Your vendor relationships can be the most important connections in your organization’s life. These are the companies that supply your business with vital services, provide crucial components for your end products, and/or work together with you to continuously expand your market offering and grow your customer base.
But the same third parties that you depend upon to keep your company afloat might open up vulnerabilities that could sink it. Third-party risks could affect your financial stability, business reputation, operational continuity, or compliance posture, but cybersecurity risk is what keeps executives awake at night. Our survey found that 94% of CISOs are concerned about third-party cybersecurity threats, and for good reason.
Working with a vendor that has poor cybersecurity exposes you to data breaches, service outages, malware infections, and more. And these risks are rising. We’re seeing more third-party data breaches in the headlines, a surge in cyber-warfare targeting vendors as a potential back door to critical infrastructure, and increasing Ransomware-as-a-Service (RaaS) gangs that leverage AI to lower the bar to sophisticated attacks.
While there’s a lot that you can do to reduce your own cybersecurity risk, you still rely on your third parties to implement strong cybersecurity practices into their daily operations. You need to work with vendors that have a solid cybersecurity awareness culture, but it’s not something you can take for granted.
In this detailed guide, we will explain the importance of a third-party cybersecurity culture, and how to cultivate this ethos within your vendor organizations by setting clear expectations, establishing good communication channels, providing training and resources, and working together on security assessments, drills, incident response, and risk monitoring.
Understanding the Third-Party Cybersecurity Landscape
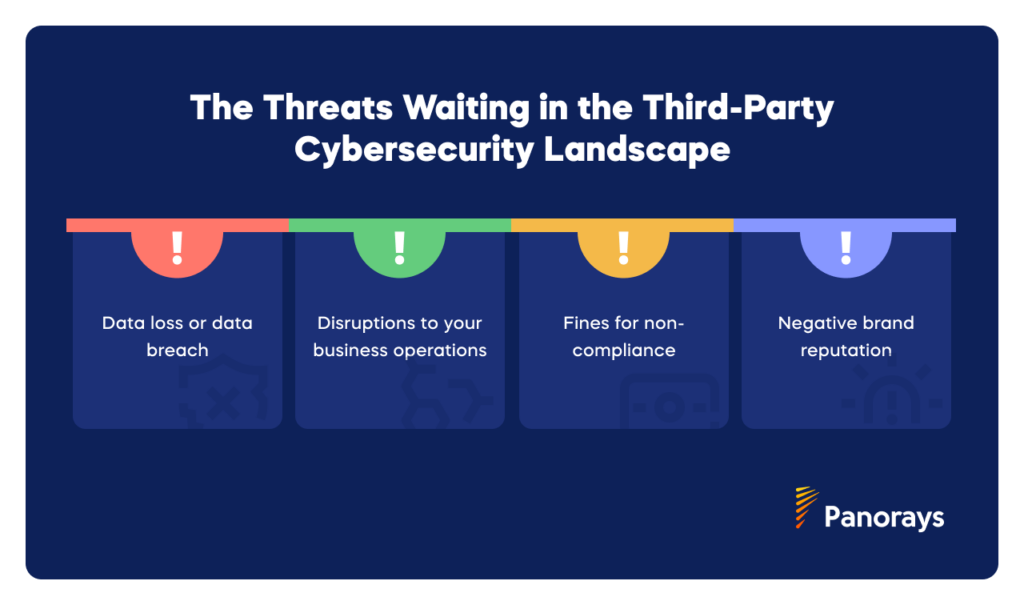
Third-party cybersecurity risks shouldn’t be taken lightly. If your vendors have weak cyber defenses or are successfully hacked by malicious actors, you could be facing serious data loss, disrupted business operations, fines for non-compliance with information security and data privacy regulations, negative brand reputation, and more.
In the UK, the National Health Service (NHS) was hit by a third-party cyber attack in June 2024, in which patient records were stolen and vital medical services were disrupted. Three weeks later, the NHS was still struggling to serve patients across the country. The same month saw a serious ransomware attack on software firm CDK Global. As a result, thousands of car dealerships in the US which use its platform had to suspend business operations for over two weeks.
How Nurturing a Cybersecurity Culture Mitigates Cyber Threats
Having a strong cybersecurity culture means that everyone involved in the organization consistently prioritizes and implements good cybersecurity habits. By embedding security as an integral part of everyday actions and decision-making, a cybersecurity culture lowers vulnerability to cyber attacks, increases compliance with industry standards, and ensures a rapid and effective response to any incidents.
Your vendors should be considered an integral part of your overall cyber posture. When they proactively work to prevent cyber attacks and lower cyber risk, it hardens your security posture, closing potential back doors that malicious actors could use to attack your systems. Working with vendors who have trustworthy cybersecurity practices helps minimize the risks of cyber threats. It also brings other benefits, like increased cyber resilience, and improved reputation and customer trust.
Creating a Cybersecurity Culture vs. Cybersecurity Training
Cybersecurity training is crucial for any robust security posture, but it’s only one aspect of a cybersecurity culture. When you nurture a cybersecurity culture, cybersecurity principles are integrated into your organization’s daily operations and ethos, influencing attitudes, behaviors, and decision-making at all levels. It means cultivating a mindset that sees security as a shared responsibility and a natural part of every action.
Cybersecurity training, however, focuses on educating employees about specific security threats, policies, and procedures. It usually involves structured sessions designed to increase awareness of and the best ways to respond to cyber threats.
Ultimately, training is an important element in building cybersecurity protections and resilience, but it’s not enough on its own to create the attitudes needed for a true cybersecurity culture.
Key Steps to Create a Cybersecurity Culture
Every company wants to nurture a cybersecurity culture throughout the organization and across all levels of its supply chain. Bear in mind that you’ll struggle to promote a third-party cybersecurity culture if it’s lacking in your own company. You need to get your house in order before you start addressing your vendors.
Once you’ve established a robust cybersecurity culture in your business, it won’t simply spread outwards on its own to take root in your third parties. You’ll need to actively create a third-party cybersecurity culture through intentional and strategic steps.
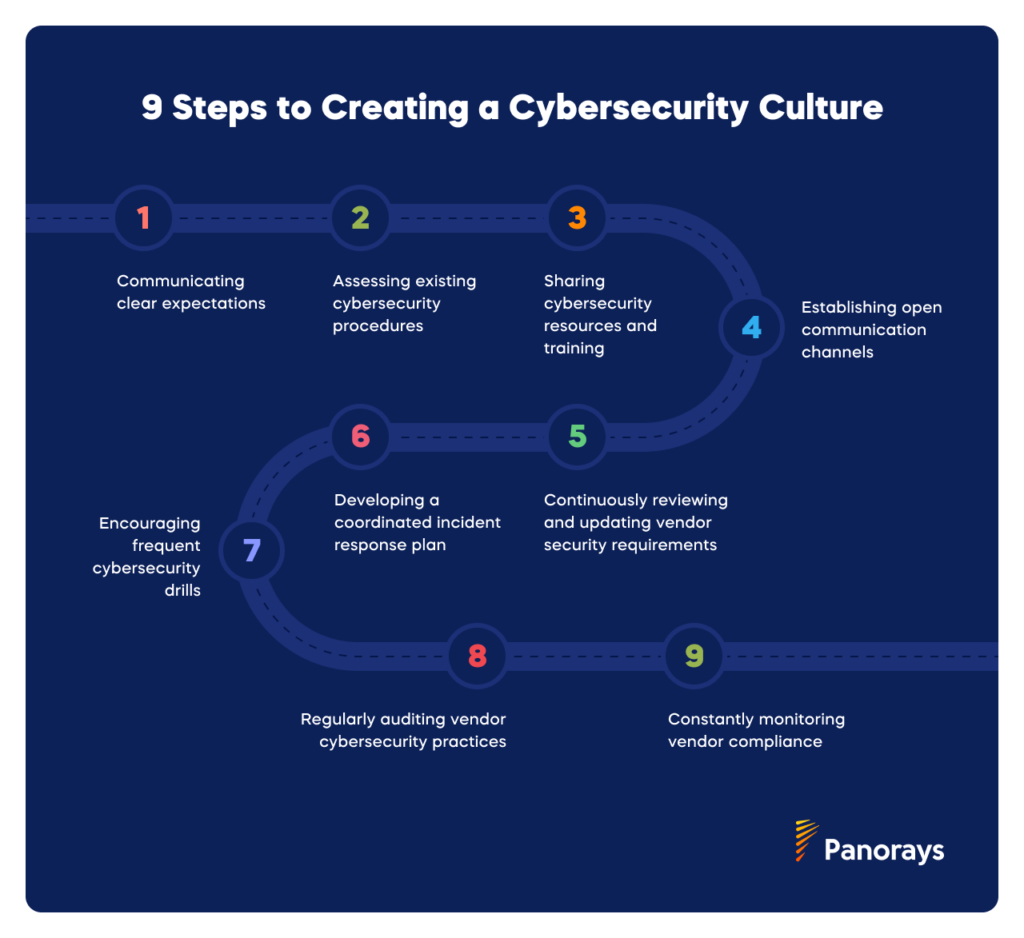
These should include:
- Communicating clear expectations about third-party cybersecurity practices and policies
- Assessing each vendor’s existing cybersecurity procedures
- Supporting vendors with cybersecurity resources and training capabilities
- Establishing open channels for communication about security concerns and incidents
- Encouraging frequent cybersecurity drills to rehearse incident response
- Developing and implementing a coordinated incident response plan
- Continuously reviewing and updating vendor security requirements
- Regularly auditing vendor cybersecurity practices
- Setting up tools and procedures for monitoring vendor compliance on an ongoing basis
In the next few sections, we’ll explain in more depth how to create this mindset and attitudes for all your third parties.
Establish Clear Cybersecurity Expectations and Requirements
It’s vital to set expectations from the beginning of your relationship with a vendor. This should include defining compliance with specific cybersecurity standards and regulations, specifying particular policies that they need to adhere to, and outlining the procedures and practices that they need to take in order to work with your organization.
Whatever security issues you define should be written into every contract and agreement that you draw up. Make sure that you communicate them clearly and comprehensively, so that your vendors know exactly what they need to do to meet your requirements. If something is vague or unclear, it could lead to misunderstandings and undermine your security posture.
Assess the Current State of Your Vendors’ Cyber Security
Before you can address your vendors’ cybersecurity culture, you need to know exactly how strong it is. This means carrying out a comprehensive cybersecurity risk assessment, covering all their cyber risk vectors and attack surface exposures.
In the process, you should:
- Examine their documented security policies and procedures
- Review their cybersecurity controls
- Run penetration tests to check their cyber defenses
- Analyze their incident response capabilities
- Evaluate their replies to security questionnaires
- Check security ratings and the results of previous audits
At the same time, it’s important to validate that they comply with all the relevant industry standards and regulatory requirements, including industry-specific standards and general data privacy and data security regulations.
It’s best to carry out this assessment on the basis of contextual risk, so that you prioritize more attention to high-risk vendors. Those third parties who have access to your sensitive data and/or critical business systems, or are vital for your continued business operations, should be the focus of your cybersecurity concerns.
Provide Regular Cybersecurity Training and Resources
Your cybersecurity posture is only as strong as that of your weakest vendor, so pay attention to their cybersecurity training programs. Encourage them to provide regular review sessions for their employees, and to use effective, up-to-date training methods and solutions.
It can be worth it to invest in advanced cybersecurity training simulations and other platforms, so that you can feel confident that your vendors fully understand cybersecurity issues.
Additionally, it’s best to share all the cyber threat intelligence, security updates, and best practices that cross your path. You want your vendors to be just as informed as you are about potential risks, so that they can prepare accordingly.
Foster Open Communication and Collaboration About Cyber Security
The last thing you want is for your vendors to avoid informing you about any cybersecurity incident or something that compromised their security posture. It’s crucial to encourage them to keep you updated about any changes in their cybersecurity capabilities or new threats. Model this transparency by sharing your information, and telling them about issues that you encounter.
To this end, ensure that there are open lines of communication between your organization and each of your vendors. Make it easy for them to send your security team a message or alert about new issues, and support them to ask questions and raise concerns at any time. Setting up communication channels that they can use to quickly report a security issue is a good way to remove friction from communication and enlist their cooperation.
Regular Cybersecurity Drills
Encourage your vendors to turn training into a habit. Ideally, they should perform regular cybersecurity drills that align with cybersecurity best practices and vendor management requirements. Frequent practice sessions help to stimulate readiness and increase awareness across your vendor’s entire organization.
Don’t forget to review their drills, to verify that they are meeting your expectations and check that they are covering all the points you expect. Evaluate the effectiveness of their response as shown in the drills, and consider their level of communication and overall performance. Through these activities, you enhance your understanding of their security positioning, and reinforce the importance of collaborative problem-solving and continuous improvement.
Respond to Security Incidents Effectively
Cybersecurity incidents can happen to any organization, even if your cybersecurity culture and that of your vendors is strong and you’re on the alert for any threats. That’s why it’s critical to prepare for a scenario where a vendor’s security is compromised, or you experience a data breach, malware infection, or other cybersecurity attack via a third party.
Develop a full incident response plan in coordination with your vendors. Include details about how you’ll manage a combined incident response, specify who will manage the overall operation, and delineate who will take responsibility for different aspects of it.
When a security incident does occur, collaborate with your vendors both during it and when evaluating it afterwards, to manage and mitigate risks more effectively in the future.
Review and Update Cybersecurity Policies Regularly
The cybersecurity landscape is constantly fluctuating, so your policies and response planning need to be dynamic. It’s important to keep tabs on emerging threats, new technologies, and other changes in the vendor landscape, so that you can adjust your third-party cybersecurity requirements accordingly.
Set regular intervals to review and update your vendor cybersecurity controls and policies, to ensure that they remain relevant and effective. By continuously revisiting your third-party cybersecurity regulations, you’ll be able to adapt to changes in the threat landscape, address vulnerabilities, and incorporate advancements in security practices.
Conduct Regular Security Assessments
Your initial cybersecurity assessment gives you a reasonable understanding of your vendors’ cybersecurity posture and policies, but that’s only a snapshot in time. Your vendors’ security controls, incident response abilities, and cyber readiness change constantly, just like the threat landscape, so you need to keep your awareness of their cybersecurity provisions up to date.
The best way to do so is to run regular security assessments and audits of their cyber practices. These should be slightly scaled-down versions of your initial assessment, including cybersecurity questionnaires, compliance criteria, penetration tests, and analysis of their incident response. Review their security documentation and security ratings frequently, because these can also change over time.
Implement Continuous Risk Monitoring and Reporting
Last but not least, you need to set up continuous risk monitoring and reporting so that you know about changes in your vendors’ cyber risk profile. Automated monitoring tools and systems can track vendor compliance with cybersecurity policies, delivering real-time or near-real-time information and alerts.
Along with this, you’ll need to establish reporting mechanisms for ongoing assessment and feedback. Make sure that your reports and dashboards are easy to read and understand. Ideally, insights for all your third parties should be available in a single central location.
You’ll probably want to adjust the settings on your monitoring tools, so that you aren’t overwhelmed with notifications whenever something changes with one of your vendors. You might choose to have high-risk vendors trigger alerts, while changes in other vendors are simply logged for periodic review. What matters is that you enforce regular times to evaluate them.
Promote a Culture of Security Among Your Vendors
A strong third-party cybersecurity culture is vital for any effective cybersecurity program. Your vendors are a crucial pillar of your overall cybersecurity preparedness, so building a cybersecurity awareness culture among them could be critical for your cyber posture.
By detailing your expectations and requirements for their cybersecurity provisions, encouraging clear and frequent communication on cyber issues and sharing effective training information and cyber risk resources, collaborating on cybersecurity drills and incident response, and maintaining ongoing vendor cybersecurity assessments, risk monitoring, and policy reviews, you’ll lay the groundwork for a robust and powerful cybersecurity awareness culture among all your third parties.
It’s never too late to revamp your vendor relationships concerning cybersecurity and cyber risk. Fostering a strong cybersecurity culture is the best way to nurture a secure vendor ecosystem and shore up vulnerabilities to cyber attacks. It should be a priority for every cyber risk-aware organization.
The best way to achieve this is by using Panorays. It’s the only third-party cyber management solution that maps your entire threat landscape and delivers up-to-date insights into your vendor cybersecurity culture. It continuously monitors and reassesses each vendor’s level of cybersecurity risk, in the form of a dynamic Risk DNA score.
With Panorays, you gain clear visibility into every vendor’s cybersecurity culture, can identify the steps they need to take to close vulnerabilities that could affect your cyber posture, and track changes in their profile. This makes it easy to evaluate vendor compliance, adjust the requirements you make from vendors, and adapt your own cybersecurity policies to proactively prevent your organization from falling victim to a third-party cyber attack.
Ready to build a comprehensive third-party cybersecurity culture? Get a demo of our third party risk management platform today.
Building a Cybersecurity Culture FAQs
-
Creating a culture of cybersecurity is a multi-step process. It involves continuous education and training about security awareness and practices at every level of the organization, together with promoting open communication about risks and incidents. By setting clear expectations and requirements around cybersecurity practices, integrating cybersecurity into everyday processes, and regularly updating policies to address emerging threats, you can nurture a culture of cybersecurity in your organization and among your vendors.
-
A cybersecurity culture is when everyone in the organization prioritizes and integrates cybersecurity into everyday activities. There’s an understanding that everyone has a shared responsibility to protect the business from cyber threats. In a strong cybersecurity culture, security measures and practices are embedded into the collective behavior, with every individual and team making them a fundamental aspect of their roles.
-
There are a number of ways to build a cybersecurity culture. For example, you should:
- Conduct regular, engaging training sessions that emphasize real-world scenarios
- Promote open communication about potential threats and incidents
- Involve everyone in cybersecurity exercises and drills
- Encourage employees and vendors to report suspicious activities
- Continuously monitor the threat landscape and update policies to reflect new threats



