DORA, or the Digital Operational Resilience Act to give it its full name, is a new set of laws enacted by the EU to increase resilience and trust within the financial services sector. It was passed in reaction to a recent wave of damaging supply chain attacks, so its main focus is to ensure that organizations minimize third-party risk as much as possible.
DORA explicitly requires organizations to monitor their third-party ICT providers for compliance., because organizational security is only as strong as that of the weakest third-party vendor. Third parties can undermine your operational resilience in numerous ways, from insufficient cyber defenses to poor user-access control and ineffective anti-phishing training, any one of which can pose serious vulnerabilities.
Effectively managing third-party risk in alignment with DORA’s regulatory requirements can be challenging. It requires identifying every entity in your supply chain, including fourth and fifth parties; assessing concentration risk; and mapping and monitoring threats to your supply chain on an ongoing basis.
In this detailed guide, we’ll explain DORA compliance and discuss how to identify and assess third-party risk, the best ways to monitor threats and the role that risk management has to play in simplifying and strengthening DORA compliance.
What Are Third-Party Risks?
Third-party risks are any kind of risk to your organization that stems from one of your third (or Nth) parties. It could affect your reputation, your financial stability, your ability to maintain operations, or any other part of your business. But the biggest nightmares come from cyber-related risks.
Third-party cyber risks can come in many shapes and sizes. They include:
- Cybersecurity threats, such as malware attacks that compromise sensitive information.
- Data breaches due to unauthorized access to data by external entities.
- Operational disruptions if a third party experiences a failure or downtime that affects your organization’s services.
- Reputational damage and/or penalties from non-compliance with regulatory standards.
- Network vulnerabilities that can expose your systems to malicious actors.
Why DORA Compliance Requires Third-Party Risk Management
DORA is all about making sure that you can meet your obligations to customers and clients without disruption or causing harm. But without effective third-party risk management (TPRM), you can’t ensure the integrity, security, or continuity of your operations.
The law recognizes that external providers are integral to the operations and security of financial services, so it mandates that financial institutions develop robust frameworks to manage third-party risks. One central element is drawing up and maintaining a Register of Information, which lists all your connections with ICT vendors.
It also requires financial services providers to conduct thorough due diligence when selecting third-party providers, assess their resilience, and regularly monitor their performance. You have to carry out continuous risk assessments to show that you’ve identified and anticipated all potential threats, and demonstrate contingency plans to ensure continuity of services.
The Key Requirements of DORA Compliance for Third-Party Management
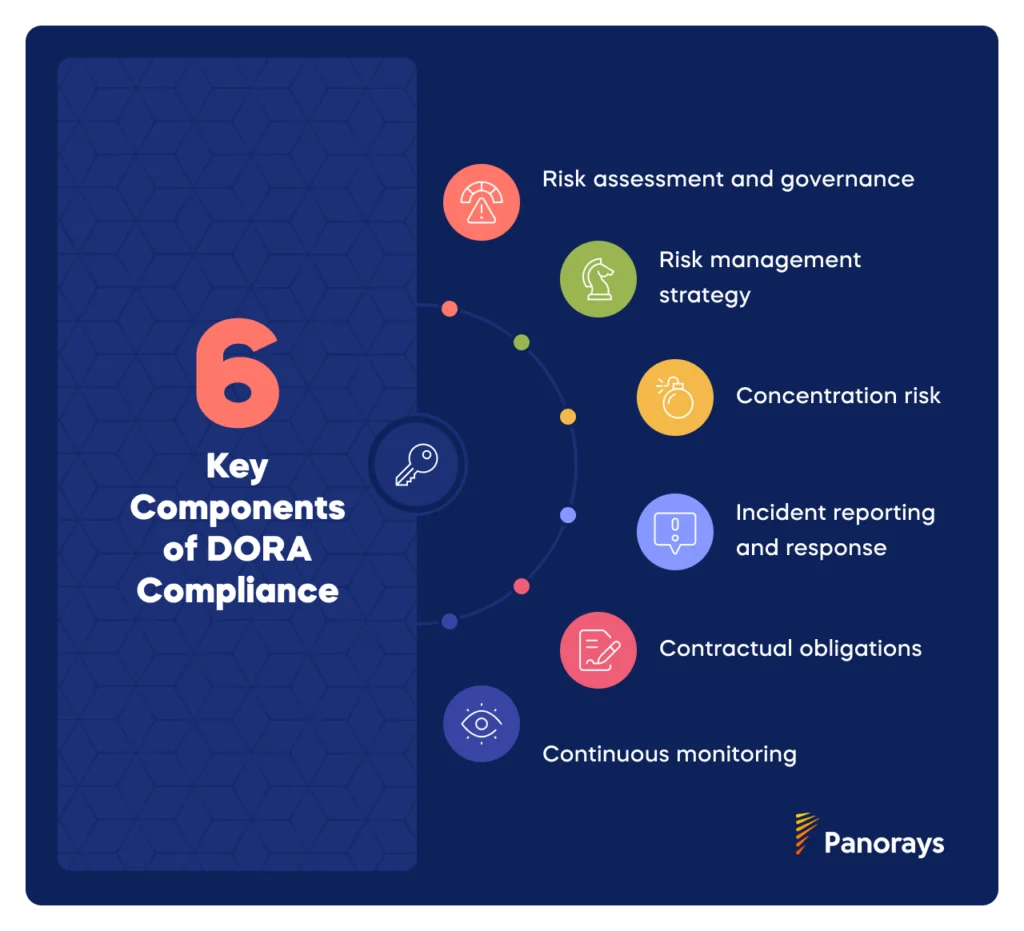
DORA compliance affects third-party risk management in a number of ways. These include:
- Risk assessment and governance. Financial institutions must conduct thorough due diligence and risk assessments before engaging with third-party providers, to evaluate their operational resilience and cybersecurity capabilities.
- Risk management strategy. Organizations need to implement a third-party risk management framework, such as ISO 27001/2, and a plan to identify all their Nth parties and designate those that are crucial for business operations.
- Concentration risk. DORA requires companies to create a Register of Information that lists all third parties that support vital functions and/or have access to sensitive data and to avoid over-reliance on a few providers, which could lead to concentration risk.
- Incident reporting and response. Financial services providers need to set up clear incident response and recovery plans to minimize disruption from any issues that arise. They need procedures to quickly spot, mitigate, and report incidents.
- Contractual obligations. The act mandates that organizations include specific clauses in their contracts with third parties, which enforce security controls, incident reporting, and audit rights.
- Continuous monitoring. Financial entities need to monitor third-party risk in an ongoing way, tracking their security posture and performance, and conducting regular tests like scenario-based testing, vulnerability assessments, and threat-led penetration testing.
Identifying and Assessing Third-Party Risks
TPRM is a crucial element of DORA compliance. You need to identify, assess, and address the potential risks posed by your ICT vendors and subcontractors in an organized and ongoing manner. There’s no other way to diversify your supply chain and ensure that you can deliver business services without serious disruption.
This involves identifying and mapping all your third-party risks; evaluating risk levels and categorizing third parties accordingly; and carrying out due diligence throughout the onboarding process.
Risk Identification
Detecting and mapping all your third-party risks is a prerequisite for effective risk management. This is itself a multi-step process. The first step is to build an inventory of all third parties, including fourth and fifth parties. Most enterprises need a tech tool to bring visibility into their entire supply chain.
Then, you’ll need to review each entity’s infrastructure for vulnerabilities and assess their data handling and encryption practices. It’s also crucial to thoroughly investigate their overall cybersecurity measures, including checking their response to past security incidents.
Risk Assessment and Prioritization
It’s just as important to evaluate the criticality of each of your third parties. This way, you can categorize them based on their level of risk, and prioritize risk management efforts and resource allocation for the highest-risk vendors.
One common approach is risk scoring, which assigns each third party with a score that reflects their risk level. The score is calculated using various criteria, including the sensitivity of the data they handle and their past cybersecurity performance. Another method is tiering, which places vendors into different tiers depending on how essential their services are to business continuity and core business functions.
Onboarding and Due Diligence Process
Carrying out thorough due diligence is a specific requirement for DORA compliance, and vital for revealing third-party vulnerabilities. It’s essential for mitigating risks related to operational disruptions, data breaches, and compliance violations. Before you sign a contract with a third party, you need to verify that this vendor meets DORA standards for resilience.
Effective due diligence usually involves vendor questionnaires, security audits, reviewing security documentation, and checking security rankings. It’s best to use an automated platform that can customize the process for each company.
How Continuously Monitoring Vendors Helps Achieve DORA Compliance

DORA explicitly obligates financial services providers to monitor and document their ICT subcontracting chain in an ongoing manner. Continuous monitoring is also vital for complying with other elements of DORA, because it ensures that you can promptly detect and respond to any vulnerabilities or disruptions in your services.
The best way to monitor complex supply chains is by using automated tools like Panorays, which constantly monitor and evaluate third-party performance and risk exposure. It tracks KPIs, runs continual security assessments, and issues an alert if it detects any changes in an entity’s security posture. Regular audits and strong communication with vendors are also important elements in a robust monitoring strategy.
Vendor Performance Metrics
Vendor performance metrics give you a quantifiable way to assess and manage third-party risk. Key metrics to track include:
- Uptime, which shows the availability of a vendor’s services and helps ensure that critical operations remain uninterrupted.
- Cybersecurity posture, which reflects the vendor’s ability to protect against cyber threats and breaches and maintain data integrity and security.
- Incident management metrics, which assess how quickly and effectively the vendor deals with incidents and minimizes impact.
- Regulatory compliance metrics, which ensure that vendors adhere to relevant laws and regulations as part of DORA requirements.
Incident Response Planning
Responding swiftly to incidents, reporting them quickly, and minimizing the impact they have on business operations is a key element in DORA compliance. Every financial organization needs a well-defined and fully-tested response plan for incidents that involve third-party vendors.
Your plan needs to align with DORA guidelines. This requires defining clear procedures for identifying, reporting, and responding to incidents, and allocating roles and responsibilities to various stakeholders. You’ll need to set up protocols for communicating with vendors during a crisis, so that you can work together efficiently even under stress. Finally, every plan must be tested thoroughly, so that you’ll know it’ll be effective if you end up needing it.
Strengthening Contracts and SLAs for DORA Compliance
A number of DORA regulations relate to the contracts and SLAs that you agree with your third parties. The law requires you to clearly address risks that could disrupt business continuity, and include specific provisions for managing risks associated with critical functions and data security.
Your contracts need to define roles and responsibilities around incident response and reporting, and SLAs should lay out expectations around service availability. You should also include clauses allowing for regular audits and access to relevant information, and specify termination rights that would end the contract if your vendor doesn’t meet DORA standards.
Contractual Obligation Requirements for DORA Compliance
You’ll need to include specific obligations in your contracts with third-party vendors, so you have a mechanism to address any deficiencies in their compliance posture. Make it clear that failing to meet these requirements would be grounds for terminating the contract.
These should cover two main areas: the vendor’s responsibilities to deliver key services, and your right to carry out ongoing monitoring, audits, and assessments to make sure that they adhere to DORA regulations.
A robust contract should include:
- The vendor’s responsibilities regarding service availability, data protection, and incident management and reporting;
- Audit rights for you to regularly assess the vendor’s performance, security practices, and DORA compliance;
- Compliance obligations that ensure that they are continuously aligned with DORA and other relevant legal requirements, including regular reporting.
Service Level Agreement (SLA) Requirements for DORA Compliance
Detailed SLAs should be part of every contract that you sign with a third-party vendor, because they hold vendors accountable for meeting DORA standards of operational resilience. Defining specific standards that vendors need to meet sets expectations for vendor performance, risk management, and regulatory adherence.
SLAs should include performance metrics such as uptime and incident response times, together with cybersecurity and risk management measures that vendors need to implement to protect against threats and breaches. You should also cover audit rights and compliance obligations, so that you can verify their ongoing alignment with DORA requirements and quickly spot any issues.
Achieving DORA Compliance Through Collaborative Risk Management
All your vendors are part of a shared risk ecosystem, so the only way to truly ensure DORA compliance is to include them in a collaborative approach to risk management. You need all your third parties to work together to manage risks that could undermine your operational resilience.
This involves a number of tactics, including fostering open communication, involving vendors in training and joint risk assessments, and aligning risk management practices to increase a sense of shared responsibility. These strategies help ensure that all parties are equally committed to DORA compliance.
Collaborative Risk Management Strategies
It’s vital to implement strategies that encourage a collaborative approach to risk management. Establish regular communication channels to discuss potential risks, share threat intelligence, and brainstorm better ways to address emerging risks. When you maintain an open dialog, it promotes a joint commitment to operational resilience that goes beyond DORA compliance box-ticking.
It’s best to include vendors in scenario planning and joint incident response exercises, so you can test your preparedness for potential disruptions and refine response strategies together. Sharing best practices and security intelligence can enhance the overall resilience of the digital supply chain.
Vendor Training and Awareness
Best practices for DORA compliance include running training and awareness programs for your vendors. You’ll need to first carry out a thorough risk assessment to highlight gaps in their DORA compliance, so you can develop training programs that are customized to that vendor’s risks and compliance challenges.
It’s best to write participation in training programs into your vendors’ contractual obligations, so you’ll know that they are aware of their responsibilities and have the necessary knowledge and tools. Interactive workshops, webinars, and scenario-based exercises are most effective at engaging vendors. Make sure your education efforts are ongoing, so that vendors stay updated on evolving regulatory requirements and threats.
Shared Responsibility for Operational Resilience
The whole point of collaborative risk management is to spread the burden of maintaining operational resilience. This means first aligning vendor practices with your current risk management strategy, ideally by including requirements to adhere to the same resilience standards in your contracts and SLAs.
It’s a good idea to regularly include vendors in joint risk assessments and resilience exercises, to turn them into active participants in your risk management strategy rather than just external service providers. This helps create an environment where both parties are equally committed to meeting DORA’s operational resilience requirements.
Leveraging Risk Management Technology and Platforms
Supply chains have grown more complex and extensive in the last few years, making it a challenge to manage third-party risks. Enter risk management technology and platforms like Panorays, which bring automation to streamline risk assessments, monitoring, and reporting processes.
The right tools simplify risk assessment with AI-powered security questionnaires, detailed reports, and automated evaluations that produce trustworthy, dynamic risk scores. A good TPRM platform has features like automated continuous monitoring for vendor performance, automated alerts for potential issues, and easy-to-read dashboards to track compliance and performance metrics.
Integrating Technology with Compliance Efforts
The right technology can take a lot of the headache out of DORA compliance. It streamlines risk management processes and improves transparency across your digital supply chain. With effective tech solutions, you can map your entire supply chain to uncover hidden vendors, as required for the DORA Register of Information, and analyze each vendor’s risk level to identify potential concentration risks.
Automated risk assessments, vendor monitoring, and incident reporting are more efficient and less prone to errors than manual processes, helping you maintain visibility into fluctuating risk levels, discover emerging threats before they become serious, and meet reporting requirements. Technology also improves communication and documentation by ensuring that actions taken to mitigate risks are well-documented and easily accessible for audits.
The Importance of Managing Third-Party Risks to Achieve DORA Compliance
As of January 2025, DORA compliance will become mandatory, so there’s no time to waste getting your compliance ducks in a row. DORA regulations focus on steps to limit concentration risk and lower the chances of serious disruption to business operations, making it the best way to maintain operational resilience and safeguard against vendor-related risks.
With third-party risk placed front and center of DORA regulations, effective TPRM is crucial for DORA compliance. Identifying and assessing third-party risks, onboarding vendors with contracts and SLAs that bake in DORA compliance, and establishing continuous monitoring and robust incident response strategies are all vital elements for meeting DORA requirements.
The average enterprise will need to leverage tech tools to achieve these goals. Panorays brings advanced capabilities to simplify and streamline the steps involved in DORA compliance. These include:
- Detailed supply chain mapping to reveal all your third, fourth, and Nth-parties, as required for the DORA Register of Information.
- A dynamic Risk DNA score for each vendor, which helps pinpoint potential concentration risks and identify vendors that need priority attention.
- Continuous monitoring and threat detection that provides early alerts about changes in vendor compliance posture and potential emerging threats.
- Customized security plans for each vendor, to ensure effective and swift incident response and resolution.
Ready to get DORA compliance under control? Contact Panorays to learn more.



