The lack of proper security controls can put an organization in a security situation that can be difficult to unravel. Take First American, the second largest title insurance company in the U.S, which was recently ordered to pay $1 million in penalties to the State of New York for violations against cybersecurity regulations 23 NYCRR 500 (also known as NYDFS Cybersecurity Regulation). The company suffered a major cybersecurity breach in 2019 that exposed 885 million customer records including sensitive data such as bank account numbers, bank statements, mortgage records, tax documents, and Social Security numbers.
The New York State Department of Financial Services (DFS) investigation found that the company violated several elements of the Cybersecurity Regulation, including the requirement to implement security controls. As a result, First American, along with many other organizations across industries, have started to take a better look at the information security controls they have implemented and how effective they might be in the event of a third-party data breach.
What are Information Security Controls?
Information security controls are any actions an organization takes to protect against unauthorized access to data and information and manage security risks. They can be physical, technical or administrative. Each type of security control helps organizations protect sensitive and confidential data from being accessed by unauthorized individuals, which leads to data leaks and breaches. In addition, information security controls help to prevent theft of IP data and trade secrets. Companies that can assure customers that they have proper security controls in place and are resilient against operational disruption in the event of an attack build more trust with their customers.
The main types of information security controls include:
- Preventative. These types of information security controls, such as malware detection, firewalls, access controls, software patching, and employee awareness training are all aimed at preventing security incidents.
- Detective. Vulnerability management, security information and event management (SIEM) systems and log monitoring are all examples of information security controls that are used to detect security incidents once they have occurred.
- Corrective. Patch management, incident response, backups and restoration, and malware removal tools are all examples of security tools that help mitigate the impact of a security incident.
The Main Critical Security Control Frameworks
Many organizations look to different frameworks and guidelines to ensure that both they and their third parties have the proper security controls in place to maintain cybersecurity best practices. This is a non-comprehensive list that addresses only a few of the main frameworks that deal specifically with third parties.
ISO/IEC 27001 and 27002 Framework
ISO 27001 is an international standard that includes security controls for your information security management system (ISMS) and is therefore relevant for third-party risk management. ISO 270001 requires the establishment, implementation, maintenance, and continual improvement of an ISMS while ISO 27002 includes best practices on ISMS.
When organizations meet ISO 27001/2 standards both internally and across their third parties, it signals to business partners that they take cybersecurity best practices seriously and have proper security controls in place. As a result, many businesses look to enter a business relationship only with organizations that have put these standards in place.
NIST Cybersecurity Framework
The NIST CF, or National Institutes of Standards and Technology Cybersecurity Framework, is based on the NIST 800-50, a set of standards of 800 controls for governmental agencies or anyone that wants to do business with the U.S. government. NIST 800-50 was developed in 2002 in response to the increase in cybersecurity attacks on critical infrastructure. The NIST CF, however, also includes controls for third-party risk management. It offers a structured approach to TPRM that not only includes roles for every manager in the organization beyond IT or security but also functions, categories, and subcategories for each third party.
CIS Framework
The nonprofit Center for Internet Security developed a security control framework called CIS, a well-known set of security controls used to map compliance standards. The CIS has different program areas for different types of organizations, including those working with the government, private sector, academia, and even the general public. The CIS security controls are standardized, making it easier for organizations to verify whether or not their third parties are meeting best practices for cybersecurity. They also help organizations manage third-party risk by helping them enhance the visibility of third parties and provide a risk assessment framework for assessing the security controls of third parties. In addition, it also provides guidelines for effective incident response and management so that organizations have a process for dealing with third-party data breaches and other security incidents.
The Role of Security Controls in Third-Party Risk Assessment
Security controls help organizations manage their third-party risks and are an essential part of proper third-party risk management. They help optimize and mitigate against third-party risks in different ways.
These include:
- A proactive approach to security. Proper security controls such as the principle of least privilege (POLP) make it easier to proactively identify the potential security threats a third party might bring to the organization. Your organization is better prepared to identify unauthorized access to sensitive data and networks and can mitigate any incidents as soon as possible.
- Consistent adherence to compliance. Security controls such as multi-factor authentication (MFA) are mandatory for many organizations that want to meet compliance. Risk assessments and due diligence questionnaires help to evaluate the security controls third parties have in place to meet these regulations. Regular checking of controls is crucial as technology, regulations, and internal policies are dynamic and subject to frequent changes.
- Continuous monitoring. Vulnerability assessments and threat detection systems help organizations regularly monitor the risks posed to their system by their third parties so that they can evaluate and prioritize them to address the most urgent ones as promptly as possible.
How Panorays Can Help You Manage Third-Party Risk
Panorays delivers a third-party cyber risk management platform that pinpoints indications of early threats within the unique context of every relationship. This enables companies to continually adapt their defenses and proactively prevent the next breach from affecting their business.
Its modules include:
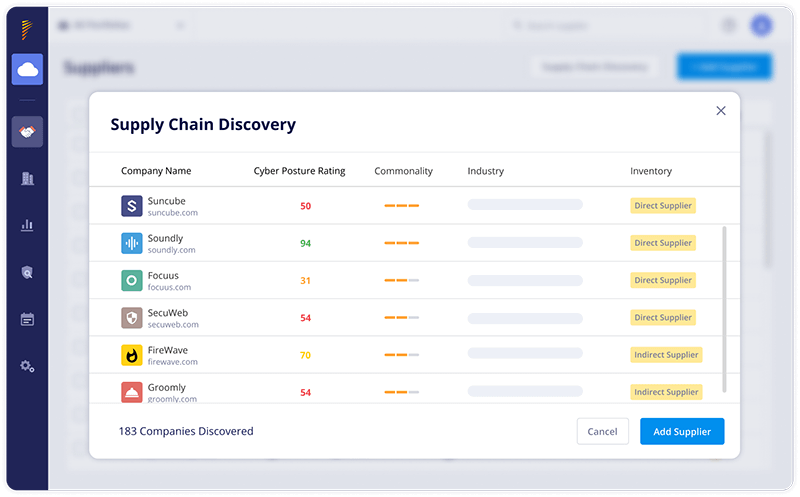
- Supply Chain Discovery and Mapping. Automatically discover unknown third, fourth, fifth, and n-th parties and define the relationship they have with your organization.
- Risk DNA Assessments. Conduct both internal and external assessments of your third parties, based on your unique risk appetite. Risk DNA also takes into account all third-party breach history and generates AI-driven predictions for future data breaches. All of these elements work together to deliver the most accurate cyber risk rating of your third parties on the market today.
- Continuous Threat Detection. Uncover exclusive critical findings and get third-party threat intelligence with a contextualized view of your supply chain.
- Remediation and Collaboration. Take immediate preventative actions with minimal need for communication with third parties. Deliver your suppliers a list of critical tasks they must perform to improve their cyber posture – addressing the most important ones first.
Want to learn more about how you can manage your third-party risk with Panorays? Get a demo today!