Cyber attacks are growing in both volume and sophistication, at the same time as attack surfaces are growing. As organizations raise their protections against cyber attacks, third-party cyber risk management (TPCRM) should be top of the list of priorities.
Third-party cyber risk management involves identifying, assessing, and mitigating cyber risks associated with vendors, partners, or service providers who might have access to your information systems or data. When all systems are connected, a vulnerability in your vendor’s networks can be a back door to your business-critical systems or sensitive data, causing damaging data breaches, harming your reputation, and/or disrupting business operations.
It’s impossible to neutralize all risk, but effective TPCRM can reduce it significantly. Robust third-party cyber risk management helps protect you from the fallout of a third-party data breach, and ensures that you comply with regulations that mandate TCPRM. What’s more, it gives you confidence about who is in your network, so you won’t stress about an unpleasant surprise from an unknown connection.
In this guide, we’ll present in-depth information about third party cyber risk management, how to conduct TPCRM effectively for your organization, and actionable steps to reduce third-party cyber risk.
Understanding Third-Party Cyber Risks

Third-party cyber risk refers to the potential threats and vulnerabilities that external parties introduce to your digital ecosystem. They could be vendors, suppliers, partners, or service providers — what matters is that they have some access to your data, networks, and/or systems.
The types of third-parties you could work with include:
- Cloud service providers
- Software and SaaS vendors
- Consultants and contractors for any digital services
- Payment processors
- Hardware suppliers for printers, computers, or any connected devices
- Third-party support services, such as IT helpdesk services or customer support services
- Business partners who work with you in any aspect of your operations
Third parties introduce a whole range of potential risks, including:
- Data breaches or data loss
- Unauthorized access to networks or data
- Malware infections
- Service outages
- Supply chain attacks
- Financial fraud
- Non-compliance with regulatory standards
- Counterfeit products that are infected with malware
- Remote access vulnerabilities
The Importance of Managing Third-Party Cyber Risks
Third-party cyber risks can disrupt your business operations, damage your financial standing and/or reputation, affect your compliance with regulations, and more. For example, operations were suspended for days for dozens of credit unions when their cloud services provider, Ongoing Operations, was hit by a ransomware attack.
Data breaches are among the most common fallouts from third party incidents, and customers are quick to leave a company after a third-party data breach. In January 2023, hackers accessed the personal data for millions of T-Mobile customers, using a vulnerability in one of their third-party vendors.
Third-party supply chain attacks can be particularly worrying for critical infrastructure. According to one study, 90% of leading global energy companies experienced a third-party breach in 2023. That means that vital energy provision could be disrupted or taken over, and sensitive data like customer payment details could be accessed.
Regulatory Requirements for Third-Party Cyber Risks
Managing third-party cyber risk is a prerequisite for compliance with many regulations and standards. Some are industry-specific or region-specific, while others apply to all businesses. Failing to identify and mitigate third-party risks can result in penalties from the regulatory authority.
Here are some of the key regulations and standards that organizations should be aware of:
- In the US, HIPAA requires covered entities to ensure that business associates comply with HIPAA’s security and privacy rules.
- The EU’s GDPR requires organizations to ensure that third-party processors comply with data protection and breach notification obligations.
- DORA requires EU financial service organizations to monitor and ensure compliance from their third parties.
- California’s CCPA mandates that third-party service providers adhere to data privacy standards and provide consumers the right to opt out of data sharing.
- The SOX requires public companies in the U.S. and their third-party service providers to meet stringent controls over financial reporting.
- The ISO/IEC 27001 standard includes provisions for managing third-party risks through contracts and monitoring.
- The PCI DSS requires organizations that handle payment card information, and their third-party service providers, to meet certain standards to protect cardholder data.
Key Components of Third-Party Cyber Risk Management (TPCRM)
Effective TPCRM involves a number of factors. It’s vital to identify all possible cyber risks from third parties, which requires cataloging all third-party relationships and mapping their access points.
You’ll need a comprehensive inventory that documents all the companies that interact with your systems or data. List their access level and what data they handle, and detail the services they provide. This makes it possible to pinpoint which third-party services pose the most critical risk to your business, so you can focus your efforts in the right places.
Assessing your third parties’ security practices to ensure they comply with relevant regulations and standards is another vital pillar for robust third-party cyber risk management. You need to establish clear contractual requirements, including incident response and reporting protocols, and set up processes to monitor and audit their security measures on a regular basis.
Third-Party Cyber Risk Assessments
Assessing your exposure to third-party cyber risk is a crucial step in any TPCRM program. It involves evaluating the security practices and potential vulnerabilities of every external vendor and partner that interacts with your systems or data.
As well as building an inventory of their data access and how business-critical their services are, you’ll want to profile their individual exposure to cyber risk. This involves security questionnaires, security ratings, audits, and penetration tests, to check how robust their cyber security provisions are.
You should also review their cybersecurity policies, controls, and compliance with relevant regulations and standards; analyze their incident response capabilities; and consider their past performance with regards to cyber security. You want to identify potential risks and weaknesses, and verify that their practices align with your security requirements.
Third-Party Cyber Risk Due Diligence
As the network of third parties grows, organizations are increasingly using cyber risk due diligence checklists and protocols. These are processes that guide you through all the steps involved in evaluating third-party cyber risks, before you decide whether to work with the company.
Due diligence typically involves a thorough audit of each entity’s security practices. You need to review their security documentation and previous audit reports; talk with their IT and security staff; evaluate their cyber security controls and protocols; and run your own tests on their systems. It’s a good idea to check what physical security they have to protect data centers or other facilities. Plan for regular follow-up audits and continuous monitoring, so that changes don’t take you by surprise.
Contractual Protections for Third-Party Cyber Risk Management
Once you’re fully informed about your third parties’ cyber risk levels, you can incorporate the relevant security requirements into the contract you sign with them. This should involve embedding robust cybersecurity requirements and Service Level Agreements (SLAs) that clearly define the cybersecurity obligations of the third party.
Your contract should outline specific measures for data protection, like encryption, access controls, and regular security assessments, together with compliance with relevant regulations and standards. Additionally, the contract must include detailed terms for breach response. Be precise about their responsibilities and timelines for notifying you about any security incidents. Include SLAs that set performance benchmarks for cybersecurity-related activities, such as incident response times and recovery procedures.
Continuous Monitoring That Addresses Third-Party Cyber Risks
Third-party cyber risk isn’t a once-and-done exercise. It’s vital to continuously evaluate third-party security postures, to identify any emerging threats or vulnerabilities. Regularly scheduled audits, periodic reviews of compliance with security policies, and the assessment of any changes in the third party’s operations or systems are crucial components of this process.
The only way to succeed is by leveraging technology. Automated tools and platforms can provide real-time visibility into third-party activities and security practices. These technologies can monitor network traffic, detect anomalies, and flag potential security incidents, allowing for prompt response and mitigation.
Additionally, tools for continuous vulnerability scanning, security information and event management (SIEM), and threat intelligence can help your organization to stay ahead of evolving cyber risks. They give you early warnings about threats that could emerge, so you can manage third-party cyber risks in a proactive way.
Steps to Implement TPCRM
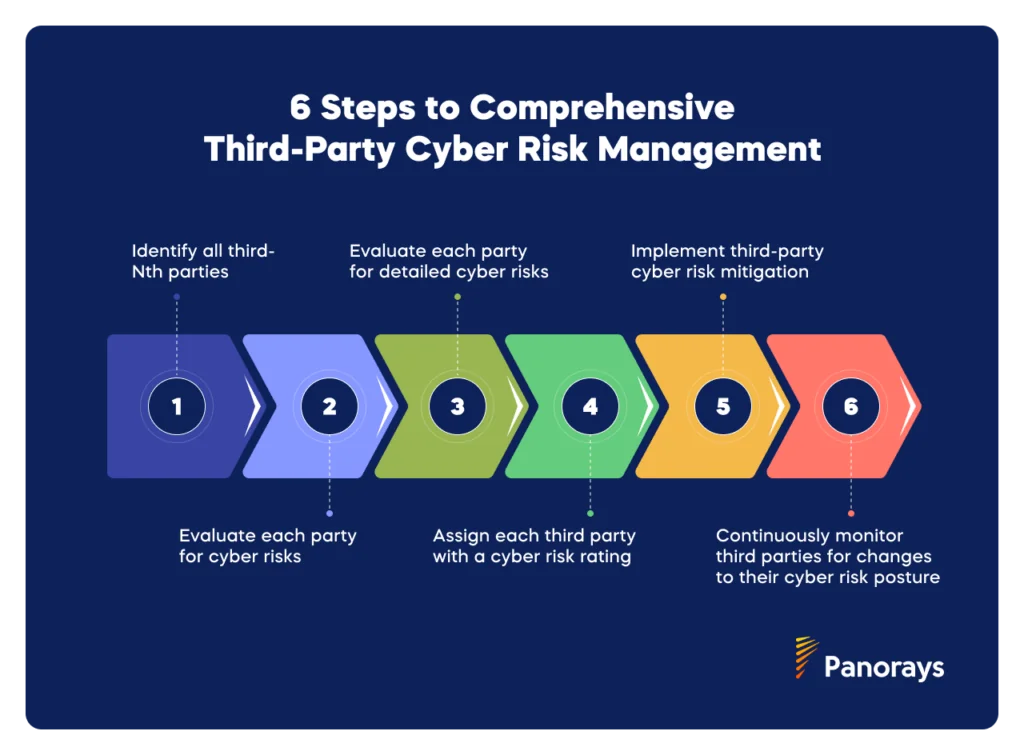
Third-party cyber risk is complex, extensive, and constantly-evolving, so your approach to managing it needs to be suitably multi-faceted. Effective TPCRM requires you to identify and understand all potential vectors for third-party cyber risks, rank them according to criticality, take steps to mitigate them, and establish processes for continuous monitoring.
Here’s a deeper explanation of what’s needed for successful third-party cyber risk management.
Step 1: Identify all third-Nth parties
The first step is to identify every source of potential cyber risk, going beyond third-parties to fourth and Nth parties. Many companies struggle to view their wider supply chain, let alone each party’s level of access to sensitive data or business-critical systems. There are tools that can help uncover Nth-parties and build a comprehensive inventory of your vendors, suppliers, and partners.
Once you know your third-plus parties, you can classify them according to risk level and how crucial they are to your business operations. Third parties that have access to sensitive data and are vital for business continuity should be the top of your list for risk management.
Step 2: Evaluate each party for cyber risks
The next step is a preliminary screening to identify high-risk vendors. Typically, it involves sending detailed questionnaires and assessments to gather information about the vendor’s cyber security posture and practices. Address data protection practices, access controls, incident response plans, compliance with relevant regulations, and historical security incidents.
Then, you’ll need to thoroughly evaluate responses to identify risks or vulnerabilities. Look out for incomplete or inaccurate information, and compare the response against predefined risk criteria. Vendors that show significant weaknesses could be rejected, or could be flagged as priorities for risk mitigation.
A platform like Panorays can automate the entire process, generating customized questionnaires, checking that responses are complete by verifying them against internal documentation, and producing a Risk DNA score that highlights entities that need more attention.
Step 3: Detailed Cyber Risk Evaluation
Now you’re ready to evaluate third party risks in greater depth. You want to test numerous aspects of their cyber security posture, including network and application security, data protection, regulatory compliance, incident response, and more, across all their assets, systems, and networks.
It should include:
- Your own cyber security tests
- On-site audits
- Interviews with key personnel
- A comprehensive review of their security policies, protocols, certifications, and employee security training programs
A comprehensive evaluation needs to examine access controls, data protection policies, encryption, audit trails, regulatory compliance, and other aspects of data security. Don’t forget to investigate how quickly they can recover from a cyber attack.
Step 4: Assign each third party with a cyber risk rating
Use a cyber risk assessment platform to analyze the results of your previous evaluations and generate an overall cyber risk score. It’s up to you how much weight you give to different factors like the vendor’s security controls, compliance status, and historical incident response.
Then you can rank third parties according to their scores, and apply appropriate mitigation efforts, controls, and monitoring. Assigning risk scores reveals which entities require more immediate attention and rigorous oversight, so you can allocate resources strategically to the most critical risks.
Step 5: Implement third-party cyber risk mitigation
Risk management and mitigation strategies protect your assets and data from third-party cyber risks. Set clear expectations for third party security practices, incorporating robust contractual terms and establishing ongoing monitoring processes to ensure compliance. You should mandate regular follow-ups, to verify that the vendor adheres to the agreed-upon controls.
It’s best to build detailed, individual risk mitigation plans for high risk vendors, outlining specific actions and controls to address the vulnerabilities you identified. You might require vendors to enhance their security protocols, implement additional safeguards, or undergo regular security training and audits.
Step 6: Continuously monitor third parties for changes to their cyber risk posture
Finally, it’s just as important to regularly reassess third-party risks and update risk scores. It helps you quickly identify and address any new or evolving risks, ensure that your risk management strategies remain effective, and check that vendors continue to meet security and compliance standards.
It’s best to deploy automated tools and systems that provide real-time or near-real-time updates on various risk factors, such as changes in the vendor’s security status, compliance issues, or emerging threats. Periodically review information from your monitoring tools, and adjust third party risk scores based on new data
Best Practices for Third-Party Cyber Risk Management (TPCRM)
It’s important to approach TPCRM in a structured manner, to make sure that no risks go overlooked. Adhering to best practices can ensure that your third-party cyber risk management is streamlined and effective at protecting your organization.
These include developing a comprehensive third-party cyber risk management framework which standardizes your criteria and methodologies for cyber risk assessment and evaluation, lays out clear guidelines for scoring and ranking third-party risk, and establishes processes for risk mitigation and ongoing monitoring.
Effective cyber risk management can’t stand alone, however. Your TPCRM program needs to be integrated into your overall cybersecurity strategy as part of a holistic defense mechanism which enhances general organizational resilience. Third-party cyber risk management should be aligned with your wider organizational policies and incident response plans.
Third-Party Cyber Risk Management Technology and Tools
Organizations today have to manage cyber risk across an increasingly large and complex network of third parties along sprawling supply chains. You need advanced technology to bring visibility into all your third parties, streamline assessments and audits, scale and speed up mitigation, and conduct continuous monitoring.
There are many tools out there offering to help with TPCRM, so it’s important to select and deploy the right ones. Look for platforms that can help with multiple tasks, like scoring questionnaire responses as well as sending them.
Solutions that use automation, artificial intelligence (AI), and machine learning (ML) significantly enhance your risk management capabilities. Automation can gather and analyze data faster and with more accuracy, while AI and ML algorithms can detect patterns that indicate potential security threats. Additionally, AI tools can monitor third parties in real time, sometimes with instant alerts and automated incident response.
Collaboration and Communication for Successful TPCRM
Successful risk management rests on smooth collaboration and communication both internally and externally. Internally, departments like IT, legal, procurement, and compliance need to pool their perspectives to produce complete, 360-degree risk evaluations and comprehensive cyber risk management strategies.
You also need to work effectively with your third parties. TPCRM is a joint undertaking, not an attempt to catch them out, so be transparent about your expectations and cybersecurity requirements. Clearly communicate your policies for data protection, incident reporting, and compliance with regulatory requirements, and arrange regular meetings, audits, and assessments.
TPCRM Training and Awareness
Your employees are crucial partners in your risk management program. Well-informed employees are more likely to follow established protocols, recognize potential threats, and respond appropriately to incidents involving third-party interactions. They need to be educated about potential vulnerabilities and their role in mitigating these risks.
Ensuring that employees understand what’s involved in TPCRM requires regular training programs and awareness campaigns to keep them updated on the latest threats, best practices, and regulatory requirements. It’s best to include interactive training sessions, newsletters, and real-world case studies, to maintain a high level of vigilance.
Overcoming Challenges in Third-Party Cyber Risk Management

There are many challenges that can stand in the way of successful TPCRM. One significant challenge is the lack of visibility into sprawling supply chains, which can hide potential Nth-party threats from view.
Organizations also often struggle to gain a comprehensive understanding of third-party cybersecurity practices, making it difficult to accurately assess potential risks. This lack of transparency can be exacerbated when businesses are unwilling or unable to share detailed security information, leaving organizations uncertain about their exposure to cyber threats.
Inconsistent assessment criteria and standards further complicate TPCRM. Organizations may apply varying levels of scrutiny to different vendors, leading to gaps in risk management. Some vendors might fly under the radar, while others are subjected to overly stringent requirements.
Additionally, smaller organizations may have limited resources and expertise for TPCRM, which can handicap their ability to sufficiently evaluate third-party vendors and increase their vulnerability to cyber risks.
Strategies to Overcome TPCRM Challenges
The good news is that there are ways to overcome all these challenges. To begin with, every organization of every size needs a consistent TPCRM framework that contains clear policies and procedures for due diligence, ongoing monitoring, and incident response, as well as standardized assessment criteria and protocols.
Companies with limited resources can take advantage of third-party cyber risk management services and platforms. These tools can handle continuous monitoring, automate risk assessments, deliver comprehensive reports, and provide deeper insights into third-party cybersecurity practices.
It’s also vital to run internal training programs, so that employees have the knowledge and skills to manage third-party risks. It’s often worth hiring specialist cybersecurity professionals who have experience in TPCRM, to strengthen your risk management programs.
Third-Party Cyber Risk Management Solutions
Third-party cyber risk management is vital to protect your business-critical systems, defend your organization from attacks and data breaches, and ensure operational resilience. A strong TPCRM strategy helps prevent business disruption, reputational damage, financial harm, and/or penalties for non-compliance, all of which could result from vendor-related cyber vulnerabilities.
As a result, managing third-party cyber risk should be a high priority for every organization. Understanding the vital components, investing in the right tools, and implementing the correct best practices empowers your business to identify and mitigate third-party cyber risks before they have any negative impact.
How Panorays Helps Manage Third Party Risks
Panorays is the only third party cyber management solution that delivers contextual third party risk management. By mapping your full threat landscape and continuously monitoring and reassessing the Risk DNA of each business connection, it pinpoints early threat indications within the unique business context of every relationship, enabling companies to adapt their defenses, minimize risk and proactively prevent the next breach from affecting their business.
The platform includes:
- AI-powered cybersecurity questionnaires. Unlike traditionally cumbersome security questionnaires that can take days or weeks to complete, these AI-powered cybersecurity questionnaires streamline third party risk management and can be completed in minutes. On the supplier’s end, AI assists in generating answers based on questionnaires conducted in the past. On the evaluator’s end, AI assists in evaluating the accuracy of responses by validating them with internal documents from both the organization and vendor.
- Extended attack surface assessments. These assessments start with first identifying and mapping third, fourth, fifth and n-th party relationships, identifying risk and prioritizing it according to the level of criticality so that organizations gain deeper visibility into the digital supply chain.
- Risk DNA Assessments. Assess the cybersecurity posture of your third parties with AI-based accuracy, taking into account the dynamic nature of every relationship. Risk DNA evolves to reflect changes that impact your third party risk, including shifts in data access and severity, changes in their business criticality and developing vulnerabilities.
- Continuous monitoring. Conduct attack surface assessments and send vendors cybersecurity questionnaires when necessary, such as when a change is made in your organization or vendor’s IT infrastructure, or an announcement of a change in the industry’s regulations.
- Automatic discovery of third, fourth, and n-th party vendors. Organizations don’t always know which third party services and applications they are using (much less fourth and fifth parties). Attack surface assessments begin by mapping and identifying third, fourth and n-th party vendors to understand the business relationship between them and your organization. Then it ranks them according to their level of criticality.
- Evaluation of compliance. Verify whether or not your suppliers are meeting compliance and continuously monitor for new issues for meeting regulations and standards such as GDPR, NDFS and PCI DSS. Replace clunky spreadsheets with efficient frameworks to document process-oriented regulations such as the OCC and EBA.
- Customized remediation. After sending cybersecurity questionnaires and identifying cyber gaps that need to be addressed, vendors and organizations can collaborate together using a detailed plan to remediate any risk you deem necessary, customized according to each organization’s specific risk appetite.
Ready to strengthen your third-party cyber risk management? Get a demo of our third party risk management platform today.
TPCRM FAQs
-
Third-party cyber risk management, or TPCRM, means the process of addressing cyber risks that arise from third parties. These risks could include data breaches, malware, disruption to business networks, and more. TPCRM involves identifying those risks, taking steps to mitigate them, and monitoring them for the long term.
-
The best way to lower your third-party cyber risks is to implement a holistic third-party cyber risk management program. This should include implementing automated tools that help identify, evaluate, monitor, and mitigate potential sources of cyber risk, as well as applying a strategic approach that prioritizes third parties that are the highest risk.
-
A third-party risk management framework is a set of standardized criteria and methodologies for assessing third parties and addressing the cyber risks that they pose. It helps enforce effective processes for mitigation and continuous monitoring, and ensures a structured approach to evaluating, scoring, and ranking third-party risk.



