Third-Party Risk Management (TPRM) is the process of managing risks with third parties that are integrated into your business IT infrastructure, and an essential cybersecurity practice for businesses today.
5 Key Things You Need to Know About Third-Party Risk Management
1. Third-Party Risk Management is Essential for Modern Digital Ecosystems
With organizations relying on dozens (sometimes hundreds) of third-party vendors, TPRM serves to identify, assess, monitor, and mitigate risks across cybersecurity, compliance, financial, and reputational domains. It ensures business resilience, regulatory alignment, and protection from external vulnerabilities introduced through the vendor landscape.
2. Third-Party Risk Management Follows a Structured Five-Phase Lifecycle
The process includes 1) vendor due diligence & onboarding, 2) risk assessment, 3) remediation/mitigation, 4) continuous monitoring, and 5) vendor offboarding. Each phase is vital for maintaining a secure third‑party ecosystem and minimizing gaps throughout the entire vendor relationship lifecycle.
3. Real-World Breaches Highlight the Stakes in TPRM
High-profile incidents such as the Target breach via its HVAC vendor, the SolarWinds supply chain attack, and the Kaseya ransomware spread underscore how vendor vulnerabilities can directly undermine enterprise cybersecurity. These cases prove that third-party risks are now core business risks.
4. Ongoing Monitoring is Critical for Third-Party Risk Management
Vendor risk evolves over time. Panorays emphasizes continuous monitoring like scanning attack surfaces, validating compliance, and inventorying nth-party exposure to detect and respond to new risks in real time. This ongoing oversight prevents latent vulnerabilities from becoming active threats.
5. Advanced TPRM Platforms Provide Contextual Insights
Panorays’ platform integrates AI-driven assessments, external attack surface analysis, dynamic cybersecurity questionnaires, and remediation workflows, helping organizations manage vendor risk proactively and at scale. Contextual data and automation improve decision-making and reduce manual burden across security and compliance teams.
But what exactly is Third-Party Risk Management, and why is it so critical?
TPRM is the process of identifying, assessing, monitoring, and mitigating the cybersecurity and compliance risks that come from working with external vendors, suppliers, and service providers. As organizations increasingly rely on third parties for core functions, their digital ecosystems grow more complex, and more vulnerable. A single compromised vendor can have cascading consequences across the business, making managing third-party risk a critical priority for security and compliance teams. This is why organizations rely on a structured third-party risk management framework to control vendor risk across the entire relationship lifecycle.
To address this, mature TPRM programs follow a structured lifecycle consisting of five key phases: identification, assessment, risk mitigation, ongoing monitoring, and offboarding. In the sections ahead, we’ll walk through each phase in detail to help you build a more resilient third-party security strategy.
Why is Third-Party Risk Management Important?
Third-party risk management (TPRM) is the process an organization implements to manage risks that are a result of business relationships with third parties that are integrated into their IT environment and infrastructure.
These risks can be operational, cybersecurity, regulatory, financial, and reputational. According to a survey from Cyber Risk Alliance, the average organization uses 88 IT third parties (including software and service providers, partners, external contractors, agencies, suppliers, and vendors), and larger organizations can rely on nearly twice as many (175) third parties.
The stakes are rising. In 2023, 61% of companies experienced a third-party data breach or cybersecurity incident, a 49% year-over-year increase, highlighting how increasingly vulnerable these external relationships have become. Another study found that 41% of organizations experienced an impactful third-party breach in just the past year, underscoring the growing urgency of better risk management.
This pressure is compounded by intensifying regulatory scrutiny. In 2023, the EU’s NIS2 Directive expanded mandatory cybersecurity obligations to more sectors, while the Digital Operational Resilience Act (DORA) sets strict oversight rules for third-party ICT providers in finance. Regulations like GDPR, HIPAA, and PCI DSS also demand that companies ensure their vendors comply with data protection and security controls.
Ultimately, TPRM isn’t just about compliance, it’s a cornerstone of business resilience, brand protection, and operational continuity. A single third-party failure can expose sensitive data, halt operations, and erode trust. A mature TPRM program helps businesses minimize disruption, maintain regulatory readiness, and build long-term confidence with customers and stakeholders.
Real-World Case Studies: Third-Party Risk Management in Action
High-profile security incidents over the past decade have demonstrated the catastrophic consequences of poor third-party risk oversight. These cases serve as critical lessons for organizations building or refining their TPRM programs.
- Target (2013): Hackers infiltrated Target’s network by compromising credentials from an HVAC subcontractor. Once inside, they gained access to the company’s payment system, leading to the theft of 40 million credit and debit card records.
- SolarWinds (2020): A sophisticated supply chain attack inserted malicious code into SolarWinds’ Orion software, which was distributed to 18,000 customers, including U.S. government agencies and Fortune 500 companies.
- Kaseya (2021): REvil ransomware exploited a vulnerability in Kaseya’s remote monitoring software, impacting over 1,500 downstream businesses through its MSP clients.
Each of these incidents highlights a simple truth: a breach in your vendor ecosystem is a breach in your organization. Strong TPRM practices—like thorough onboarding due diligence, continuous monitoring, and clear contractual obligations—could have helped prevent or reduce the impact of these events.
The Most Common Third-Party Cyber Risks
Risk management technology can help your organization consolidate vendor information and conduct an ongoing third-party risk assessment of all your vendors, to help identify risk factors and evaluate each vendor’s inherent risk. Often, the technology determines the risk according to risk scores. After identifying the risk level that each vendor poses, a risk reduction strategy can be put into place according to your organization’s risk tolerance. This is the heart of third-party risk management.

Third-party risks include:
- Cybersecurity risk. A data breach, phishing scam, DDoS attack, or ransomware incident at a third party can cost your organization time and resources, halt operations, and significantly damage its reputation. The MOVEit breach in 2023 is a stark reminder: a vulnerability in a widely used file transfer tool led to widespread data exposure across both private and public sector organizations.
- Operational risk. If a third-party vendor provides a critical service or system and suffers a disruption, due to a natural disaster, political instability, or cyberattack, it can jeopardize your business continuity. The global Suez Canal blockage in 2021, for instance, triggered major supply chain delays, affecting companies dependent on real-time vendor fulfillment.
- Financial risk. Third-party financial risk can stem from mismanaged supply chains, pricing instability, or delayed service delivery. The COVID-19 pandemic exposed systemic vulnerabilities in supplier ecosystems, leading to inventory backlogs, cash flow issues, and missed revenue targets across industries like automotive, retail, and manufacturing.
- Strategic risk. Market changes, new acquisitions or mergers, and changing expectations of customers can make it difficult for all parties in the supply chain to align on business strategy. Strategic misalignment can quietly erode efficiency and responsiveness if not regularly assessed and realigned.
- Regulatory and Compliance risk. Industries governed by laws like HIPAA, PCI DSS, GDPR, CCPA, or EBA guidelines must ensure that their vendors are also compliant. In 2023, T-Mobile faced regulatory fallout when a third-party marketing partner was breached, exposing sensitive customer data and triggering international data privacy scrutiny.
- Geopolitical risk. Vendors operating in politically unstable regions can pose heightened risks due to sanctions, conflicts, or sudden policy shifts. The Russia–Ukraine war prompted many companies to re-evaluate and relocate critical vendor relationships to reduce exposure.
- Reputational risks. When a third party experiences a security incident or ethical failure, the ripple effects often land on your brand. Even if your systems remain secure, customers, partners, and regulators may hold your organization accountable for inadequate oversight. Reputational risk is uniquely difficult to contain; media coverage spreads quickly, customer trust is slow to rebuild, and long-term brand equity can take a serious hit.
Governance and Foundations of Third-Party Risk Management
Traditionally, TPRM has been the responsibility of the procurement or risk and compliance teams. For example, at one time a banking system had limited interaction with third parties. Perhaps a consultant would come in to evaluate specific programs or procedures, or a lawyer might examine internal processes to determine any legal risk. Only networks such as SWIFT, an international system for exchanging monetary transactions, were integrated into banking systems. But as software systems became more interdependent, each bank evolved a complex layer of third, fourth, and even fifth-party systems, which made robust third-party risk management a necessity.
As a result, a dedicated third-party risk professional is an essential part of today’s third-party risk management process, particularly in the banking and finance industries. This person is responsible for assessing and managing the third-party risks, with a wide range of responsibilities such as collecting information from third parties, assessing their ability to manage compliance, prioritizing third-party risks, creating and sending questionnaires to third parties, and overseeing legal contracts such as SLAs to mitigate any legal risks to the organization.
Ownership of TPRM varies across organizations, but it is increasingly shared between risk, compliance, IT, procurement, and security functions. Clear governance structures are necessary to define who is accountable for different phases of the third-party lifecycle—from onboarding and due diligence to ongoing monitoring and eventual offboarding. A mature TPRM program also requires a structured policy, including criteria for risk classification, documentation standards, escalation procedures, breach response plans, and periodic reassessments.
Because third-party decisions often involve legal, technical, and strategic considerations, cross-functional collaboration is critical. IT and cybersecurity teams assess the technical footprint and attack surface of vendors; procurement evaluates service quality and cost; legal teams ensure contract language includes appropriate liability and data protection clauses; and compliance tracks regulatory alignment. All of this requires orchestration—often led by a TPRM manager or steering committee.
Lastly, executive and board-level engagement is no longer optional. As regulators worldwide impose stricter rules on supply chain accountability (via GDPR, DORA, NIS2, etc.), and as reputational risks mount, TPRM must be recognized as a boardroom priority. Regular reporting, oversight committees, and integration with enterprise risk management frameworks help ensure alignment with the organization’s broader risk posture and strategic objectives.
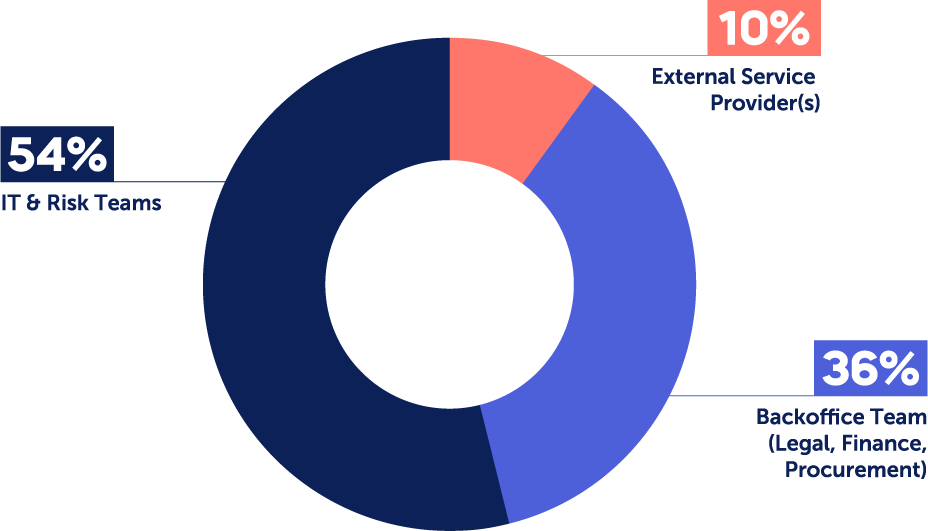
A recent Panorays survey on third-party risk management priorities found that:
- In more than half of cases (54%), the responsibility for managing third party risks falls to dedicated IT and Risk teams who have specific technology expertise. These include Operations and Logistics teams, Compliance and Privacy, Information Security, Risk Management, and Technology or IT.
- In 36% of cases, the Back Office Team is in charge, which includes Legal, Finance and Procurement. This may include tasks like managing cyber questionnaires, onboarding third parties to internal systems, or handling payments.
- While 10% outsource third-party cyber risk management to external service providers, this is predominantly the case in enterprises with under 5k employees.
Best Practices and Framework for TPRM
Third-party risk professionals have a heavy burden in today’s risk-fraught landscape. The process of managing third-party risks involves a number of individual steps, each of which has an important role in enabling you to minimize the threats that face your organization. These steps include:
- Mapping your vendor ecosystem to identify all third-party access
- Assessing potential third-party risks based on a range of factors
- Categorizing and prioritizing risks to focus your resources on the most urgent needs
- Ensuring compliance to relevant regulations and standards
- Preparing incident response plans to manage breaches or incidents that arise
Identifying Third Parties
Mapping your supply chain is a prerequisite to successful third-party risk management. You have to know which companies populate your vendor landscape, otherwise you’re flying blind. Each third party represents a potential source for vulnerabilities, cyber attacks, and business disruptions, so you need visibility into which vendors, service providers, and contractors have access to your sensitive data and/or critical systems.
Your vendor inventory should also be updated regularly so that it reflects the current risk landscape. Only then can you move on to evaluate risk levels, enforce compliance, and resolve vulnerabilities.
Assessing Third-Party Risk
The next step is to evaluate all potential third-party risks, so that you can assess which vulnerabilities could be introduced and the level of damage they might cause to your organization. Reviewing vendor risk levels allows you to identify weaknesses and take steps to resolve them.
Risk assessments involve carefully considering a whole range of factors, including your vendor’s security protocols, financial stability, resilience, and exposure to geopolitical disruption; their level of access to your sensitive data and systems; and your own ability to contain and resolve the threats that may arise.
Risk Categorization and Prioritization
Categorizing and prioritizing risks is another crucial step in third-party risk management, and part of the process of assessing and addressing risks. Risks should be categorized according to a number of concerns, including the sensitivity of the data that each vendor accesses, the vendor’s security posture, and how critical their services are to your business continuity.
This enables you to direct your resources towards the most significant threats first, reducing the chances of a serious incident that causes significant harm to your organization. High-risk vendors will receive more rigorous scrutiny and mitigation measures, and you won’t waste resources on low-risk vendors that don’t need the same level of attention.
Ensure Regulatory Compliance
The regulatory burden keeps rising, especially if you’re in a critical industry like finance or health. Many regulations include third-party risk management as part of your own compliance requirements, so it’s vital to build in processes for measuring and monitoring third-party compliance.
Ensuring regulatory compliance with laws like GDPR, HIPAA, or PCI DSS helps you avoid legal penalties, financial losses, and reputational damage. It demonstrates due diligence and corporate responsibility, while also helping reveal gaps in third-party practices that could lead to breaches or serious security incidents.
Incident Response Planning
Last but not least, every third-party risk management strategy needs to include incident response planning. It’s almost inevitable that you’ll encounter some type of third-party incident, so you need to be ready to identify, contain, and remediate issues as fast as possible to minimize damage. Incident response planning is also mandated by many regulations.
Defining response tactics, communication protocols, roles and responsibilities, and vendor coordination ahead of time enables you to respond more quickly when an incident occurs. This helps you to maintain business continuity, protect sensitive data, and reduce recovery time and costs.
Common Third-Party Risk Management Lifecycle Phases
Third-party risk management is a multi-step process that covers a number of different tasks, from an initial risk survey to ongoing methods for continuous visibility into changing risk levels.
Common TPRM lifecycle phases include:
- Carrying out due diligence to evaluate vendor weaknesses
- Conducting comprehensive vendor risk assessment
- Onboarding new vendors in a structured way
- Taking steps to remediate and mitigate third-party risks
- Establishing continuous monitoring for ongoing risk management
TPRM Phase 1: Due Diligence and Vendor Onboarding
Third-party risk management begins well before a vendor joins your network. Due diligence is a thorough evaluation of a vendor’s operational and cybersecurity posture, financial health, legal standing, and historical compliance. The goal is to spot major vulnerabilities before they enter your ecosystem and determine how to work with them responsibly.
This process includes reviewing security documentation (e.g., SOC 2, ISO 27001), financial reports, insurance coverage, and regulatory history. You may also conduct background checks, reference calls, and external audits. An often-overlooked but critical part of onboarding is setting security and compliance expectations from the outset, including data handling procedures and breach notification timelines.
Onboarding is the formalization of this relationship, including the execution of contracts that clearly define service-level agreements (SLAs), data protection requirements, regulatory compliance obligations (e.g., GDPR, HIPAA), and incident response plans. Vendors should only gain access to systems and data once contractual and technical controls are in place.
A well-designed onboarding process minimizes risk and lays the groundwork for a secure, resilient, and accountable relationship.
TPRM Phase 2: Vendor Risk Assessment
Once due diligence is complete, a more systematic and risk-based evaluation follows. The vendor risk assessment phase identifies potential threats the third party could pose to your organization’s data, systems, operations, and compliance status.
A critical part of this process is categorizing vendors based on risk exposure. High-risk vendors typically handle sensitive data, have deep systems integration, or support mission-critical services. Lower-risk vendors may provide peripheral or commodity services with minimal access to sensitive assets.
To assess vendor risk effectively, many organizations use standard frameworks such as ISO 27036, which focuses on ICT supply chain security, or NIST SP 800-161, which guides supply chain risk management for federal information systems.
Practical tools include:
- Security questionnaires (e.g., SIG – Standardized Information Gathering, CAIQ – Cloud Security Alliance’s Consensus Assessments, or custom checklists).
- On-site audits or third-party rating services
- Regulatory compliance mapping to ensure vendors meet requirements relevant to your business or region.
These tools help quantify risks and support informed decisions on which controls to apply or escalate.
TPRM Phase 3: Risk Remediation and Mitigation
Once risk levels are clear, the next step is to take action. Risk remediation involves working directly with vendors to address specific gaps—such as outdated software, missing controls, or incomplete policies. Rather than rejecting a vendor outright, it’s often more productive to collaborate on resolving issues, especially when the vendor plays a critical role in your operations.
Setting remediation deadlines is key for accountability. High-risk issues should have short timeframes (e.g., 30–60 days), while medium- or low-risk findings may be addressed over longer periods or accepted with compensating controls.
Contracts can include enforceable technical safeguards such as:
- Multi-factor authentication (MFA)
- Encryption for data at rest and in transit
- Endpoint protection and patch management
- Defined breach notification procedures
Mitigation, on the other hand, refers to reducing the likelihood or impact of risks that cannot be fully remediated. This may involve isolating a vendor’s access, implementing read-only permissions, or establishing contingency plans.
A collaborative, non-punitive approach improves vendor relationships and encourages continuous security maturity across your supply chain.
TPRM Phase 4: Continuous Monitoring and Ongoing Risk Management
Risk doesn’t end after onboarding—it evolves. Vendors may introduce new services, undergo acquisitions, change data processing practices, or fall out of compliance. That’s why continuous monitoring is critical to any TPRM program.
Monitoring methods include:
- Automated security ratings and alerts from platforms like Panorays
- Periodic reassessments and audits at defined intervals (e.g., annually or semi-annually)
- Review of incident reports and vendor disclosures
- Quarterly or annual meetings with strategic vendors to discuss security posture
You should also account for fourth-party risk, the vendors your vendors rely on. Mapping subcontractor dependencies during onboarding helps maintain visibility throughout the extended supply chain. Some organizations require primary vendors to disclose all material sub-processors and subcontractors and include flow-down obligations in contracts.
A strong continuous monitoring program ensures your organization can detect and respond to new risks quickly, before they become breaches.
TPRM Phase 5: Vendor Offboarding & Contract Termination
Vendor offboarding is a critical yet often underestimated phase in the third-party risk management lifecycle. When not handled correctly, the termination of a vendor relationship can leave behind serious security vulnerabilities. Unrevoked access credentials, unmanaged data remnants, and poor internal communication can all lead to ongoing exposure well after the partnership ends.
A secure offboarding process begins with systematically revoking all forms of access, including user credentials, VPN permissions, and API keys. Any company-owned data in the vendor’s possession should be returned or permanently deleted in accordance with contractual obligations. It’s also essential to update your internal systems, particularly your vendor risk inventory, to reflect the termination and prevent the vendor from appearing as an active partner in audits or compliance checks.
Equally important is communicating the offboarding to relevant internal teams such as IT, security, legal, and finance. Each team has a role to play in ensuring that assets are accounted for, liabilities are closed out, and no lingering risks remain. Reviewing the terms of the original contract helps ensure compliance with legal obligations during the termination process, such as notice periods or data retention rules.
By treating offboarding with the same diligence as onboarding, organizations can close the loop on vendor relationships securely and protect themselves from residual third-party risk.
What is an Example of Third-Party Risk Management?
For example, imagine a non-profit organization that runs global education initiatives. We’ll call it the HopeWell Foundation. The HopeWell Foundation relies on third-party vendors to manage donor databases, process donations, and run virtual fundraising campaigns.
These vendors do a great job, allowing the Foundation to focus on its core activities, but they also open the Foundation up to a number of risks. Those third-party risks include:
- Data breaches: Exposing sensitive donor information, such as personal details and payment data.
- Vendor non-compliance: Failure to adhere to GDPR, HIPAA, or other regulatory requirements.
- Operational downtime: Disruptions in fundraising activities due to vendor system failures.
Here’s what the HopeWell Foundation did to ensure effective TPRM and minimize those risks.
Steps Taken for TPRM
First, the Foundation carried out a thorough due diligence before onboarding vendors. This includes a vendor assessment, where they requested security certifications such as SOC 2 Type II reports and ISO 27001 compliance, and carried out background checks to assess vendors’ reputation and past performance.
Then they took risk mitigation measures, ensuring that the vendor encrypts all donor data both at rest and in transit, and confirming that vendors meet GDPR, HIPAA, and local regulations for handling sensitive data. They also checked that the vendor has robust incident response and breach notification processes, and made sure that the vendor contract includes clauses about incident response and reporting timelines.
Finally, they set up processes to continue to manage risks through ongoing monitoring. The Foundation reviews vendor performance metrics and compliance reports every quarter, and regularly runs vulnerability assessments and penetration tests on vendor systems. It also uses TPRM software to monitor vendor compliance with regulations.
Outcome of TPRM
Thanks to its TPRM activities, the HopeWell Foundation succeeded in minimizing the risk of data breaches and operational disruptions. It protected donor data, demonstrated adherence to GDPR and HIPAA regulations, and reduced its legal and financial liabilities, which enhanced trust with stakeholders while safeguarding the organization’s reputation.
This example shows how a proactive approach to TPRM ensures operational stability and defends an organization’s reputation. By integrating TPRM into its risk management strategy, HopeWell Foundation not only protected sensitive donor data but also strengthened its ability to fulfill its mission without interruptions, reinforcing stakeholder confidence and long-term sustainability.
What We Saw in TPRM in 2025
Let’s take a quick look at a few of the trends we saw this past year.
1. Supply chain attacks and third-party breaches continued to rise
2025 reinforced a hard truth: attackers increasingly target the weakest link in the supply chain. High-profile incidents such as the Polyfill.io supply chain compromise, third-party exposures impacting platforms like Discord, and breaches affecting identity and access providers highlighted how a single vendor failure can cascade across thousands of organizations.
Beyond sophisticated attacks, operational missteps and configuration errors by third parties continued to disrupt business operations. These incidents underscored the growing need for visibility not only into direct vendors, but also into fourth, fifth, and Nth parties embedded deeper in the digital supply chain.
2. Third-party ecosystems expanded attack surfaces
Organizations continued to integrate more third-party technologies into core operations, including cloud services, SaaS platforms, IoT devices, and remote access tools. At the same time, remote and hybrid work environments increased reliance on unmanaged devices and external networks.
As supply chains expanded to include more Nth parties, cybercriminals gained additional entry points. Many downstream vendors still lack mature security programs, making advanced TPRM platforms essential for identifying, mapping, and monitoring risks beyond direct contractual relationships.
3. Regulatory compliance became a greater operational burden
2025 marked a turning point as several major regulations moved from preparation to enforcement. Organizations faced increased scrutiny under frameworks such as the EU’s NIS2 Directive, the Cyber Resilience Act (CRA), and evolving national cybersecurity strategies across the US, EU, and APAC regions.
These regulations elevated third-party risk from a security concern to a board-level compliance priority. As a result, organizations increasingly embedded regulatory requirements directly into their TPRM strategies, contracts, and continuous monitoring programs.
4. Vendor criticality gained renewed importance
As vendor ecosystems grew more complex, organizations recognized that not all vendors carry the same level of risk. Understanding vendor criticality became essential for prioritizing assessments, monitoring efforts, and remediation.
By classifying vendors based on business impact, access level, and data sensitivity, organizations were better positioned to focus resources where risk exposure was highest and to coordinate remediation efforts across supply chain partners more effectively.
TPRM Trends to Expect in 2026
Looking ahead, several trends will shape how third-party risk and security teams operate in 2026 and how they communicate risk to the business.
1. Accelerated adoption of artificial intelligence in TPRM
AI will continue to play a dual role in third-party risk management. On one hand, AI-driven TPRM platforms are enabling organizations to scale programs by improving the accuracy and speed of risk assessments.
Key use cases include:
- Automating and validating responses to security questionnaires
- Mapping digital supply chains and identifying fourth, fifth, and Nth parties
- Prioritizing known exploited vulnerabilities (KEVs), common exposure vectors (CEVs), and contextual risks based on vendor criticality
At the same time, third-party use of AI introduces new risks:
- Data privacy and control: Vendors may use sensitive customer data, source code, or intellectual property to train AI models, increasing the risk of data leakage.
- Trust and reputational risk: AI bias, misinformation, and hallucinations can result in inaccurate outputs that damage customer trust.
- Security abuse: Threat actors increasingly use AI to generate convincing phishing campaigns, automate polymorphic attacks, and exploit prompt injection or indirect data poisoning techniques.
- Supply chain opacity: As vendors adopt AI tools, new Nth-party relationships often emerge without clear visibility, complicating compliance and risk tracking.
In 2026, organizations will need stronger AI governance requirements for vendors, clearer contractual controls, and continuous monitoring of AI-related risks.
2. Stronger emphasis on cloud-first and shared responsibility risks
Cloud adoption will continue to accelerate, but many organizations will struggle with the shared responsibility model. While cloud service providers secure underlying infrastructure, vendors and customers remain responsible for configurations, access controls, and data protection.
When organizations outsource services to SaaS providers that rely on cloud platforms such as AWS, Azure, or GCP, assumptions about security controls can create dangerous gaps. Misconfigurations, excessive permissions, and insecure integrations remain common causes of third-party data exposure.
In 2026, effective TPRM programs will place greater emphasis on:
- Auditing vendor cloud configurations and access controls
- Enforcing least privilege access and network segmentation
- Clearly defining cloud security responsibilities in vendor contracts
Even with strong controls in place, human error remains a risk. Continuous monitoring and validation will be critical to minimizing cloud-related third-party exposure.
3. Increased regulatory focus on outsourcing and third-party cyber risk
Regulators are placing greater accountability on organizations for the cyber risks introduced through outsourcing. In 2026, enforcement activity is expected to intensify across several major frameworks, including:
- DORA: Fully enforced across the EU financial sector, requiring continuous third-party risk assessments, ICT asset mapping, and documented remediation plans.
- NYDFS 23 NYCRR 500: Updated requirements emphasize stronger vendor oversight, encryption, MFA, and faster incident reporting for organizations handling non-public sensitive data.
- NIS2 Directive: Expands coverage across industries and strengthens requirements for supply chain risk management, incident reporting, and vendor accountability.
AI regulation is also maturing. The EU AI Act is now moving into phased enforcement, placing clear obligations on organizations that deploy or rely on high-risk AI systems, including those provided by third parties. Additional AI governance frameworks are emerging globally, requiring transparency, risk assessments, and ongoing oversight of AI-enabled vendors.
In 2026, organizations that proactively integrate regulatory compliance into their TPRM programs, rather than treating it as a separate initiative, will be better positioned to manage both security and compliance risk.
The Benefits of Third Party Risk Management Framework
You can conduct third-party security risk management using an internal team, or by working with a third-party security risk management specialist. Either way, you’ll need to spend time and money and implement new business processes to improve your risk profile. Either way, investing in third-party risk management offers a number of benefits.
They include:
- Cost reduction. Think of a third-party risk management program as an investment, not an expense. Even though it will cost you some time and money upfront, you stand to save money in the long run. A data breach could cost your company thousands if not millions of dollars, but an effective third-party cybersecurity risk management strategy could prevent you from ever facing this scenario.
- Regulatory compliance. You’re legally required to meet industry regulations, which include components of TPRM. Whether or not you implement TPRM directly or outsource it to an external party, you are still bound by these regulations. This is particularly true for industries that deal with customer data.
- Knowledge and confidence. Third-party risk management increases your knowledge and visibility of the third-party vendors with whom you’re working. The more confident you are in your network of vendors and partners, the more you’ll be able to work without pausing to look over your shoulder.
- Risk reduction. Continuous third-party risk management is instrumental in order to tier your third parties properly and gain better insight into risk posed by fourth parties. When new vulnerabilities and data breaches are discovered, you’ll have the context to prioritize them effectively.
Why CISOs are Choosing to Invest in TPRM
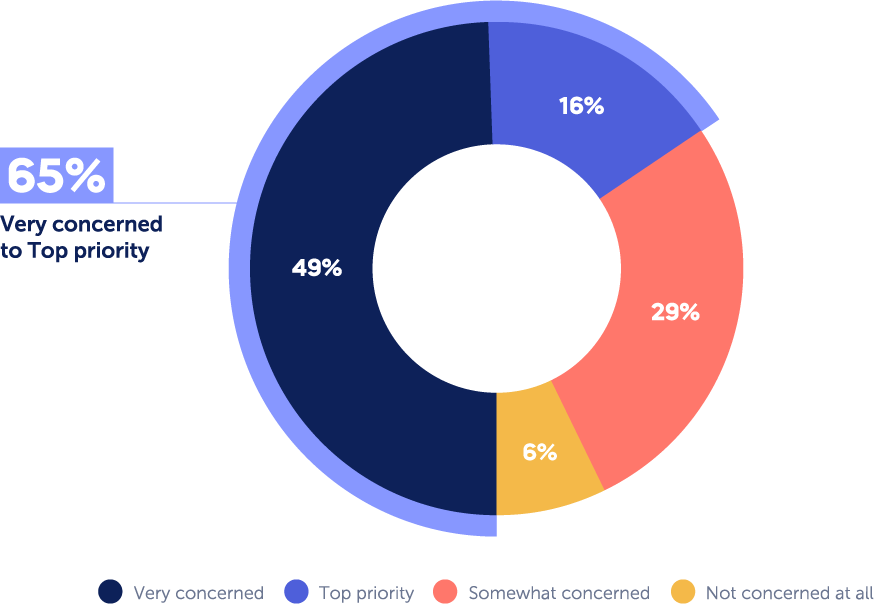
A recent survey conducted by Panorays found that the vast majority – 94% of CISOs are concerned about third-party cybersecurity attacks; and 16% rate it as their top priority. The level of concern may depend on different factors, such as the size of the organization, how reliant it is on third parties for critical services, and the need for it to adhere to various regulations.
As a basic rule of thumb, the larger the enterprise, the more concerned it is about third-party attacks, due to the potential risk and consequence of a third-party breach.
No Silver Bullet in Terms of Third-Party Tools
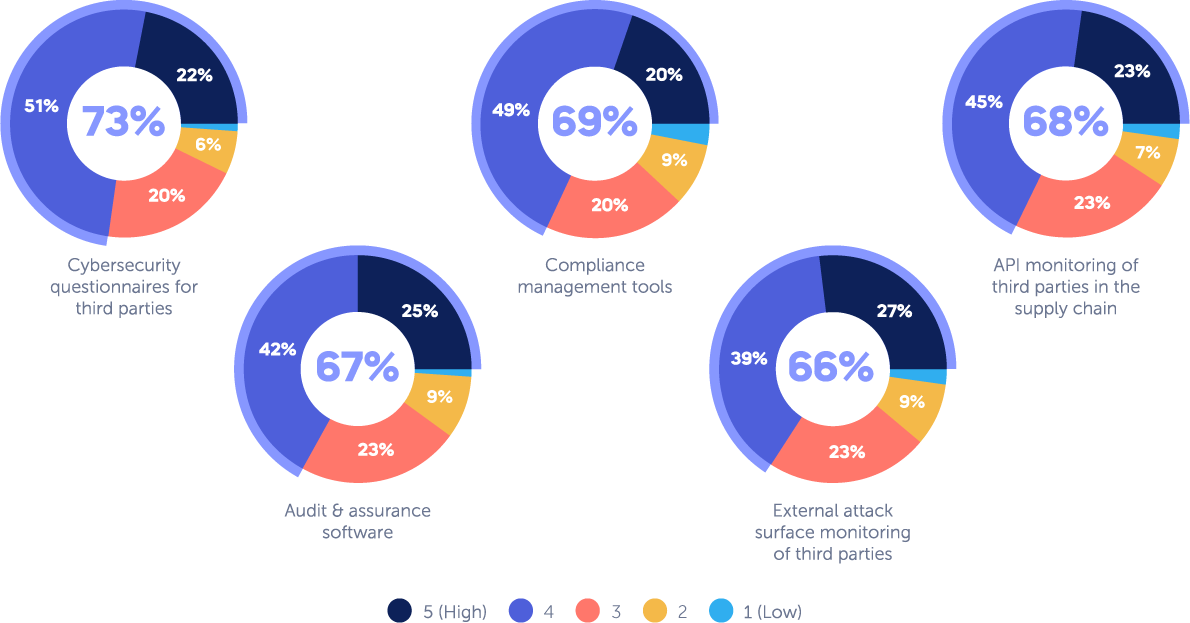
CISOs realize that combining multiple tools is the key to success when building a third-party risk management program. Although CISOs have slightly different opinions as to the effectiveness of different tools, they agree on the importance of a few main ones.
Nearly 73% found cybersecurity questionnaires to be effective; 69% compliance management tools; 68% compliance management; 67% audit and assurance software and 66% external attack surface monitoring of third parties.
How to Measure and Improve Your TPRM Program
Establishing a third-party risk management program is only the beginning. To ensure its effectiveness and maturity over time, organizations need a clear framework for measuring performance and identifying areas for improvement. This starts with setting relevant KPIs that reflect both the operational health and strategic impact of your TPRM efforts.
Common metrics include the percentage of vendors assessed versus the total number of third parties, which reveals coverage gaps in your risk process. You should also track the average time to remediate identified vendor risks, a critical indicator of responsiveness and coordination across internal teams. Additionally, monitoring the number and severity of third-party-related security incidents over time helps measure risk reduction and justify continued investment.
Beyond metrics, a strong TPRM program incorporates an ongoing feedback loop. Conducting annual policy reviews ensures your risk approach evolves alongside new technologies, regulations, and threats. Benchmarking your program against industry frameworks, such as NIST, ISO 27036, or SIG maturity models, can help identify blind spots and set goals.
Budgeting is another core consideration. As risk exposure grows, demonstrating measurable improvements and reduced incident frequency strengthens the case for continued or expanded investment. Mature TPRM programs allocate resources for platform upgrades, process automation, and staff training to ensure they stay ahead of evolving third-party threats.
What to Consider When Selecting a TPRM Platform
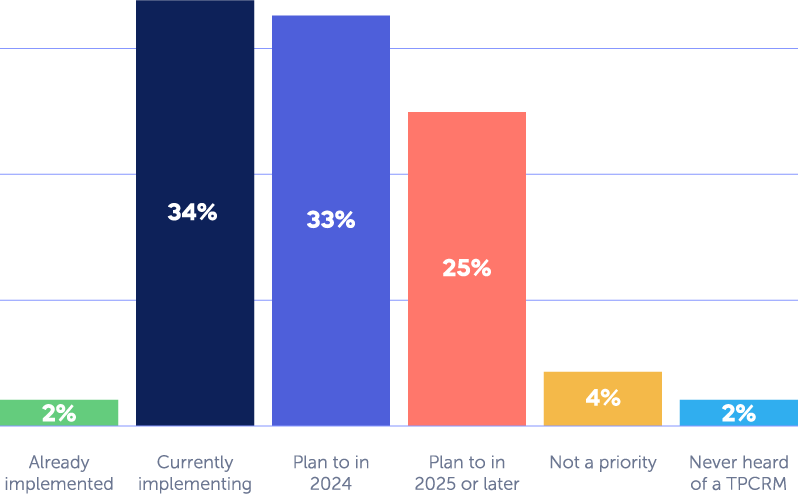
According to a recent Panorays survey, 65% of CISOs have increased their budget for third-party risk management, and 92% of them are allocating these resources to implementing a designated solution for third-party threats. But how can they ensure that they spend that budget efficiently?
When considering a TPRM platform, there are a number of features and functionalities to look for:
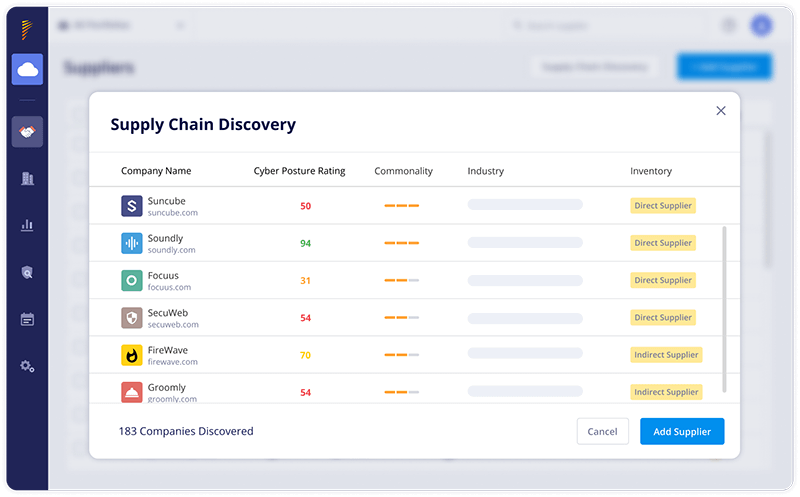
- Mapping of the supply chain. Many organizations aren’t even aware of how many third parties they use, let alone the types of critical services they provide. Profile each vendor, grouping them with similar vendors. It should list what service they provide, the criticality of that service, the types of data they are handling, their access to sensitive data, and the internal contact managing the vendor. This will help you determine which questionnaires to send out to your vendors, according to your regulatory requirements and risk appetite.
- Scalability. With enterprise-level companies relying on as many as 175 third parties, it’s important to have minimal friction when dealing with suppliers. This reduces time spent on security assessments and helps resolve issues quickly. Automated and customized security questionnaires and external cyber posture assessments streamline the work, with targeted questions that apply only to the specific third party and its relationship with you.
- Attack surface assessment. An external assessment can provide a picture of the third party’s exterior attack surface. Your platform should perform regular third-party risk assessments to identify weaknesses and vulnerabilities inherent within vendor IT networks, applications and human layer.
- Continuous monitoring. Hackers are constantly developing new methods to exploit vulnerabilities and engage in cyberattacks. In addition, suppliers add new assets and software and change or update their internal policies, resulting in new cyber gaps. With continuous monitoring, your organization receives real-time data that enables a more proactive approach by uncovering issues, detecting suspicious activity and staying updated about security policy changes.
- Remediation. The right tools can provide third parties with remediation or mitigation plans, along with visibility about how you identified these cybersecurity gaps. You should set realistic deadlines and provide an intuitive method for communication. In short, you and your third party should establish a collaborative business relationship.
How Panorays Supports a Modern Third-Party Risk Management Framework
Panorays is the only third-party cyber management solution that delivers contextual third-party risk management. By mapping your full threat landscape and continuously monitoring and reassessing the Risk DNA of each business connection, it pinpoints early threat indications within the unique business context of every relationship, enabling companies to adapt their defenses, minimize risk and proactively prevent the next breach from affecting their business.
The platform includes:
- AI-powered cybersecurity questionnaires. Unlike cumbersome security questionnaires that can take days or weeks to complete, AI-powered cybersecurity questionnaires streamline third-party risk management and can be completed in minutes. On the supplier’s end, AI assists in generating answers based on questionnaires conducted in the past. On the evaluator’s end, AI assists in evaluating the accuracy of responses by validating them with internal documents from both the organization and vendor.
- Extended attack surface assessments. These assessments start with first identifying and mapping third, fourth, fifth and n-th party relationships, identifying risk and prioritizing it according to the level of criticality, so that organizations gain deeper visibility into the digital supply chain.
- Risk DNA Assessments. Assess the cybersecurity posture of your third parties with AI-based accuracy, taking into account the dynamic nature of every relationship. Risk DNA evolves to reflect changes that impact your third-party risk, including shifts in data access and severity, changes in business criticality, and developing vulnerabilities.
- Continuous monitoring. Conduct attack surface assessments and send vendors cybersecurity questionnaires when necessary, such as when a change is made in your organization, the vendor’s IT infrastructure, or industry regulations.
- Automatic discovery of third, fourth, and n-th party vendors. Panorays automatically maps third, fourth and Nth party vendors to understand the business relationship between them and your organization. Then it ranks them according to their level of criticality.
- Evaluation of compliance. Verify whether your suppliers are meeting compliance requirements, and continuously monitor for new issues in regulations and standards such as GDPR, NDFS and PCI DSS. Replace clunky spreadsheets with efficient frameworks to document process-oriented regulations such as the OCC and EBA.
- Customized remediation. After sending cybersecurity questionnaires and identifying cyber gaps that need to be addressed, vendors and organizations can collaborate using a detailed plan to remediate risk, customized according to each organization’s specific risk appetite.
Want to learn more about managing third-party risk across your extended attack surface? Get a demo of our third-party risk management platform today.
Third Party Risk Management FAQs
-
Third-party risk management is a process designed to review third parties for their current security practices, their role in your organization, and their overall sustainability. It includes the controls put in place to minimize operational, financial, reputational, financial and cybersecurity risks posed to your organization.
-
The five steps essential to third-party risk management are:
- Analysis. Identify the inherent risk of the relationship of the vendor and the level of due diligence to be performed.
- Engagement. Collaborates with the third party to remediate security gaps.
- Remediation. The vendor or third party fixes the security gap.
- Approval. Approved or rejected the third party based on your organization’s tolerance for risk.
- Ongoing Monitoring. Conduct continuous monitoring to detect any cyber gaps of the third party.
-
Third-party frameworks are sets of controls used to manage relationships with third parties. An example is the NIST CF or the National Institute of Standards Cybersecurity Framework, a voluntary set of standards used by organizations across industries, of all sizes, to strengthen their cybersecurity programs.
-
Third-party risk management is important because third party risks have increased as more organizations rely increasingly on third parties for their operations and business growth. Recent supply chain attacks such as the MoveIt and Applied Materials attacks have highlighted the need to apply resources to TPRM.
Traditionally, TPRM has been the responsibility of the procurement or risk and compliance teams. For example, at one time a banking system had limited interaction with third parties.
Perhaps a consultant would come in to evaluate specific programs or procedures, or a lawyer might examine internal processes to determine any legal risk. Only networks such as SWIFT, an international system for exchanging monetary transactions, were integrated into banking systems. But as software systems became more interdependent, each bank evolved a complex layer of third, fourth, and even fifth-party systems, which made robust third-party risk management a necessity.
-
Third-party cyber risk management focuses on cyber risks with capabilities such as threat intelligence, ongoing monitoring, breach remediation, etc and is catered towards CISO, third-party risk management and security and compliance teams.
-
The difference between TPRM and TPCRM is that TPRM, or third-party risk management, focuses on the full range of third-party risks such as financial, legal, cyber, reputational, strategic, operational and geopolitical. TPCRM, or third-party cyber risk management, focuses specifically on managing cyber risks.