome Third-Party Risk Management (TPRM)
By the early to mid-2000s, organizations were more dependent on third parties such as vendors, suppliers, and service providers. Their vulnerabilities posed significant risks and led to TPRM developing as a specialized field.
Think back to the chaos the U.S. railroad workers’ strike caused in 2003. Companies reliant on transporting goods by train had to scramble to find alternate, more expensive methods to move their goods.
The world needed structured methods to proactively manage third-party risks. TPRM provided the framework for assessing, prioritizing, and mitigating these risks.
TPRM enhanced the traditional risk management approaches by specifically addressing the challenges introduced by the growing complexity and interdependence of third-party relationships. Unlike GRC, which provides a broader risk management framework, TPRM zeroed in on the unique risks posed by third-party vendors, offering tools for more detailed assessment and mitigation tailored to these specific relationships.
Key components of TPRM include:
- Vendor risk assessments
- Risk mitigation strategies
- Contract management
- Vendor performance tracking
According to Deloitte, 60% of today’s organizations work with over 1,000 third parties. These numbers will only rise as business ecosystems continue to expand and grow more complex.
Third Party Risk Management Challenges
Despite 87% of retail businesses viewing TPRM as a strategic priority, many say it’s challenging to maintain effective TPRM models. In fact, during COVID, 56% felt they avoided major third-party incidents due more to chance than through their robust TPRM practices.
Furthermore, only 35% have successfully integrated their TPRM programs with other risk and business functions, and 77% believe an overhaul of their operating model is urgently needed.
Behind every B2C is at least one supplier, so B2B companies need to be vigilant with their third-party defenses.
Two other issues CISOs face with only TPRM are lack of remediation prioritization with third parties and maintaining visibility over all third parties.
Next on the Scene: Security Rating Service (SRS)
SRS platforms provide a high-level view of an organization’s security posture using public data.

Security Rating Services (SRS) were introduced in 2013 to manage cybersecurity risks more systematically and transparently.
They provided clients and others with an independent, high-level view of their organization’s security posture using public data from global threat intelligence feeds. Most SRS platforms run Attack Surface Assessments on discovered digital assets to understand an organization’s security posture. Essentially, SRS reports make it simple to compare one company’s security profile with others while also providing an overall cybersecurity score.
Here are three reasons SRS was needed:
- Increasing Cyber Threats: The frequency and sophistication of cyber attacks were escalating, making it essential for organizations to have a clearer understanding of their security posture as well as their vendors’.
- Third-Party Risk Management: Businesses were becoming more interconnected and organizations needed a way to assess and monitor the cybersecurity risks associated with third parties.
- Objective Benchmarking: Leaders wanted an objective, standardized method to measure and compare the cybersecurity performance of different organizations, similar to how credit ratings are used in the financial industry.
Security Rating Services are essential for any organization looking to defend its market position or reputation. They help organizations understand their security posture relative to others and take necessary actions to improve their ratings based on third-party evaluations. However, SRS is not meant for deep security testing or as a substitute for managing your attack surfaces.
The Challenges of SRS
Because SRS relies on publicly available data and external threat intelligence feeds, the information could be inaccurate, incomplete or unverifiable. There is potential for misleading ratings or not getting an accurate understanding of a company’s security profile. More concerning is that reducing a complex security program to a single metric with security ratings can lead CISOs to overlook the comprehensive view that is needed.
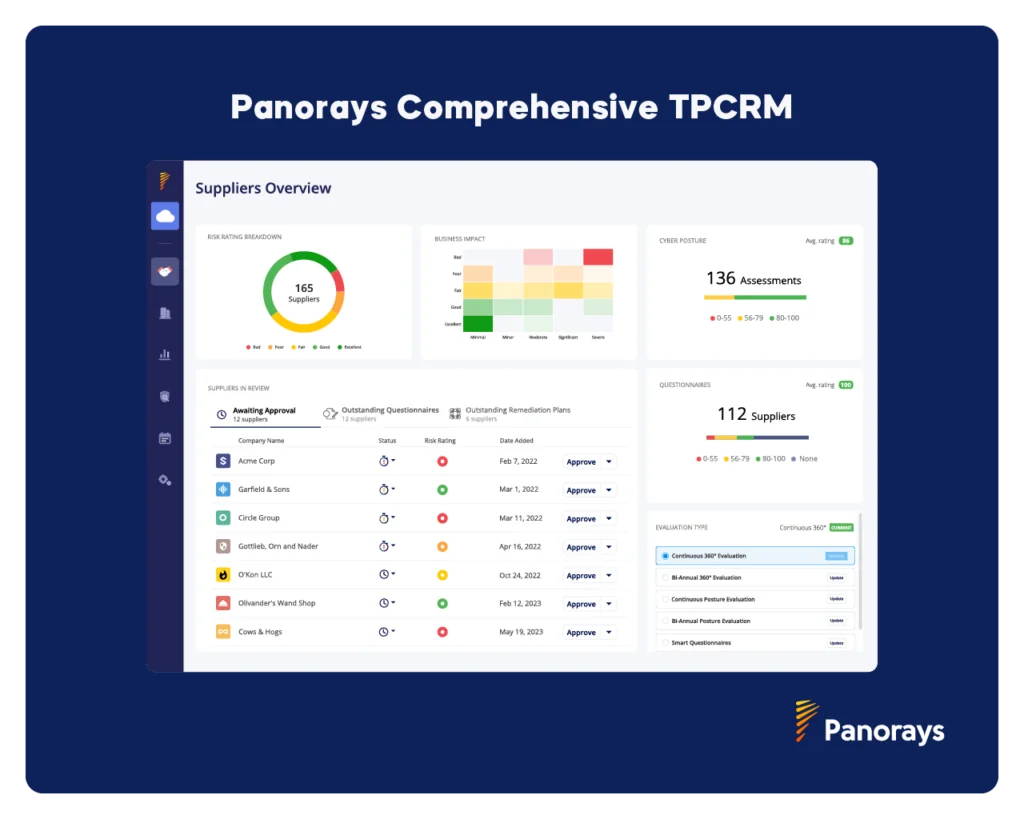
And Now There’s Third-Party Cyber Risk Management (TPCRM)
TPCRM platforms offer real-time visibility and proactive management of third-party cyber risks.
By the 2010s, businesses were increasingly moving their data to the cloud as part of a broader digital transformation. This shift to cloud storage was a major change, affecting how companies managed and secured their information.
As organizations adapted to this new environment, they faced new challenges in third-party risk management, leading to the development of Third-Party Cyber Risk Management (TPCRM) solutions.
TPCRM emerged to address these challenges by providing enhanced visibility and control over the security risks associated with third-party relationships in this evolving digital landscape with:
Comprehensive Risk Visibility: To help CISOs identify and prioritize risks effectively, TPCRM provides a complete view of cyber risks across all third-party relationships and discovers hidden 4th and nth parties.
Enhanced Security Posture: By proactively managing third-party cyber risks, organizations can significantly strengthen their overall security posture and resilience against cyber threats, especially through continuous cyber assessments and customizable questionnaires tailored to assess the inherent risk of each relationship and align with the company’s risk tolerance.
Regulatory Compliance: TPCRM helps organizations comply with regulatory requirements related to third-party risk management, reducing legal and regulatory risks.
Operational Efficiency: Streamlined processes and automated workflows in TPCRM platforms improve efficiency in assessing, monitoring, and responding to third-party risks.
Risk-Based Decision Making: TPCRM enables informed decision-making by providing data-driven insights into third-party risks, supporting strategic business initiatives.
AI Integration: AI enables third-party risk management by automating and scaling cyber risk programs, helping protect against breaches. It supports CISOs in setting priorities and allocating budgets, highlighting its role in compliance and risk quantification for mitigating third-party risk.
This diagram illustrates how TPCRM checks all the boxes:
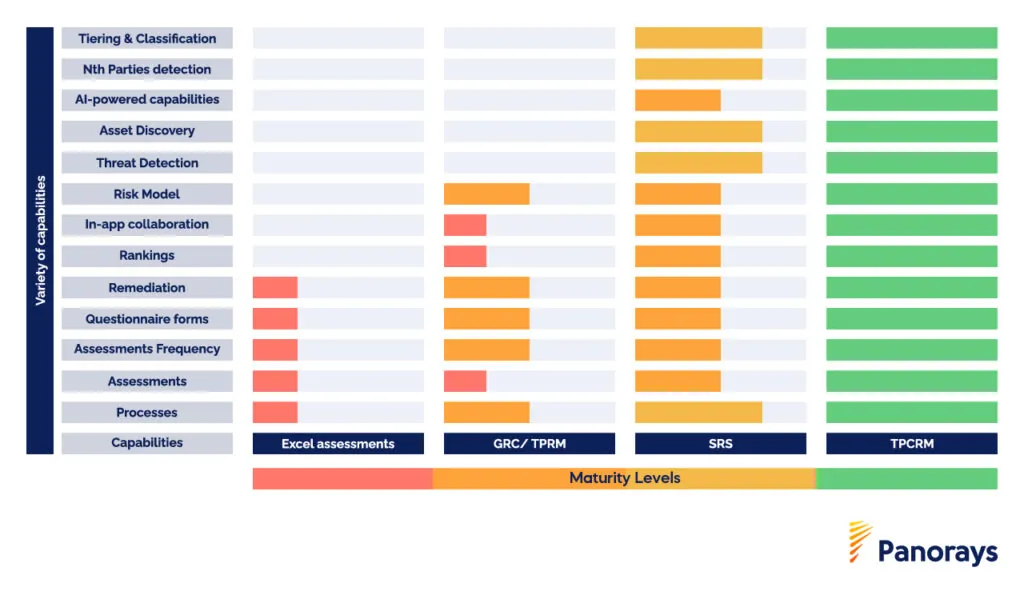
You can see how TPCRM collectively enhances an organization’s resilience and security. When you add in the expanded risks associated with harnessing AI, a TPCRM like Panorays Risk DNA, provides the constant vigilance that lets CISOs sleep better. Panorays Risk DNA conducts continuous, personalized assessments of the vulnerabilities resulting from each third-party connection and clearly portrays the potential risks. In the words of one customer:
Secure Tomorrow’s Threatscape with TPCRM
The threats facing companies connected on the supply chain grow daily because of the risks third parties bring to their relationships. While GRC and TPRM launched a framework approach to third-party security, TPCRM goes beyond these frameworks by offering deeper insights and proactive risk management tailored to today’s complex digital landscape. TPCRM delivers the most comprehensive risk visibility and security measures to better equip CISOs.
“…you can get a very clear view of what risk we’re carrying at this moment in time based on what’s been pumped into the system.”
– Panorays customer
To see how Panorays can help you quickly and easily manage third-party risk in your digital supply chain, click here.
TPCRM FAQs
-
Third-Party Cyber Risk Management (TPCRM) is a cybersecurity-focused approach to managing risks introduced by vendors, suppliers, and partners with access to an organization’s systems or data. It provides continuous monitoring, real-time visibility, and risk prioritization across third- and nth-party relationships to strengthen security and resilience.
-
Governance, Risk, and Compliance (GRC) is a broad framework for managing organizational risks and regulatory compliance, while Third-Party Risk Management (TPRM) specifically focuses on risks associated with external vendors and partners. TPRM operates within or alongside GRC but provides deeper processes for assessing, monitoring, and mitigating vendor-related risks.
-

TPCRM platforms offer real-time visibility and proactive management of third-party cyber risks. 

SRS platforms provide a high-level view of an organization’s security posture using public data. 
TPCRM platforms offer real-time visibility and proactive management of third-party cyber risks. 
Third-party risk management focuses on assessing and mitigating risks from vendors and service providers that directly access systems, data, or operations. Supply chain risk management is broader, addressing disruptions and risks across the entire supply network, including logistics, manufacturing, and geopolitical factors.

SRS platforms provide a high-level view of an organization’s security posture using public data. 
TPCRM platforms offer real-time visibility and proactive management of third-party cyber risks. 



