Every company carries a long tail of vendors, suppliers, and third parties which provide vital services, but which also represent a potential threat. In today’s connected world, each vendor offers malicious actors a doorway to the IT networks and systems that you rely on to maintain business operations.
Since your organization can’t cut itself off from this ecosystem of vendors, you need to manage the cyber risk that they represent. Effective vendor risk management limits your vulnerability to cyber attacks and minimizes the risk of disruptions to your business operations, and it all begins with vendor risk assessment.
Third-party vendor risk assessment refers to identifying, analyzing, and taking steps to mitigate the risks associated with third-party vendors. In this detailed guide, we will explain all you need to know about vendor risk assessment, how to complete assessments effectively and efficiently, and best practices to minimize vendor risk.
What is Vendor Risk Assessment?
The goal of any good vendor risk assessment process is to identify every type and aspect of vendor risk on an ongoing basis. You can’t reduce inherent risk if you don’t know that it exists or where it lies, and you can’t protect your business until you’ve identified the likely vector, source, and scope of residual risks.
For example, a third-party vendor might have poor cyber security which puts your own operating systems at risk, or fail to comply with regulations in ways that undermine your compliance posture. Other types of risk could affect your data privacy and security, financial stability, or brand reputation.
It’s also important to review inherent, profiled, and residual risk.
- Inherent risk is that posed by a vendor’s activities and context before you take any steps to mitigate it.
- Profiled risk refers to specific risks documented in a particular vendor, based on their unique characteristics, performance, and relationship with your organization.
- Residual risk is the risk that remains after you’ve implemented risk control measures.
What Does a Vendor Risk Assessment Cover?
A comprehensive vendor risk assessment goes beyond surface-level checks. It examines every aspect of a vendor’s operations, security posture, and reliability to determine how their weaknesses could impact your organization. The goal is to understand not just if a vendor poses risk, but where that risk originates and how it could affect your data, compliance, and business continuity. Each of the following areas plays a critical role in building a complete vendor risk profile.
1. Vendor Security Controls
Checking that your vendors have appropriate security controls is a priority for any effective vendor risk assessment. You want to check that they have robust processes for patch management and software updates; regularly scan for vulnerabilities and anomalies; keep on top of threat intelligence; and have reliable incident response policies.
2. Vendor Privacy
Your VRA should carefully evaluate each vendor’s privacy controls, both to verify that they’ll protect your data and to ensure that they won’t harm your compliance with privacy regulations like GDPR. Make sure each vendor has strong identity and access management (IAM) processes and credentials management protocols, with features like multi-factor authentication (MFA) and encryption by default.
3. Vendor Confidentiality Policies
It’s important to check your vendors’ commitment to keeping sensitive information confidential. This means not just protected customer data and personal identifying information, but also your proprietary information. You need to be confident that it won’t be leaked to competitors, especially if your rivals work with the same vendor.
4. Vendor Data Policies
Now that data is the new oil, it’s more crucial than ever to keep it free from contamination. Before you grant a vendor access to your data sources and repositories, you need to be sure that they understand the importance of good data stewardship and will adhere to your data governance policies, so that the integrity of your information isn’t harmed.
5. Vendor Data Workflow
Some of your vendors analyze your data to produce new insights. Others might collect and/or process data on your behalf, which enhances your understanding of your business context and helps you with decision-making and strategic planning. But can they produce that data when you need it? Make sure that your vendors can deliver data insights in a timely manner and on the issues that most concern you.
6. Vendor Financial Stability
If one of your vendors is financially unwell, your own finances could catch a cold. Carefully investigate each vendor’s financial standing and cash flow stability. The last thing you want is for a vital vendor to suddenly declare bankruptcy or struggle to pay its own bills. If it goes down, you could be left without critical services.
7. Vendor Reputation
If your business is linked with a company that has a poor reputation, it can muddy your own brand name. Make sure that you run a thorough assessment of each vendor’s commitment to sustainability, ethical business practices, regulatory compliance, and other key issues. If your customer base is highly concerned about a specific issue, such as carbon emissions, you should check that vendors respect and meet those expectations.
How Do You Perform a Vendor Risk Assessment?
Conducting a vendor risk assessment requires a structured, repeatable process to ensure no gaps are missed. The goal is to identify which vendors pose the greatest risk, evaluate their controls, and take proactive steps to mitigate potential issues. The following steps outline how to perform a thorough and efficient vendor risk assessment from start to finish.
Identify critical assets and vendors
The first step is to make sure that you know both who your vendors are, and what assets you possess. You need to know which entities are lurking in your supply chain, otherwise you can’t assess them. You also need to be aware of every database, network, and other business asset in your ecosystem, so that you can control access to them and monitor their security.
Determine risk tolerance
Before you get stuck into the vendor risk assessment process, you need to decide what levels of risk you’re willing to accept from your vendors. Your risk tolerance might vary for different areas, like data security, compliance, or operational continuity. You also might have a higher risk tolerance for less-critical vendors. Once you define your risk tolerance, you can use it to guide your decision-making.
Gather information about the vendor
Now you’re ready to collect the information you need to evaluate each vendor’s risk profile. This might include their security policies, financial documentation, compliance and incident history, and brand reputation. You may interview key stakeholders to get a deeper understanding of the company, and/or visit the business site yourself.
Evaluate the vendor’s products and services
Next, take a close look at the products and services that the vendor is offering. You want to be sure that they meet your needs, and that the quality and security levels align with your expectations. This includes reviewing how the products are developed, maintained, and supported, as well as potential vulnerabilities they may introduce.
Generate security ratings
Security ratings give you a clear and quick way to measure each vendor’s security risk profile. You’ll need to use a specialist firm or solution to crunch data and produce a single, quantifiable score. Once you have security ratings, you can use them to compare different vendors and choose those that meet your security requirements.
Send out security questionnaires
Security questionnaires complement security ratings to give you a more comprehensive understanding of vendor cybersecurity risks. Customize your security questionnaires so that they address the issues that most concern your organization, and are relevant to each vendor’s criticality and level of access to your data and systems.
Tier vendors by criticality level
After you’ve gathered all the relevant data, completed vendor evaluations and security questionnaires, and acquired clear benchmarks like security ratings, prioritize vendors for deeper examination and/or mitigation. This helps you to allocate resources appropriately, and prevents serious risks from slipping through the cracks.
Track for data leaks
A vendor risk assessment isn’t a once-and-done activity. Although the main work is carried out when a vendor first joins your supply chain, vendor risk doesn’t stay static. It’s important to monitor your vendors for any changes in their risk levels, and especially for the first signs of data leaks and breaches. This way, you can resolve them quickly and prevent them from escalating.
Why is Vendor Risk Assessment Important?
Vendor risk poses a serious threat that could cause real damage to your operating systems, reputation, finances, and more if left unmanaged. For example, Microsoft saw a significant rise in negative sentiment after a systems crash in July 2024, caused by a misconfigured update from its vendor CrowdStrike.
A zero-day vulnerability in the vendor MOVEit exposed sensitive health data and personal identifying information (PII) held by many organizations, affecting millions of people. It’s just one of many data breaches that occurred in 2023 due to vendor relationships. Data breaches can bring financial penalties, as well as harm customer trust for the long term.
MGM Casinos lost an estimated $100 million from a cyber attack that exploited third-party weaknesses around access controls and MFA, allowing hackers to access MGM data and disrupt vital business operations. All these risks should be detected and addressed by a vendor risk assessment.
Key Components of Vendor Risk Assessment
The essence of vendor risk assessment covers a number of issues. You need to consider all the possible risk vectors, including regulatory risk, operational risk, reputational risk, financial risk, geographic risk, cybersecurity risk, and data privacy risk.
When reviewing vendors, look at their exposure to physical risks such as natural disasters or social upheaval, which could disrupt their operations, as well as digital exposure. Their IT networks and systems, applications, and human access parameters should all be examined to evaluate their attack surface exposures.
It’s also crucial to assess vendor risk in the context of their relationship with your organization. A certain level of risk might be acceptable for a peripheral vendor which has no access to your data, but indefensible for a vendor that provides vital services and accesses proprietary or sensitive customer data.
Vendor Risk Assessment Tools and Methods
Your vendor risk assessment process needs to be multi-faceted, using security questionnaires, on-site audits, security rating platforms, and third-party risk management (TPRM) platforms.
Questionnaires
Creating and sending a list of questions about the vendor’s security practices and controls is the foundation of risk assessment practices. Your questionnaires should cover issues like network security, data protection policies, access controls, incident responses, and regulatory compliance. It’s best to customize questionnaires according to the vendor’s level of risk and access to your data and systems. Standardized templates can help ensure that you address every issue.
On-site audits and assessments
Visiting your vendor’s site to directly observe their environment and practices can reveal vulnerabilities that might not be evident through other assessment methods. An on-site audit involves reviewing the vendor’s processes, inspecting facilities, interviewing staff, and examining documentation to verify that the vendor adheres to agreed-upon standards and best practices. Audits are typically carried out by your risk management team or third-party auditors.
Security ratings
Security ratings, usually provided by specialist firms, focus on cybersecurity risk. They use data from automated tools and public sources to deliver objective, quantifiable evaluations. It’s best to combine security ratings with questionnaires, to gain a more complete overview. With vendor security ratings, you can benchmark and compare multiple vendors to identify high-risk vendors and prioritize those needing further scrutiny.
Third-party risk management platforms (TPRM)
Advanced TPRM platforms are comprehensive solutions that streamline risk assessment. They deliver a holistic view of your vendors’ risk profile by integrating various risk assessment methods, including security ratings, questionnaires, and audits, into a centralized system. TPRM platforms also offer workflow automation, risk-scoring models, real-time updates and alerts, and reporting tools and dashboards.
Steps to Conduct a Vendor Risk Assessment
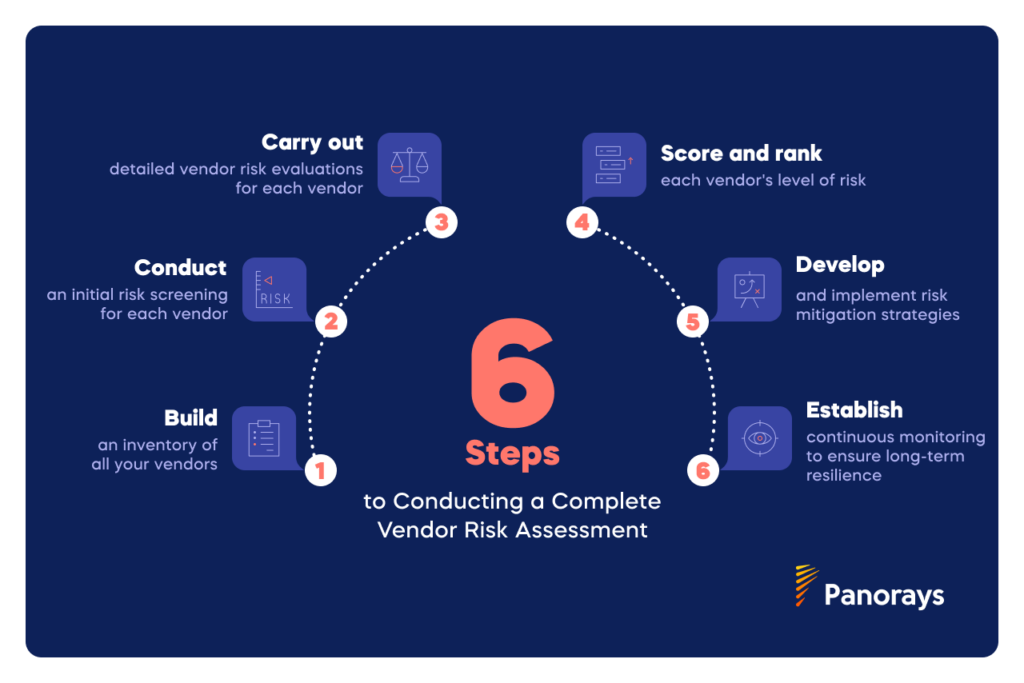
Carrying out a vendor risk assessment can seem daunting, but it’s crucial to do it properly. You’ll need to do a vendor inventory, conduct an initial and then more detailed risk analysis, and score and rank your vendors. Then you’ll be ready to take steps to mitigate the risks you discover. Finally, you’ll want to ensure that vendors are continuously monitored for changes in their risk score and the rise of potential vulnerabilities.
Here’s a deeper explanation of what’s needed for effective vendor risk assessment.
Step 1: Vendor Inventory
You can’t assess your vendors for risk until you know who they are. Creating an inventory of all your vendors ensures that you don’t overlook anyone, and allows you to approach risk assessments in a systematic way.
Many companies struggle to identify their fourth to Nth party vendors, who can easily rest unnoticed deep in the supply chain. Knowing your vendors’ vendors means you have total visibility into every organization that could access your company data.
Make sure that you include low-risk business partners, such as marketing tools and calendar integrations. Once you’ve built a comprehensive list of vendors, you can classify them according to their risk level and how critical they are to your business operations.
Step 2: Initial Vendor Risk Screening
Next, you’ll want to carry out a quick preliminary assessment. This helps you to identify which vendors carry the highest risk so that you can prioritize them for more detailed, in-depth evaluations. It helps ensure that critical risks are addressed promptly and guides you to allocate resources more effectively to protect the organization’s assets and data.
Your initial screening should be designed to gather essential information about a vendor’s security practices, compliance, and overall risk profile. It’s best done using questionnaires that are customized according to the vendor’s access to your data and importance to your organization. An automated platform that can use standardized templates and adapt questionnaires for each vendor’s circumstances helps screen vendors quickly and efficiently.
Step 3: Detailed Vendor Risk Assessment
You’ll use the results of your initial screening to classify vendors for a detailed risk assessment, using a risk assessment platform that can conduct numerous tests across the vendor’s ecosystem and into all their existing assets. Make sure that it covers networks, IT systems, applications, and human vulnerabilities, to reveal all possible security gaps.
A detailed risk assessment typically includes an on-site security audit, where auditors physically visit the vendor’s site to assess various aspects of the vendor’s security, test the effectiveness of existing security controls, and identify any vulnerabilities or gaps that could pose risks.
In addition, you’ll check if the vendor’s security policies and procedures align with industry best practices and regulatory requirements. This involves examining documentation such as security policies, access control protocols, data encryption practices, and disaster recovery plans.
Step 4: Vendor Risk Scoring and Ranking
When you have the results of all your various risk assessment methods, you’ll need to use a platform like Panorays to generate an overall qualitative risk score for each vendor. You can customize how much weight is given to various criteria, like compliance, data protection, and incident response, depending on how important it is to you.
Then you can produce a standardized measure of their risk level, and use that to organize risk management efforts and make informed decisions about vendor relationships. Vendors with higher risk scores have a higher potential to damage your organization, so you want to prioritize them for further scrutiny, mitigation strategies, and ongoing monitoring.
This ranking allows organizations to focus their resources on the most critical areas, ensuring that high-risk vendors are managed more rigorously while maintaining a balanced approach to lower-risk vendors.
Step 5: Vendor Risk Mitigation
Developing and implementing strategies to address the risk that you’ve identified is a crucial step in protecting your data and systems. By proactively addressing identified risks, organizations can significantly reduce the likelihood of security breaches, data leaks, and other disruptions.
You’ll want to create a detailed risk mitigation plan for high-risk vendors, tailored to each vendor’s specific risk profile, which outlines the necessary controls and safeguards to reduce or eliminate vulnerabilities. It should include continuous monitoring and periodic reassessments.
A risk mitigation plan could require actions like enhancing security protocols, enforcing stricter access controls, requiring regular security audits, and ensuring compliance with industry standards and regulations. Additionally, you might request that vendors adopt specific cybersecurity tools, conduct employee training, or improve their incident response capabilities.
Step 6: Continuous Monitoring of Vendor Risk
Regularly reassessing vendor risks and updating risk scores is crucial for maintaining an accurate understanding of potential threats. Your vendors’ security environments and risk profiles evolve over time, so you need to continuously monitor them to ensure that any new vulnerabilities or compliance issues are promptly identified and addressed.
You’ll want to set up processes to regularly track and evaluate the security posture and risk profile of vendors. It’s best to use automated tools and systems that provide real-time or near-real-time updates on various risk factors, such as changes in a vendor’s security status, compliance issues, or emerging threats. Look for solutions that offer automated alerts for significant changes, and periodic reviews of vendor performance.
This proactive approach helps organizations respond quickly to emerging risks, adjust their risk management strategies as needed, and ensure ongoing protection of their data and systems.
Common Pitfalls and Challenges of Vendor Risk Assessments
Even well-designed vendor risk assessment programs can fall short if key challenges are overlooked. One of the most common mistakes is relying on one-size-fits-all questionnaires that fail to account for vendor criticality or the specific risks each supplier presents.
This approach often leads to incomplete or misleading results. Another frequent pitfall is neglecting fourth-party risks, vendors’ own supplier,s which can introduce hidden vulnerabilities deep within the supply chain. Additional challenges include inconsistent risk scoring, poor data validation, and treating assessments as one-time exercises instead of continuous processes. Addressing these gaps is essential for achieving accurate, actionable risk visibility.
Best Practices for Vendor Risk Assessment in 2026
Robust vendor risk assessment doesn’t arise in a vacuum. There are certain best practices that help organizations to effectively manage vendor-related risks.
Developing a detailed vendor risk assessment framework, implementing the right technology and tools, and ensuring smooth collaboration and communication within your organization and with your vendors are all critical to establishing a comprehensive and structured approach to vendor risk assessment.
By integrating these practices into your overall risk management strategy, your organization can ensure consistent and thorough evaluations, proactive risk mitigation, and enhanced security posture, ultimately fostering more secure vendor relationships.
Vendor Risk Assessment Framework Development
A structured vendor risk assessment framework is a system that guides your approach to evaluating and managing risks associated with third-party vendors. It’s a critical best practice because it ensures consistency, thoroughness, and repeatability in assessing vendor risks.
With a well-developed risk assessment framework, you can make informed and objective decisions about your third-party relationships. It should define a standardized series of processes, criteria, and methodologies for risk assessment, along with clear procedures for evaluating vendor performance, scoring risk levels, and implementing mitigation strategies.
A risk assessment framework shouldn’t stand alone, however. Integrating it into your overall risk management strategy ensures that vendor risks are considered alongside other critical risk factors, allowing for a comprehensive approach to risk mitigation. It’s essential for aligning vendor risk management with broader organizational goals and risk management practices.
Vendor Risk Assessment Technology and Tools
As vendor networks and business supply chains have grown more complex and extensive, the burden of assessing and managing vendor risk has increased. It’s very difficult for the average business today to identify all its vendors, let alone to assess, score, and mitigate risk for them all. With threats emerging faster than ever, it’s also extremely challenging to monitor changing risk levels in a way that delivers reliable visibility.
This is why organizations need to leverage advanced technology. The right tech allows organizations to feel confident that they are controlling vendor risk as much as possible. TPRM platforms, security rating tools, and other risk assessment solutions bring the capabilities that your company needs for effective risk assessments. These include automated continuous monitoring solutions, real-time alerts about serious threats, and AI-powered questionnaires and surveys.
Vendor Risk Assessment Collaboration and Communication
It’s important not to see vendor risk assessment as a competitive exercise that pits your organization against your vendors. It should be a collaborative process. Open and transparent communication helps build trust and fosters a cooperative relationship where vendors are more likely to comply with security and risk management requirements.
Establish clear communication channels and expectations with vendors, including regular updates, feedback loops, and clear guidelines on compliance and security expectations. This can involve periodic meetings, detailed documentation of security policies, and setting up dedicated points of contact for risk-related queries.
Internal stakeholders, such as IT, legal, procurement, and compliance teams, help you gain a comprehensive understanding of the risks and impacts associated with third-party vendors. Including diverse perspectives and expertise to inform the risk assessment process leads to more accurate and holistic evaluations.
The Future of Vendor Risk Assessment: 2026 and Beyond
As the vendor ecosystem continues to expand and digital supply chains become more complex, vendor risk assessment will evolve to meet new technological and regulatory realities. The future of this discipline lies in automation, intelligence, and integration—where data moves faster than threats and risk management adapts in real time. The following trends will define how organizations assess, manage, and mitigate vendor risk in 2026 and beyond.
Emerging Cyber and Third-Party Threats
Supply chain attacks are becoming more sophisticated, targeting not only vendors but also their fourth- and fifth-party connections. Cloud misconfigurations, identity breaches, and open-source vulnerabilities are introducing new pathways for exploitation. Organizations must adopt layered defense and threat intelligence integrations to stay ahead.
Evolving Risk Assessment Strategies
Future-ready programs will prioritize continuous monitoring over annual reviews. Automated validations will replace manual questionnaires, while data-driven scoring and integrated orchestration will ensure risk insights flow seamlessly between procurement, security, and compliance teams.
New Tools and Technologies
Innovation will drive a new wave of vendor risk management capabilities.
- AI-powered risk scoring: Advanced models will evaluate vast datasets to predict vendor vulnerabilities before incidents occur.
- Autonomous agents: Intelligent bots will continuously collect, verify, and update vendor data across multiple sources.
- Orchestration platforms: Unified systems will connect TPRM, GRC, and procurement workflows to eliminate silos.
- SBOM and provenance tools: Software Bill of Materials (SBOM) and supply chain provenance technologies will bring unprecedented transparency into software components and dependencies.
Regulatory and Compliance Outlook
Global regulations like DORA, NIS2, and evolving data protection laws will continue to raise the bar for vendor oversight. Organizations will need to demonstrate continuous compliance and real-time evidence of control effectiveness across all third-party relationships.
Modernizing Vendor Risk for 2026 and Beyond
The future of vendor risk assessment is intelligent, automated, and collaborative. By embracing continuous monitoring, AI insights, and integrated workflows, organizations can turn vendor risk into a managed, measurable, and strategic advantage—building resilience for the years ahead.
Vendor Risk Assessment Solutions
Vendor risk assessment is a crucial element to any effective vendor risk management system. It ensures that your organization is aware of potential vendor-related threats that could disrupt your business operations, affect your brand reputation or financial stability, or undermine your compliance posture. Robust vendor risk assessment helps reduce the level of risk that your organization faces and protect your business from harm.
By integrating the right components, tools, methodologies, and best practices, you’ll be able to create a solid third-party vendor risk assessment program as part of a comprehensive risk management plan. Prioritizing vendor risk assessment builds business resilience and delivers confidence in business continuity.
Ready to address vendor risk? Contact Panorays to learn more.
Vendor Risk Assessment FAQs
-
Vendor due diligence and vendor risk assessment are closely related but serve different purposes. Due diligence is typically performed before onboarding a new vendor to verify their legitimacy, financial stability, and compliance posture. A vendor risk assessment, on the other hand, is an ongoing process that evaluates the vendor’s cybersecurity, operational, and compliance risks throughout the relationship. Together, they provide a complete picture of vendor reliability and security.
-
A vendor risk assessment should be conducted during onboarding, whenever there are significant changes to the vendor’s services, or following a major security incident. It’s also essential before contract renewals or when a vendor begins handling new types of sensitive data. Performing assessments at these key stages ensures that risk levels remain aligned with your organization’s tolerance and evolving business needs.
-
The frequency of reassessment depends on each vendor’s risk tier and criticality. High-risk or high-access vendors should be reviewed continuously or at least quarterly, supported by automated monitoring tools. Moderate-risk vendors may be reassessed annually, while low-risk vendors can follow a longer review cycle. Continuous monitoring through a platform like Panorays helps detect changes in vendor posture between formal assessments, ensuring that new threats are identified and addressed in real time.



