Vendor risk management encompasses a wide range of third-party risk that includes operational, financial, reputational, regulatory, strategic, geopolitical and cybersecurity risks. If these third parties fail to uphold their end of the deal when it comes to security, or if they’re the victim of a cyberattack, it could impact your organization directly. Many of these risks also impact a company from multiple angles.
5 Key Things You Need to Know About Vendor Risk Management
1. Vendor Risk Management (VRM) is Essential in Today’s Interconnected Ecosystem
As businesses increasingly rely on third-party vendors, VRM helps identify, assess, and mitigate risks—spanning cybersecurity, financial, operational, reputational, and compliance concerns. Proactive VRM safeguards digital ecosystems by ensuring vendors meet security expectations before, during, and after engagement.
2. Cyber Supply Chain Breaches Are on the Rise
With over 60% of data breaches now involving third-party vendors (e.g., Change Healthcare), businesses must adopt real-time, proactive VRM to ensure continuous resilience. Without it, vulnerabilities in vendor systems can become direct entry points for cyberattacks.
3. VRM is a Lifecycle-Driven Process with Three Core Stages
It involves:
- Onboarding (due diligence and risk assessment)
- Ongoing monitoring (continuous security evaluation)
- Offboarding (secure termination and data handling)
- Managing vendors throughout their lifecycle helps ensure compliance and reduce long-term exposure to risk.
4. Vendor Risk Management Programs Deliver Broad Organizational Benefits
Effective VRM reduces operational disruptions, supports regulatory compliance, improves visibility, increases efficiency through automation, and lowers costs by avoiding breaches and fines. It also builds trust among stakeholders by demonstrating a commitment to third-party security.
5. Key Components Include Assessment, Categorization, Contracts, Monitoring, and Incident Response
A robust VRM framework includes detailed due diligence, risk-based vendor classification, strong contractual agreements, continuous monitoring, and coordinated incident response planning. These components work together to create a repeatable, scalable, and defensible risk management process.
What is Vendor Risk Management (VRM) in 2026?
Vendor risk management (VRM) is essential for identifying, assessing, and mitigating risks posed by third-party vendors. As organizations expand their digital ecosystems, the reliance on external providers for software, infrastructure, and services introduces increasing security and compliance risks.
Cyberattacks targeting supply chains are on the rise, with over 60% of data breaches now involving third parties. In 2023, the Change Healthcare cyberattack disrupted medical billing nationwide, delaying patient care and causing widespread financial strain. These incidents underscore the need for proactive, real-time vendor risk management to prevent disruptions and protect sensitive data.
In 2026, organizations must adopt AI-driven risk assessments, automated compliance tracking, and continuous security monitoring to ensure vendors meet cybersecurity standards. A proactive, technology-driven approach is no longer optional—it’s a necessity.
What is a Vendor?
A vendor is typically a third-party organization that sells a product, service, or piece of equipment that your business needs to operate. An effective third-party risk management program needs to focus on multiple layers of protection.
Types of Vendor Risk
Each third-party vendor, upon being connected to your organization, is going to carry some level of cybersecurity risk. Risks could be financial, operational, legal, regulatory, reputational and even geopolitical.

If a vendor fails to uphold their end of the deal in matters of security (e.g. they don’t implement proper security controls or data encryption), or if they’re the victim of a cyberattack, it could impact your organization directly. An effective risk assessment, as part of a greater vendor risk management plan, strives to identify and fix these potential failure points long before they become a problem.
Why is Vendor Risk Management Important?
Even if your own internal security measures are strong, integrating third-party vendors who don’t follow best practices into your IT infrastructure can pose a big risk to your organization. This is especially true when those vendors handle confidential, sensitive, proprietary, or classified information. Vendor risk management provides a documented strategy that helps your organization streamline the VRM process.
An effective VRM program should:
- Mitigate third-party risk. A process for accurately assessing the risk of any new vendor, reducing your organization’s risk exposure over time.
- Minimize operational disruptions. A clear process for vendor risk management ensures that each component of your organization knows its role in evaluating third-party risk so that no processes are overlooked or skipped. This ongoing, proactive approach to vendor risk helps your organization stay ahead of any breach, attack or security incident, ensuring business continuity.
- Provide better ability to meet regulatory compliance. A streamlined process for onboarding vendors that includes due diligence makes it easier to evaluate vendor compliance and decide whether or not to enter into a new business relationship or employee measures to remediate the risk.
- Ensure greater transparency. Since information on vendor risk is open and available across the organization, executive leadership can work together with your security and business teams to evaluate the potential impact of risk across the entire vendor ecosystem.
- Increase operational efficiency. Automating the vendor risk management process means faster risk assessments and optimized workflows, allowing for greater collaboration across teams. A good vendor risk management program also ensures that vendors are paid on time and for their products or services.
- Enhance security. Third-party vendors can be a major security risk if not properly vetted and monitored. Implementing continuous monitoring, access controls, and zero-trust security models helps organizations minimize vulnerabilities within the supply chain. A strong VRM program also ensures that vendors apply encryption, secure authentication methods, and compliance standards to protect sensitive information from breaches or cyberattacks.
- Reduce costs associated with security failures. A well-structured vendor risk management program helps organizations avoid costly breaches, regulatory fines, and operational downtime. Proactively addressing vendor risks prevents financial losses caused by security incidents or compliance failures. Additionally, by optimizing vendor contracts and ensuring third parties meet security and regulatory standards, businesses can avoid unexpected expenses and improve long-term financial stability.
- Allow for more effective use of time and resources. It’s easier to address potential risks than to deal with them after they occur. A strategic and detailed approach to the vendor risk assessment process also frees up your management and executive teams to focus on business growth, rather than having to stop in the middle of their current projects to focus on onboarding, compliance, or managing risks.
Key Components of a Vendor Risk Management Program
A strong vendor risk management (VRM) program is built on a structured approach that ensures vendors meet security, compliance, and operational requirements. Effective VRM programs incorporate thorough risk assessments, continuous monitoring, and clear contractual obligations to safeguard organizations from potential security threats. By adopting modern tools that automate vendor risk management, businesses can proactively mitigate risks and build stronger vendor relationships.
Vendor Assessment
Before onboarding a vendor, organizations must conduct comprehensive due diligence to evaluate potential security risks. This includes reviewing the vendor’s security policies, compliance certifications, and past risk incidents. Businesses should also assess financial stability, reputation, and regulatory adherence to ensure the vendor aligns with their security and operational standards. Utilizing security questionnaires and vendor risk assessment tools can help organizations gain deeper insights into a vendor’s risk posture. Proper vendor assessment helps businesses make informed decisions while reducing exposure to unreliable or high-risk third parties.
Risk Categorization
Not all vendors pose the same level of vendor risk, so organizations must classify them based on their potential impact on security, compliance, and operations. Critical vendors—those handling sensitive data, processing financial transactions, or supporting core infrastructure—should be subjected to more rigorous security evaluations and monitoring. Low-risk vendors, such as office supply providers, may require less intensive oversight. By categorizing vendors appropriately, businesses can prioritize resources effectively and ensure the highest level of scrutiny is applied where it matters most.
Continuous Monitoring
Vendor risk management is not a one-time process; it requires ongoing monitoring to detect emerging risks. Organizations should establish continuous risk assessment protocols, including real-time security monitoring, periodic compliance reviews, and automated alerts for policy violations. Security ratings and threat intelligence tools that automate vendor risk management help businesses track vendors’ cybersecurity posture and detect potential vulnerabilities before they escalate into breaches. By adopting a proactive monitoring approach, businesses can identify threats early and take corrective actions to maintain compliance and security.
Contract Management
Vendor contracts should clearly define security expectations, compliance requirements, and termination clauses to protect organizations from third-party risks. Contracts must specify data protection policies, regulatory obligations, and liability measures in the event of security failures. Strong contract governance ensures that vendors remain accountable and adhere to established security standards throughout the business relationship. Including service level agreements (SLAs) that outline security and compliance responsibilities further strengthens vendor accountability and risk management effectiveness.
Incident Response Planning
A well-defined incident response plan is essential for addressing security breaches, compliance violations, or service disruptions caused by third-party vendors. Organizations should establish clear protocols for reporting, investigating, and mitigating vendor-related incidents. This includes escalation procedures, forensic analysis processes, and corrective action plans to minimize the impact of security failures. Businesses should also require vendors to maintain their own incident response plans and participate in coordinated response efforts when cybersecurity threats arise. Having a structured response framework helps reduce downtime, contain risks, and ensure regulatory compliance in the event of a security incident.
The Vendor Risk Management Framework
A vendor risk management framework is the system an organization uses to create its defense program for vendor risk. It is the first step a CISO should take before deciding to invest in resource-draining vendor risk management software and solutions. The vendor risk management framework you choose should be based on your risk appetite, industry, compliance requirements and reliance on third parties, as well as the resources you are able to dedicate to vendor risk management. Although first developed for critical infrastructures, the NIST Cybersecurity Framework is the most widely adopted risk management framework by leading global organizations of all sizes and industries today.
How to Automate Vendor Risk Management
Automation in vendor risk management helps teams scale VRM without sacrificing consistency, speed, or oversight. Instead of relying on manual questionnaires, spreadsheets, and periodic reviews, automated VRM uses technology to identify vendors, assess risk, track compliance, and monitor changes continuously throughout the vendor lifecycle.
What Automation Means in VRM
In VRM, automation means using software and integrations to complete repetitive, time-consuming tasks with minimal human effort while maintaining clear workflows, documentation, and accountability.
Automated VRM typically includes:
- Collecting and normalizing vendor data from multiple sources
- Scoring vendors based on risk signals and criticality
- Triggering questionnaires and follow-ups automatically
- Flagging policy violations or changes in vendor posture in real time
- Routing remediation tasks to the right owners with deadlines and audit trails
Manual vs. automated VRM
Manual VRM is often point-in-time and document-heavy. Teams spend time chasing vendors for responses, updating spreadsheets, and trying to keep reassessment schedules on track. Automation standardizes those steps and turns VRM into a continuous process, so risk scoring, follow-ups, and monitoring happen consistently without relying on someone to remember the next step.
Why automated VRM it matters in 2026
Vendor ecosystems are larger and supply chains are deeper, so risk can change faster than periodic reviews can catch. Automation helps you keep pace by surfacing new exposures, vulnerabilities, and compliance gaps as they emerge, and by routing the right actions to the right owners faster.
Key VRM Processes You Can Automate
Most organizations start by automating the highest-volume, highest-friction parts of VRM.
- Vendor discovery and inventory management. Automatically identify and maintain a current vendor list by pulling data from procurement, finance, IT, and contract repositories.
- Risk scoring and vendor tiering. Assign risk ratings based on factors like data access, business criticality, security posture signals, and regulatory impact.
- Questionnaires and evidence collection. Send the right assessment based on vendor type and criticality, track completion, and standardize evidence requests.
- Compliance checks and control mapping. Map vendor controls to internal policies and external requirements, then track gaps and remediation progress.
- Continuous monitoring. Monitor vendors for changes in security posture, exposed assets, vulnerabilities, breach indicators, and other risk signals.
- Alerts and escalation workflows. Automatically notify the right stakeholders when risk thresholds are exceeded or when a vendor’s status changes.
Top Benefits of Automating Vendor Risk Management
Automation improves both speed and quality across the VRM program.
- Faster assessments. Reduce onboarding delays by accelerating vendor intake, categorization, and due diligence workflows.
- Fewer manual errors. Replace spreadsheets and inconsistent tracking with standardized workflows, required fields, and audit-ready documentation.
- Continuous, real-time monitoring. Move beyond point-in-time assessments to detect risk changes when they happen, not months later.
- Better risk prioritization and faster remediation. Focus resources on critical vendors and the most urgent issues, then track remediation progress with clear ownership.
Typical Automation Tools and Capabilities
Modern VRM automation platforms commonly include these capabilities:
- Real-time risk scoring. Dynamic risk ratings that update as new security, business, or compliance signals appear.
- Continuous vendor monitoring. Ongoing tracking of vendor posture changes, exposed systems, vulnerability indicators, and emerging risk events.
- Automated compliance workflows. Built-in workflows for policy alignment, evidence collection, exception handling, and reassessments.
- Integrations with procurement and procure-to-pay systems. Sync vendor records, automate intake and approvals, and reduce shadow vendors by connecting VRM to how vendors are actually purchased and onboarded.
The 3 Stages of the Vendor Risk Management Lifecycle
Vendor risk does not begin and end with onboarding. Risk levels change over time based on a vendor’s access, data handling practices, business changes, and evolving threat landscapes. That is why vendor risk management must be applied continuously across the entire vendor lifecycle.
The vendor risk management lifecycle is typically divided into three core stages:
1. Onboarding
The onboarding stage focuses on due diligence before a vendor is granted access to systems, data, or operations. This is where organizations assess whether a vendor meets security, compliance, and operational requirements.
Key activities during onboarding include:
- Conducting initial vendor risk assessments and security questionnaires
- Evaluating compliance with relevant regulations and standards such as ISO 27001, SOC 2, HIPAA, or GDPR
- Reviewing data handling practices, access controls, and incident response capabilities
- Assigning an initial risk rating based on criticality and inherent risk
Strong onboarding controls help organizations prevent high-risk vendors from entering the ecosystem without proper safeguards.
2. Ongoing Monitoring
Once a vendor is approved, risk management must continue throughout the relationship. Vendors may change their infrastructure, introduce new technologies, or experience security incidents that impact their risk posture.
Ongoing monitoring typically includes:
- Continuous security posture monitoring and risk scoring
- Periodic reassessments and compliance reviews
- Monitoring for breaches, vulnerabilities, regulatory changes, or financial instability
- Tracking remediation progress when issues are identified
Continuous monitoring enables organizations to detect emerging risks early and respond before they escalate into operational disruptions or data breaches.
3. Offboarding
Vendor risk does not disappear when a contract ends. Improper offboarding can leave behind exposed credentials, retained data, or unresolved access permissions.
Effective offboarding processes should ensure:
- Secure termination of system access and credentials
- Verified deletion or transfer of sensitive data
- Documentation of contract termination and compliance obligations
- Final risk review to confirm no residual exposure remains
A structured offboarding process helps organizations prevent long-term exposure and ensures former vendors cannot become future security liabilities.
By managing vendors across all three lifecycle stages, organizations can reduce blind spots, maintain compliance, and build a more resilient third-party risk management program.
The 3 Stages of the Vendor Risk Management Lifecycle
Since the level of security risk also varies widely depending on additional factors such as the type of organization, industry, third-party relationship, technologies, and relevant regulations, organizations need to continue to employ third-party vendor risk management throughout the lifecycle of the business relationship.
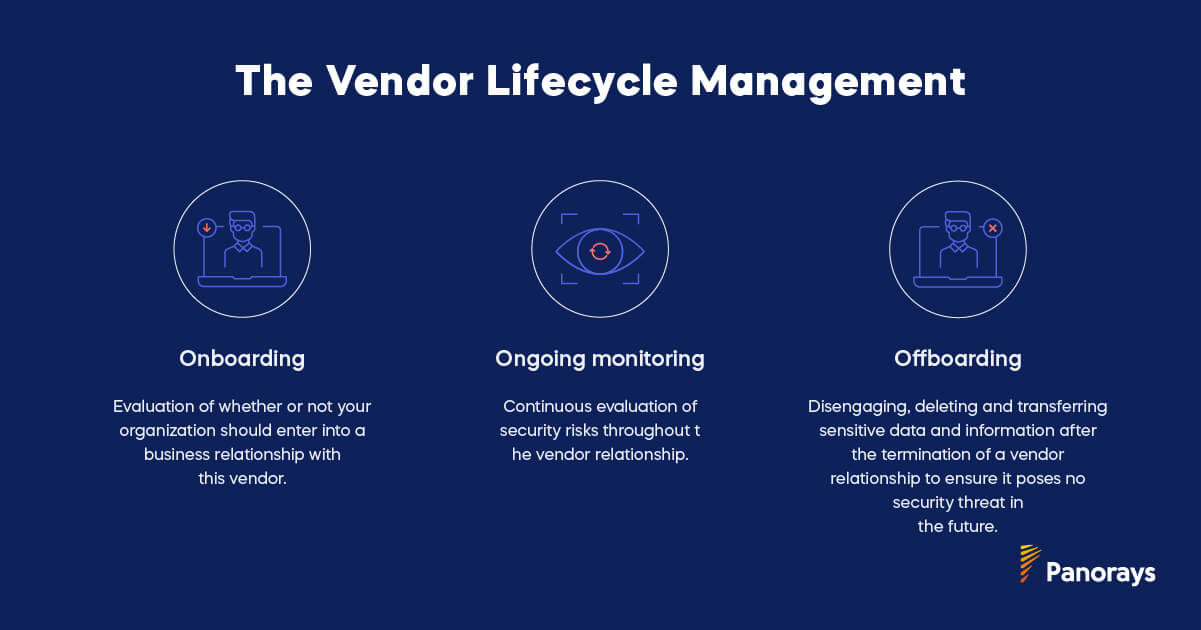
These stages can be divided into three separate periods:
- Onboarding. Due diligence is conducted at the beginning of the vendor relationship to evaluate whether or not the business should enter into a relationship with the third party in question.
- Ongoing monitoring. Security risks are regularly evaluated during the vendor relationship to ensure the third party is applying the appropriate security controls to meet the relevant regulations and standards.
- Offboarding. Vendors who terminate their relationship with your organization must have a process for disengaging, deleting and transferring sensitive data and information formerly shared with your organization so that it cannot pose a future threat.
How to Implement a Vendor Risk Management Program
Implementing a vendor risk management program is essential for managing vendor risk throughout the vendor lifecycle. Vendor risk assessments and cybersecurity questionnaires should be regularly sent to vendors to continually assess the risk they pose to your organization and establish a policy for addressing these risks – before they impact your business.
The general process for developing a vendor risk management program typically includes defining your objectives, setting up a vendor risk management team, and establishing a process for vendor risk management. After this, you’ll need to develop a list of your vendors, identify vendor risks, and evaluate the risks based on predefined criteria.
At this point, you can then categorize the risks according to predetermined criteria and incorporate the security requirements your vendors must take into the contract. The contract should also clearly state who is responsible for risk assessments and the roles of each party in the event that high risk is found during the assessment. Vendor risk management programs must be continual and should be improved over time.
Vendor Risk Management Software
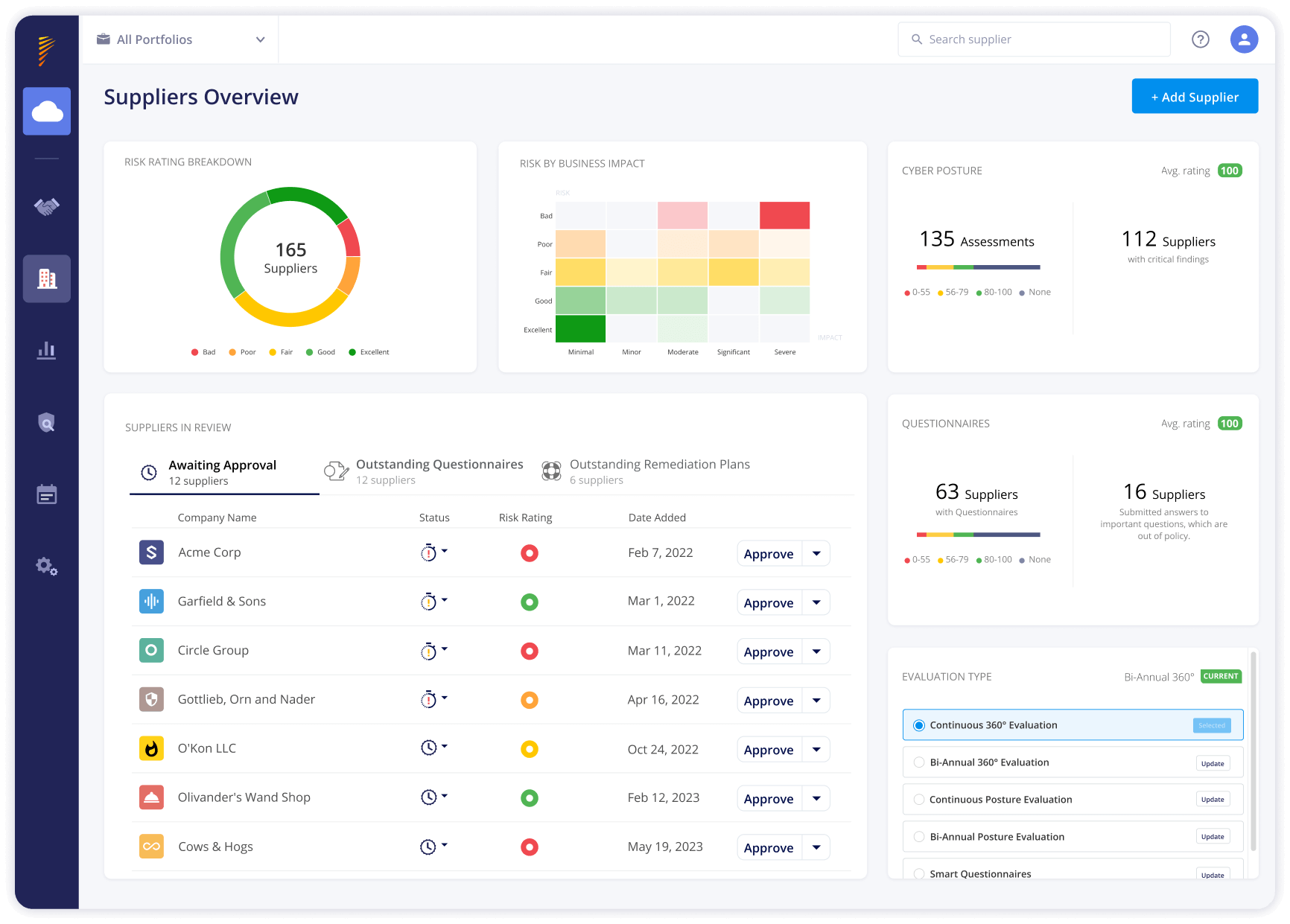
Two trends will continue for the foreseeable future in cybersecurity. The first is that businesses will increase their reliance on third parties that are integrated into their IT infrastructure. The second is that the scope and sophistication of threats will continue to evolve.
With this in mind, organizations are constantly looking to improve their methods for defending against third party threats. They look to vendor risk management software to help them automate and streamline the process of onboarding, managing, mitigating, identifying and monitoring third-party risk at scale.
How Companies Manage Vendor Risk
As your technology, the cybersecurity landscape and reliance and use of third parties changes, vendor risk is dynamic and needs to be monitored continuously. For example, if your payment processing vendor makes a small change to their infrastructure, it may suddenly fail to meet compliance and impact your organization. This is particularly true if you rely on this vendor for capabilities that help you meet compliance, such as data encryption, firewalls, or data breach detection software.

If your organization is going to be successful with your vendor risk management, you’ll need to pay close attention to these areas:
- Specific goals and directives. What are you hoping to achieve with your vendor risk management strategy? There are several areas of potential vulnerability in your vendors and in your business, but which ones are your biggest concerns or biggest priorities? What steps will you follow to review new vendor candidates? How will your strategies evolve over time?
- Context-based relationships. Your vendors should be assessed based on their specific business and technological relationship with your company. For example, a vendor that connects to your business’ IT systems should be treated as more of a risk than a vendor that delivers paper supplies to your business.
- Continuous monitoring. Since new technologies are constantly being introduced, you will need to make sure you’re monitoring your vendors on a constant basis. Even a temporary decline of vigilance can create a blind spot.
- Engagement. It’s best to treat vendor risk management as a kind of partnership between you and your vendors. Accordingly, you should strive for engagement; request your vendors to be open and honest about how they’re operating. Let them know what your standards are (and why they’re your standards), so you can both learn and benefit from the arrangement.
- Legal prioritization. It’s important to fully understand the legal consequences of your actions and the regulatory standards that you must meet in your vendor relationships. For many businesses, regulatory compliance is the top priority for any vendor risk management strategy.
What is Vendor Relationship Management?
Vendor relationship management (VRM) is the process of managing and improving third-party vendor relationships with the goal of achieving the maximum possible benefit for both parties. It’s a collaborative approach that works towards minimizing costs, optimizing vendor performance, negotiating contract terms and fostering better communication between the vendor and the buyer. It also includes establishing and evaluating risk management frameworks and performing regular risk assessments for each vendor.
What is an Enterprise Vendor Risk Management Program?
An enterprise vendor risk management program is a holistic approach to managing risk across your organization. This includes all risks posed to your organization in addition to vendor risk. For example, it considers potential impact from terrorist attacks, natural disasters and economic crises.
It is broader than both vendor risk management and third-party risk management yet encompasses both and can help optimize supply chain risk management. Since it is connected to business risk and an enterprise-wide approach however, it demands strategy and control from top-level leadership.
Why You Need to Manage Your Vendor Risks
A security risk assessment (SRA) is designed to help you evaluate risk and maintain compliance with regulatory requirements. Note that a security risk assessment may also be called something slightly different, like an IT infrastructure risk assessment, a security audit or a security risk audit, or simply a more in-depth vulnerability assessment. Security risk analysis carries several benefits, including its ability to identify areas of weakness, maintain compliance, prevent damage to your operations and revenue, and help you stay up-to-date with security standards.
5 Steps to the Vendor Risk Management Process
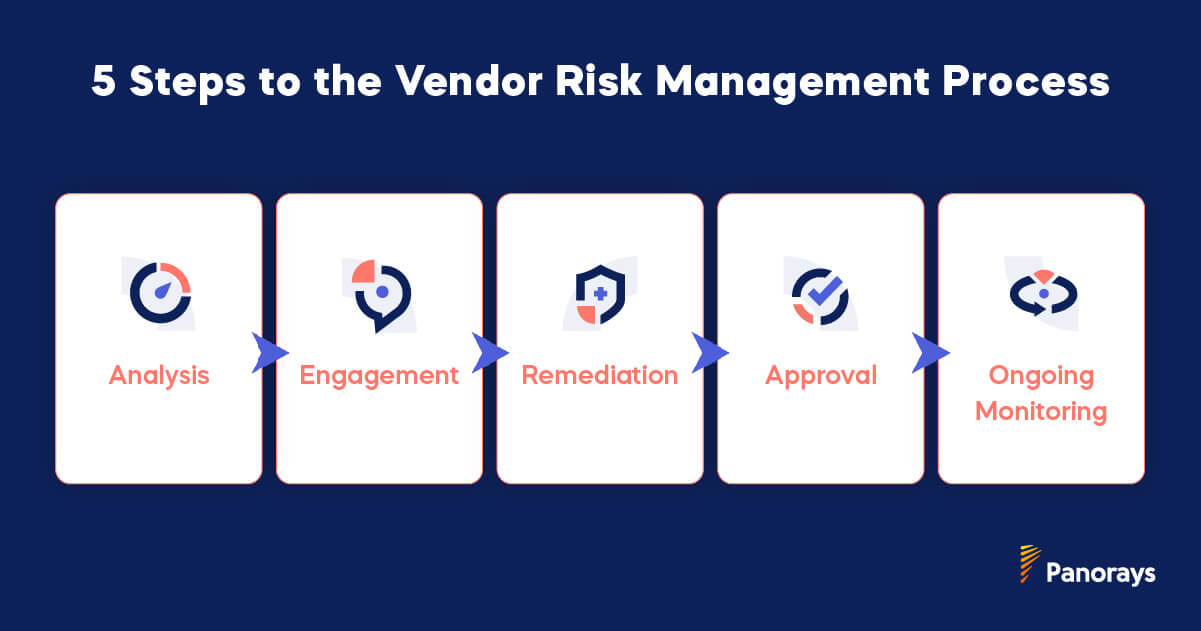
Having a properly detailed process for managing vendor risk is crucial, especially if you’re trying to facilitate greater collaboration across teams in your organization. Vendor security risk management is an ongoing process and one you’ll execute with any future vendors you bring into your supply chain. Although the exact steps might vary between organizations, the general ideas are the same.
The typical process looks like this:
1) Analysis
First, vendor inventory is taken. This identifies every vendor and its relationship to your business. Only after this can your business conduct vendor risk assessment, identifying the inherent risk of the vendor relationship and the level of due diligence to be performed. At this point, your business evaluates the third party’s security posture and performs a gap analysis.
2) Engagement
Your business and third-party should collaborate on how they can work towards remediating any security gaps. This may include implementing a security framework relevant to your industry. For example, healthcare organizations must comply with HIPAA; any vendor that deals with European clients must comply with GDPR. Design your third-party risk assessment so it addresses compliance requirements and regulatory requirements for the industry with the goal of strengthening the business relationship with potential vendors.
3) Remediation
The third-party must fix the cyber gaps. This may include establishing different security controls such as multi-factor authentication, limiting privileged access of data to only those who need it, and data encryption. It may also include sending security questionnaires to understand the vendor’s current compliance policies and procedures. In addition, your business should ensure that the vendor contract includes clauses related to data protection and compliance with your organization’s vendor risk management policies, as well as causes for vendor relationship termination and secure offboarding.
4) Approval
Your business approves the vendor relationship or rejects it based on risk tolerance, whether or not it has met compliance with industry regulations and how critical the service provider is for your organization’s business operations. Approved vendors must be documented, along with the reasons for the approval. (If vendors are rejected, this should also be documented, along with the reasons for the rejection).
5) Ongoing Monitoring
Organizations must continuously monitor the third party to detect any cyber gaps along the entire vendor management lifecycle. This is an essential and proactive approach to emerging threats. This includes the offboarding process to ensure that sensitive data shared with the vendor is no longer accessible to the vendor or deleted.
What is a Vendor Risk Management Plan?
A vendor risk management plan is similar to a vendor risk management program and vendor risk management process in that it identifies the scope and goals of your VRM in addition to identifying the vendors and the potential risk posed to your organization. However, it is different in that it also details the responsibility and role of both the vendor and your organization in the event of a security incident or data breach.
For example, in addition to detailing the role of your IT and third-party risk management team, your vendor risk management plan might also stipulate the responsibility of the HR team and executive leadership after such an incident.
What are Third-Party Vendor Risk Exchanges and How Can They Help Me with Vendor Risk Assessments?
Third-party vendor risk exchanges are a centralized point where organizations and third parties share and access information related to risk in real time. Organizations and their third-party risk management teams use it to access third-party risk data and respond to completed assessments from their third parties. Third parties use the vendor risk exchange to share their risk data and demonstrate their compliance with security measures with responses to security audits and questionnaires.
These exchanges offer many benefits for both parties:
- Organizations and their TPRM teams. Organizations benefit by gaining access to real-time data, reducing time spent on manual data collection, and the ability to better analyze risk data to identify trends and develop proactive measures to defend against risk. It is particularly useful for organizations looking to scale their TPRM and vendors who might be difficult to access, as they only need to apply once to use the exchange.
- Third parties. Third parties also benefit by demonstrating to customers that they are serious about risk management and reducing the need for multiple audits from customers. It also allows them to choose which parties have access to their risk data so that they can maintain control of their sensitive data while at the same time stay compliant with evolving regulations and build trust with customers.
What is a Vendor Risk Management Maturity Model (VRMMM)?
A vendor risk management maturity model (VRMMM) enables organizations to assess an organization’s third-party risk management programs and develop measures to improve it. In addition to being a tool for assessment and roadmap for improvement, it also allows for a holistic approach to the evaluation of vendor risk management so that all relevant areas of third-party risk are addressed. Since it is a standardized approach, it also enables organizations to measure their VRM against other organizations in their industry and understand exactly where they can improve it.
What are the Vendor Risk Management Maturity Levels?
Although vendor risk management maturity levels may differ slightly for each organization, most maturity assessments include five basic levels.
| Maturity Level | TPRM Status | Description |
| 1 | Ad hoc | Startups or organizations with limited resources for TPRM |
| 2 | Approved roadmap | Organizations that perform TPRM occasionally but not on a regular basis and do not have a plan in place |
| 3 | Established | Organizations with an established and approved TPRM program in place but are not yet fully operational and do not measure their performance |
| 4 | Operational | Organizations with a fully operational TPRM program in place and measure their performance |
| 5 | Continuous improvement | Organizations that are able to benchmark their success against others in the industry and make any relevant improvements necessary |
How to Create a Third-Party or Vendor Risk Management Checklist
When developing your vendor risk management process, it is essential to have a basic checklist of questions to ask internally and to your vendors. Please note that this list is only intended as a starting point, and should be customized based on your organization’s risk appetite, the level of risk posed, and according to your type of vendor relationship.
Questions should include:
- What are the current access controls used by the vendor?
- Is the vendor invested in data encryption, data security and information systems controls?
- Does the vendor have an incident response plan in place? Do they have a data recovery plan?
- Has your organization conducted a thorough examination of the vendor’s financial statements, including additional risks along the supply chain such as their subsidiaries’ risk history?
- What types of certification does the vendor have that is protecting data? For example, does it have ISO 27001 certification or SOC 2 certification?
- Has the vendor been in the news recently for bankruptcy, legal battles, or a sudden resignation of the CEO?
- Is the vendor willing to complete a vendor risk checklist or security questionnaire?
Vendor Risk Management Best Practices in 2026
As cybersecurity threats evolve, vendor risk management (VRM) strategies must adapt to new challenges, technologies, and regulatory requirements. In 2025, three key trends are driving best practices: AI-powered risk mitigation, stricter third-party regulations, and cloud security enhancements.
1) Managing AI risks in third-party relationships
AI-powered tools are transforming cybersecurity, with 61% of CISOs believing AI could prevent more than 50% of third-party breaches. However, AI also introduces risks, such as data leakage, algorithmic bias, and misinformation (“hallucinations”) that can lead to security misconfigurations.
To mitigate these risks, organizations should:
- Ensure vendors implement AI governance policies to prevent security vulnerabilities and unethical use.
- Deploy AI bias detection tools to minimize inaccuracies in decision-making.
- Monitor AI-powered vendor applications for unauthorized data usage or compliance gaps.
2) Adapting to stricter third-party risk regulations
Global regulators are tightening oversight on vendor security, requiring organizations to enhance due diligence and compliance tracking. Key regulations shaping third-party risk management in 2026 include:
- DORA (Digital Operational Resilience Act): Now fully enforced, DORA requires financial institutions in the EU to continuously assess vendor risks, implement third-party asset mapping, and maintain remediation plans for security gaps. Non-compliance can lead to heavy fines, making ongoing vendor risk assessments a critical priority.
- NYDFS 23 NYCRR 500: The latest updates to New York’s cybersecurity regulation impose stricter vendor oversight, including more frequent risk assessments, stronger MFA requirements, and enhanced breach notification rules. Vendors handling non-public sensitive data (NPSD) must also comply with higher encryption and authentication standards.
- NIS2 Directive: This EU directive expands cybersecurity and supply chain risk requirements across multiple industries, including healthcare, technology, and energy. Organizations must increase vendor scrutiny, enforce risk-based third-party assessments, and ensure suppliers meet security standards.
To keep up with these evolving regulations, organizations should focus on automating compliance tracking to detect non-compliance risks in real-time. Conducting routine vendor security audits is essential to verifying adherence to changing regulations and ensuring vendors meet the latest requirements. Additionally, organizations must incorporate compliance responsibilities into vendor contracts, clearly outlining expectations and accountability to mitigate regulatory risks.
As third-party risk regulations grow more stringent, businesses that proactively adapt to compliance changes and strengthen vendor due diligence will be better positioned to manage security risks effectively.
3) Strengthening cloud security in vendor ecosystems
The increasing adoption of multi-cloud and hybrid infrastructures has introduced new security concerns, particularly regarding vendor-managed cloud environments. Many organizations struggle with the shared responsibility model, where cloud providers manage infrastructure security, but vendors and customers remain responsible for securing data, access controls, and software configurations.
To minimize third-party cloud risks, organizations should:
- Clarify vendor security responsibilities in contracts and service agreements.
- Regularly audit vendor-managed cloud environments for misconfigurations or security gaps.
- Adopt a zero-trust security model to enforce strict access controls and prevent unauthorized data exposure.
As cloud adoption accelerates, organizations must strengthen their VRM programs to ensure vendors maintain secure and compliant cloud environments.
How to Automate Vendor Risk Management with Panorays
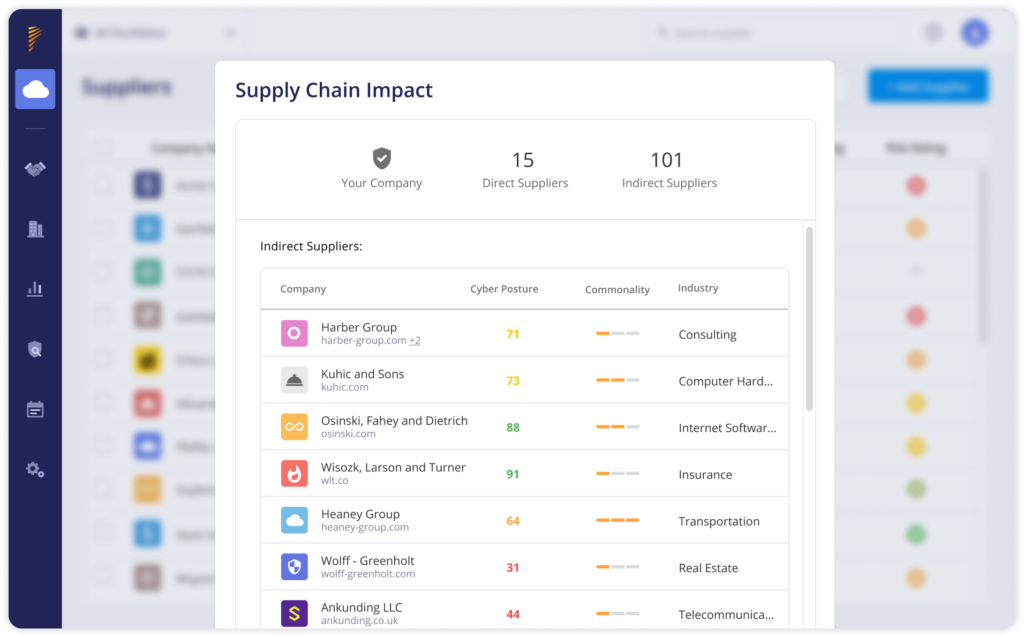
Panorays delivers a contextual business approach to vendor risk management that streamlines and automatically detects your threat landscape, including third, fourth and fifth parties and the risks posed to your organization according to their criticality. It then customizes its assessment and scoring based on criticality, sending alerts based on the risk level. Finally, it prioritizes the most important issues your third parties should remediate, delivering a step-by-step plan to close the gaps that pose the most risk to your organization.
Want to learn more about how Panorays can automate your vendor risk management? Get a demo today!
FAQs
-
Vendor risk management (VRM) is essential for identifying, assessing, and mitigating risks posed by third-party vendors. As organizations expand their digital ecosystems, the reliance on external providers for software, infrastructure, and services introduces increasing security and compliance risks.
Cyberattacks targeting supply chains are on the rise, with over 60% of data breaches now involving third parties. In 2023, the Change Healthcare cyberattack disrupted medical billing nationwide, delaying patient care and causing widespread financial strain. These incidents underscore the need for proactive, real-time vendor risk management to prevent disruptions and protect sensitive data.
In 2026, organizations must increasingly adopt AI-driven risk assessments, automated compliance tracking, and continuous security monitoring to ensure vendors meet cybersecurity standards. A proactive, technology-driven approach is no longer optional—it’s a necessity.
-
Each third-party vendor, upon being connected to your organization, is going to carry some level of cybersecurity risk. Risks could be financial, operational, legal, regulatory, reputational and even geopolitical. If a vendor fails to uphold their end of the deal in matters of security (e.g. they don’t implement proper security controls or data encryption), or if they’re the victim of a cyberattack, it could impact your organization directly. An effective risk assessment, as part of a greater vendor risk management plan, strives to identify and fix these potential failure points long before they become a problem.
-
Even if your own internal security measures are strong, integrating third-party vendors who don’t follow best practices into your IT infrastructure can pose a big risk to your organization. This is especially true when those vendors handle confidential, sensitive, proprietary, or classified information. Vendor risk management provides a documented strategy that helps your organization streamline the VRM process.
-
A strong vendor risk management (VRM) program is built on a structured approach that ensures vendors meet security, compliance, and operational requirements. Effective VRM programs incorporate thorough risk assessments, continuous monitoring, and clear contractual obligations to safeguard organizations from potential security threats. By integrating these key components, businesses can proactively mitigate risks and build stronger vendor relationships.
-
Since the level of security risk also varies widely depending on additional factors such as the type of organization, industry, third-party relationship, technologies, and relevant regulations, organizations need to continue to employ third-party vendor risk management throughout the lifecycle of the business relationship.These stages can be divided into three separate periods:
Onboarding: Due diligence is conducted at the beginning of the vendor relationship to evaluate whether or not the business should enter into a relationship with the third party in question.
Ongoing monitoring: Security risks are regularly evaluated during the vendor relationship to ensure the third party is applying the appropriate security controls to meet the relevant regulations and standards.
Offboarding: Vendors who terminate their relationship with your organization must have a process for disengaging, deleting and transferring sensitive data and information formerly shared with your organization so that it cannot pose a future threat.
-
Implementing a vendor risk management program is essential for managing vendor risk throughout the vendor lifecycle. Vendor risk assessments and cybersecurity questionnaires should be regularly sent to vendors to continually assess the risk they pose to your organization and establish a policy for addressing these risks – before they impact your business.
The general process for developing a vendor risk management program typically includes defining your objectives, setting up a vendor risk management team, and establishing a process for vendor risk management. After this, you’ll need to develop a list of your vendors, identify vendor risks, and evaluate the risks based on predefined criteria.
At this point, you can then categorize the risks according to predetermined criteria and incorporate the security requirements your vendors must take into the contract. The contract should also clearly state who is responsible for risk assessments and the roles of each party in the event that high risk is found during the assessment. Vendor risk management programs must be continual and should be improved over time.



