Third-Party Cyber Risk Management for Technology Companies
Complete Control Over Third-Party Risks

Tackle Supply Chain Complexity
Manage your complex supply chain and easily assess the security postures of all software vendors and integrations. Gain visibility into your third parties’ security postures and manage each relationship with remediation steps and in-platform communication.
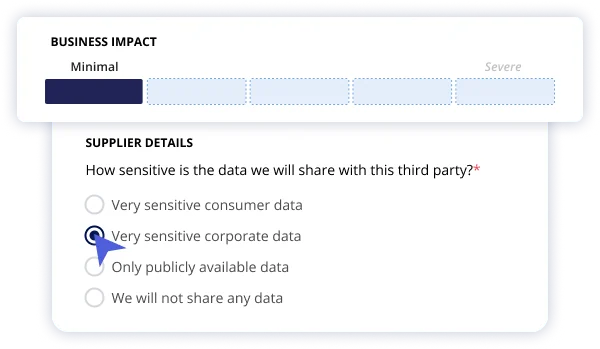
Manage Vendor Criticality Based on Data Access
Panorays helps SaaS companies categorize and prioritize vendors based on the criticality of the information and services they provide. This way you can focus your resources on managing the risk associated with the most crucial vendors, and in context to your unique risk appetite.

Respond to Third-Party Data Breaches
Build a trusted incident response strategy with tools to identify and manage the risks associated with third-party vendors. Respond to breaches and vulnerabilities in collaboration with third parties to reduce potential damage and downtime.
-

Tackle Supply Chain Complexity
Manage your complex supply chain and easily assess the security postures of all software vendors and integrations. Gain visibility into your third parties’ security postures and manage each relationship with remediation steps and in-platform communication.
-

Manage Vendor Criticality Based on Data Access
Panorays helps SaaS companies categorize and prioritize vendors based on the criticality of the information and services they provide. This way you can focus your resources on managing the risk associated with the most crucial vendors, and in context to your unique risk appetite.
-

Respond to Third-Party Data Breaches
Build a trusted incident response strategy with tools to identify and manage the risks associated with third-party vendors. Respond to breaches and vulnerabilities in collaboration with third parties to reduce potential damage and downtime.


