Security practitioners often struggle to accurately determine how critical or sensitive their third parties are to the business. Without clear visibility, it becomes difficult to tier, classify, or map suppliers and plan security assessments effectively. As a result, teams may end up assessing the wrong vendors, overlooking potentially high-risk third parties, or wasting time and resources on non-critical ones. Panorays’ Inventory solves this challenge by centralizing all your third parties in one place, giving you the visibility to monitor their security posture, define their inherent risk, and plan assessments proactively.
What is Panorays’ Centralized Vendor Repository?
Panorays’ Inventory enables security practitioners to easily upload their entire digital supply chain for automatic cybersecurity assessments. It also allows sending internal questionnaires (IRQs) to evaluate each third party’s business impact. Using these two risk indicators, teams can effectively tier their third parties and determine how frequently each should be assessed, ensuring a smarter, risk-based approach. Additionally, Inventory provides flexibility to keep an eye on low-critical vendors and seamlessly move them into the appropriate assessment plan whenever needed.
Inventory is also beneficial for procurement, finance, legal, and other non-cyber risk-related roles, as well as for risk management, cybersecurity, and budget-conscious teams.
Benefits of a Centralized Vendor Repository
Panorays’ Inventory helps you simplify and strengthen your third-party cybersecurity program. From complete visibility to automated prioritization, here’s how it simplifies your workflow and strengthens your security strategy:
Single, up-to-date supplier repository: Easily upload all your third parties to Panorays, regardless of their criticality or sensitivity. Even if you’re unsure how or when to assess them, full visibility over your digital supply chain, combined with automatic risk indicators, enables you to make data-driven decisions and plan assessments proactively.
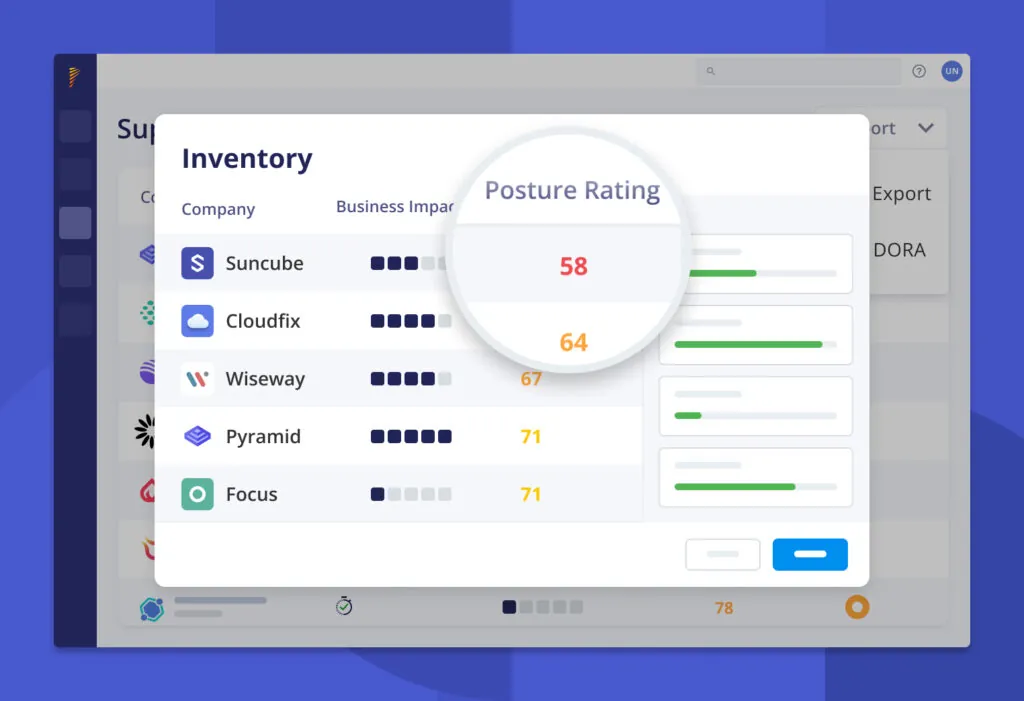
At-a-glance risk scoring across all vendors: When you add a supplier to Inventory, an External Attack Surface Assessment (EASA) generates a Cyber Posture Rating you can rely on to guide the type and frequency of security assessments. Panorays also gives you the flexibility to move suppliers to the appropriate assessment type based on their risk.
Tiered third parties and prioritized plans: Along with the Cyber Posture Rating, you can send an internal questionnaire (IRQ) to gather business impact insights for each supplier. This helps you understand how critical and sensitive each supplier is to your business and enables you to create a customized, data-driven security plan, saving time, effort, and budget.
Low-critical watchlist portfolio: Keep your low-risk third parties in Inventory without diving into detailed cyber insights, while monitoring their frequently updated high-level cyber ratings. This gives you the flexibility to respond quickly to emerging cyber events and to easily move impacted third parties into a full assessment plan for faster incident response.

Panorays’ Inventory: Your Centralized Vendor Repository Solution
Managing your entire digital supply chain from a centralized platform is key to adopting a proactive, context-based risk approach. Tiering your third parties by their criticality and sensitivity helps you plan and prioritize your security assessments effectively. See how Panorays’ Inventory provides the visibility, prioritization, and flexibility you need in Third-Party Cyber Risk Management (TPCRM). Request a demo today.



